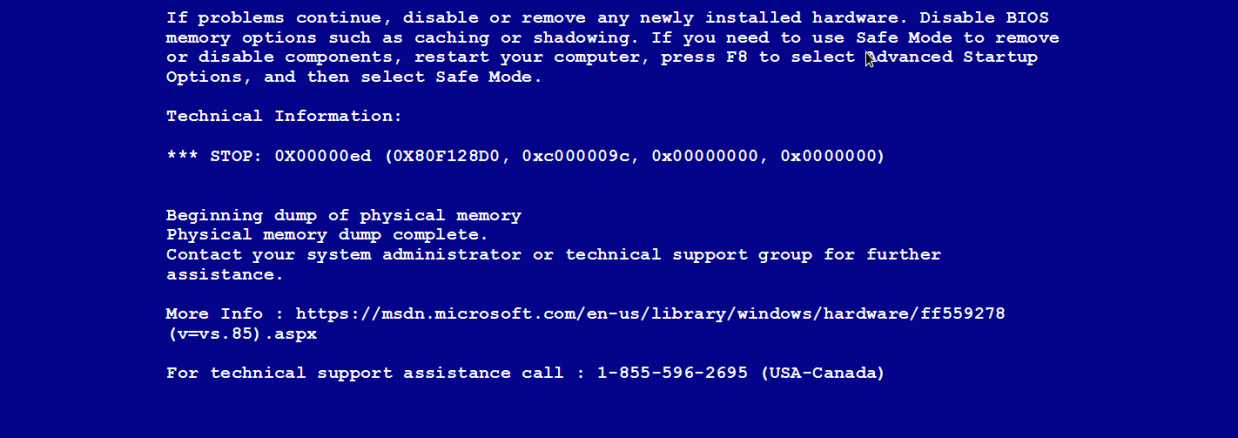
Many Windows users are familiar with the dreaded Blue Screen of Death (AKA BSOD), which usually happens when the system crashes.
The BSOD can occur for many reasons, for example when there is a memory access violation. To the end user, it usually means that they have lost all their work and that Windows might not be happy the next time it reboots.
It is also a rather scary screen (at least up until Windows 8) and that is exactly what tech support scammers are capitalizing on to trick potential victims into calling for immediate assistance.
The fake browser BSOD
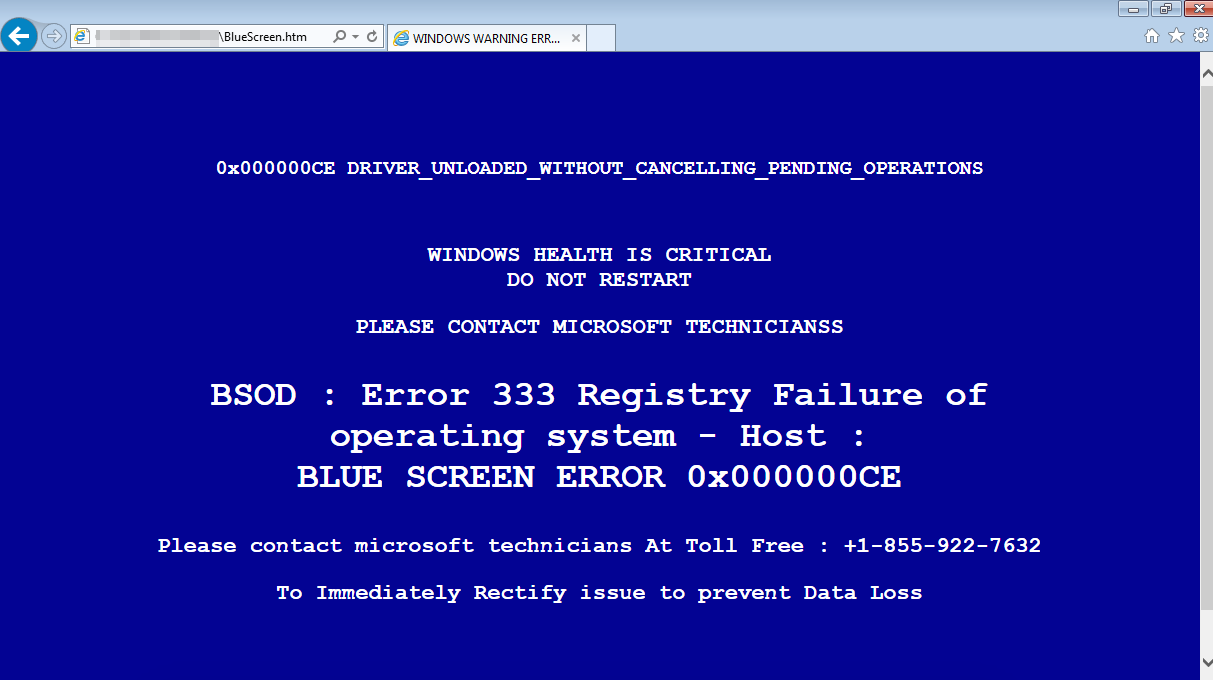
We documented the use of scare pages before and the BSOD theme was a natural fit. Miscreants even register the websites with very explicit names and launch them via by rogue affiliates or black hat advertisers.
It’s all about scare tactics to get people to call in for support.
- http://bluescreenalert.com/
- http://bluescreenerrors.net/
The template for those pages is quite straightforward with only a few lines of HTML code:
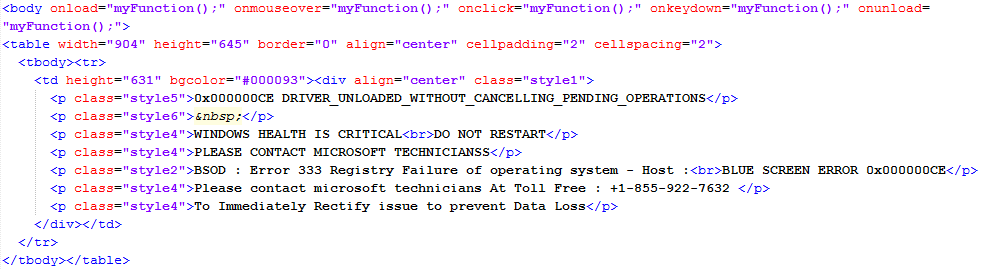
Those scare pages are also quite effective and particularly annoying to get rid of thanks to the use of JavaScript code to pop an alert ad infinitum.
The fake malware BSOD
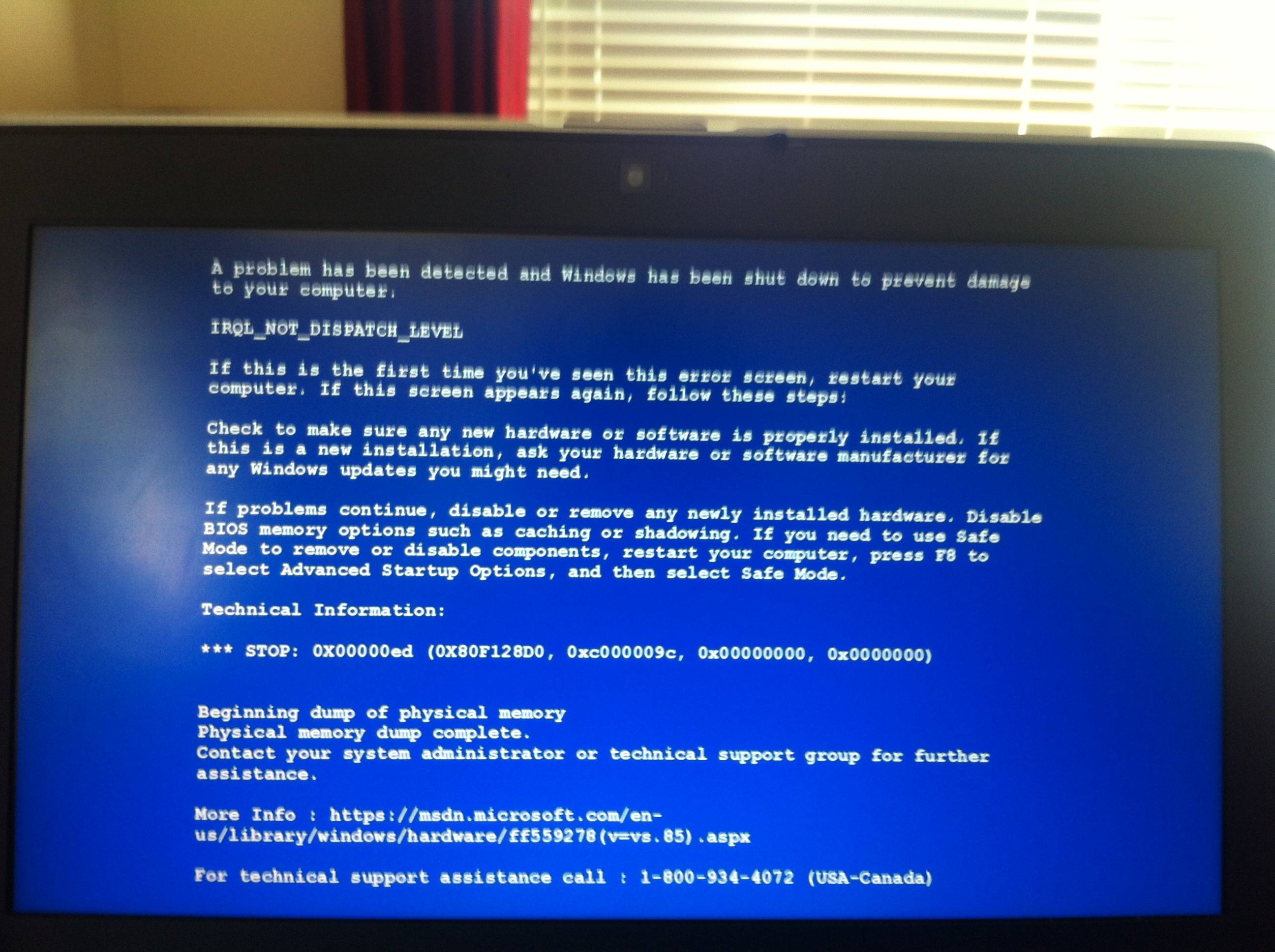
Tech support scammers had another trick up their sleeve and in a case first reported in the BleepingComputer forums, essentially built a piece of malware to create an almost genuine BSOD.
As you can see in below, there is no browser window and the BSOD is displayed in full screen. More annoying is the fact that this ‘hijack’ happens at regular intervals.
We dug for the initial installer that lead to this ‘infection’. Not too surprisingly, it started from a PUP (thanks Rich Matteo for identifying it):
which drops a digitally signed executable (SenseIUpdater.exe) manufactured by Fidelis IT Solutions Private Limited. It is worth noting that this happens when the PUP is ran, but before clicking on the Next ‘I agree’ button.
C:Users%userprofile%AppDataRoamingSenseIUpdater
This is a rather basic but yet interesting piece of scareware whose purpose is to create a more persistent way of nagging users by using malware-like techniques.
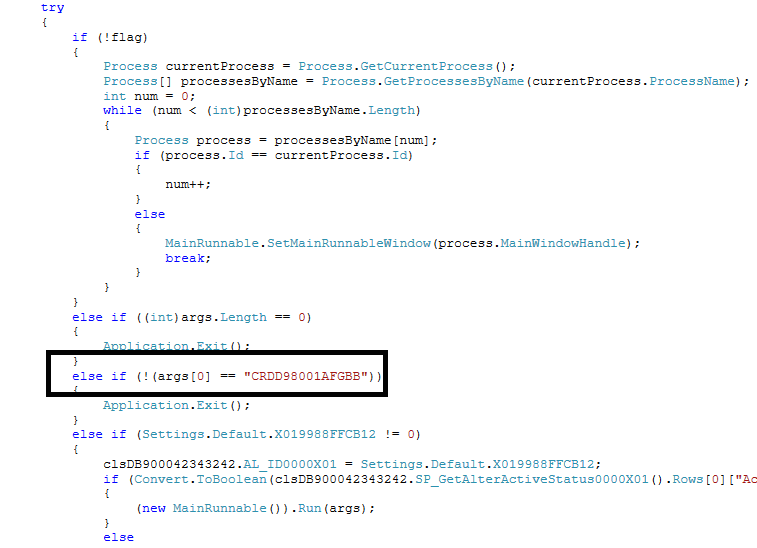
First, the sample will not do its payload unless a special argument (pictured below) is passed to it, which is most likely a (weak) attempt to appear benign when analyzed in a sandbox.
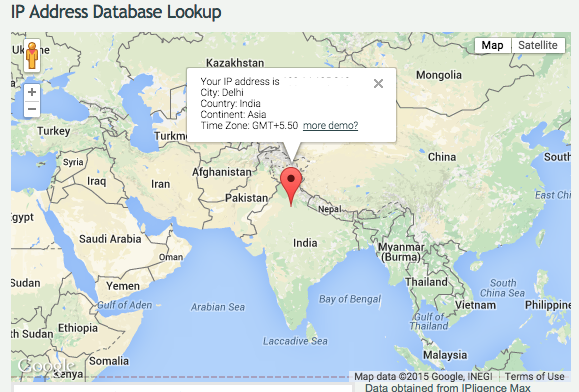
If the right argument is passed, we move to the next phase where the malware checks the system for various pieces of information such as IP address, country, city, etc:
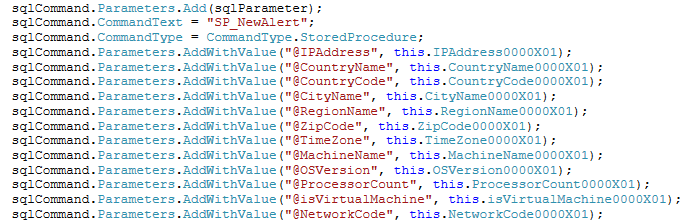
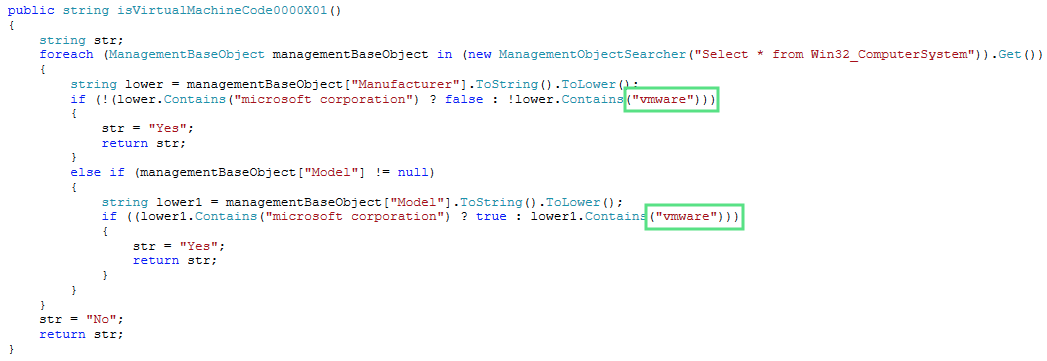
We note the detection of Virtual Machines so that if the file is ran in VMware, it will simply exit without doing its true payload.
Then, the harvested data is sent to a remote database – credentials are hardcoded inside the binary (poor opsec) – as well as stored in a local configuration file:
The sample then installs the hook point by adding a task in the TaskScheduler so that it can run in the future even if the computer is rebooted:
This allows the piece of malware to communicate with the command and control server at regular intervals and determines whether it should display the fake BSOD or not.
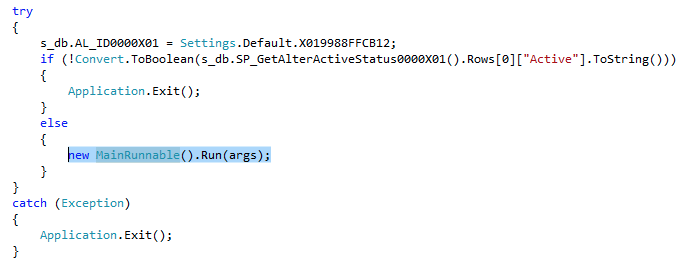
The BSOD itself is created with the following code:
Some elements of the page are dynamic, in particular the toll free phone number, which allows the crooks to update it whenever they need to. Finally, the BSOD:
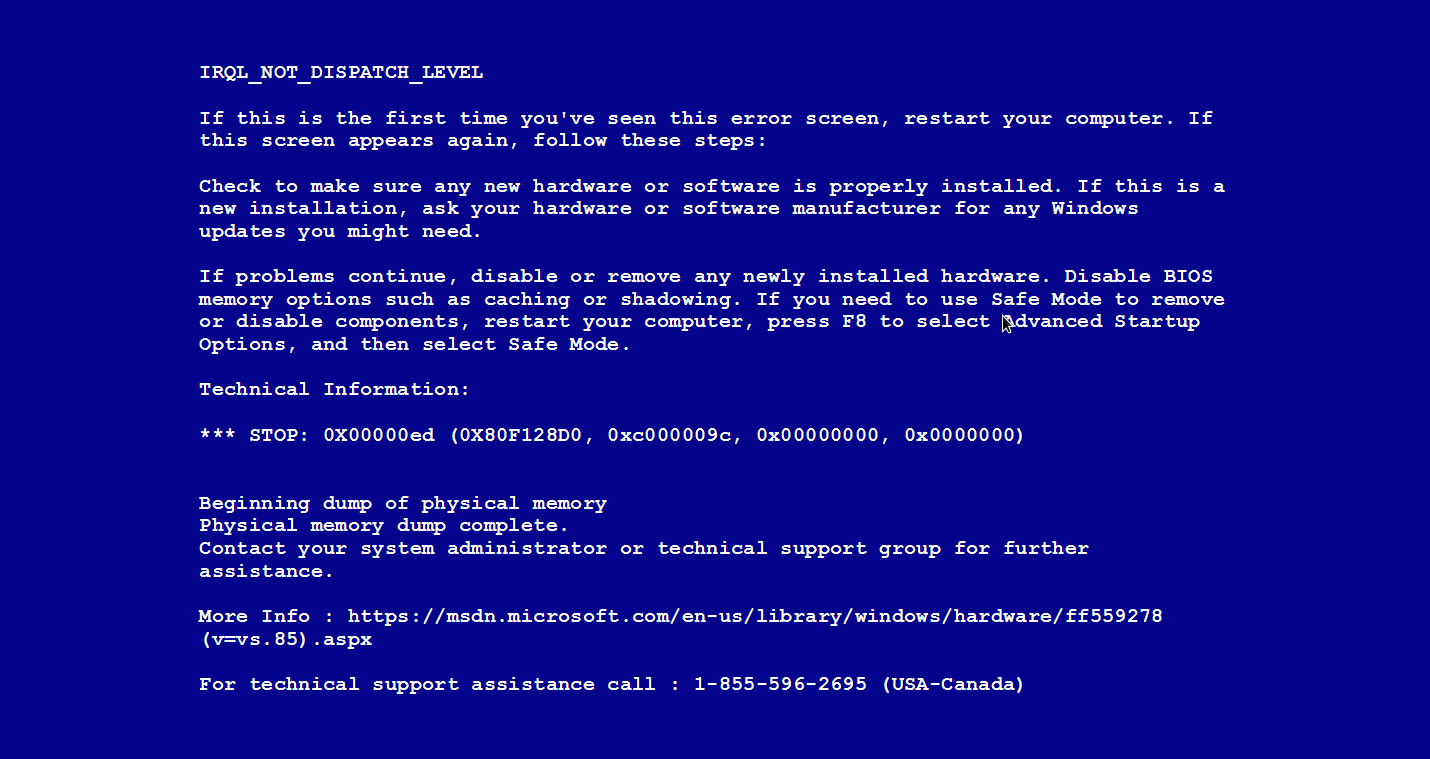
This message will display in full screen while at the same time both keyboard and mouse are disabled, preventing the user from closing it down.
The only way out seems to hard reboot the computer.
Without a doubt many people will be distressed and fall for this scam. So what exactly happens if you do call that toll-free number?
Rogue tech support
The ‘agent’ who answers the phone call has a heavy Indian accent and is sitting in a crowded boiler room, judging by the loud noise surrounding him. After the basic formalities of taking down your name and operating system information, he will have you download the TeamViewer remote control software.
It doesn’t take very long for the technician to start spilling out lies and even downloading a fake “Microsoft Internet Safety and Security Center”, a simple batch file (Microsoft Scanner.bat)
The program merely does a few file listing commands and is stuffed with bogus alarming errors. The technician makes sure to insist on the fact that your computer is riddled with viruses and already involved in terrorist attacks.
The coup de grâce comes with a hefty fee to clean up the otherwise fine computer.
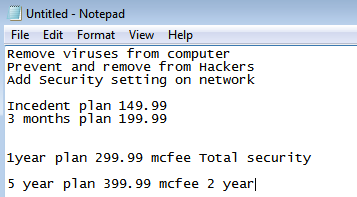
The company behind this particular operation is Thy Tech Support and they have been added to our tech support scams blacklist for:
- Using misleading tactics to force a sale
- Finding viruses, malware or an infection on a perfectly clean system
Despite what it says on their website, they are not located in the US, but rather in Delhi, India (IP lookup from IPligence).
Wannabe malware authors?
Tech support scammers started with the most simple form of social engineering by cold calling people. This technique is cheap but has a low success rate because it is very random and after (too) many years of being in use, it is starting to be less effective.
The abuse of online advertising was a logical next step for fraudsters trying to get in front of potential victims. In fact, they simply copied what was done before by other cyber criminals, for example with Browlock.
If they can code html templates they can also code real applications. We saw that with modified versions of popular installers for antivirus software.
However this latest incarnation is a little bit more worrisome because this is the realm of malware and once you get into it, there’s no way back.
Malwarebytes Anti-Malware detects this file as Ransom.SenseiUpdater.
Many thanks to Rich Matteo, Joshua Cannell and hasherezade for their respective contributions.