Update 08/14: The campaign has moved to another advertiser (AOL) and new Azure domain:

Malvertising URL:
imp.bid.ace.advertising.com/{redacted}pmcpmprice=0.545/{redacted}dref=http://www.ebay.com/sch/i.html?_nkw=jazzy+wheelchair+battery&_pgn=3&_skc=100&rt=nc First redirection (Azure website):
v5tr34-a09.azurewebsites.net/?=a09vv5vtrkpSecond redirection
:
mbiscotti.com/?Xz29TuVbablQcAngler exploit kit
:
abgzdbergzr.jeppe.iemooentypo.com/{redacted} abgzdbergzr.le9.anguoanti-malware.net/abgzdbergzr/{redacted}Our telemetry captured this malvertising on eBay.com and the cost per thousand impressions (CPM) for this ad was $0.545. Visitors that were served that ad were redirected to the Angler exploit, known for dropping ransomware and ad fraud malware.
– – Original story —
The actors behind the recent Yahoo! malvertising attack are still very much active and able to infect people who browse popular websites.
We have been tracking this campaign and noticed that is has recently moved to a new ad network used by many top publishers.
- weather.com 121M visits per month
- drudgereport.com 61.8M visits per month
- wunderground.com 49.9M visits per month
- findagrave.com 6M visits per month
- webmaila.juno.com 3.6M visits per month
- my.netzero.net 3.2M visits per month
- sltrib.com 1.8M visits per month
Stats according to SimilarWeb.com
The malvertising is loaded via AdSpirit.de and includes a redirection to an Azure website. Note how both URLs are using HTTPS encryption, making it harder to detect the malicious traffic at the network layer.
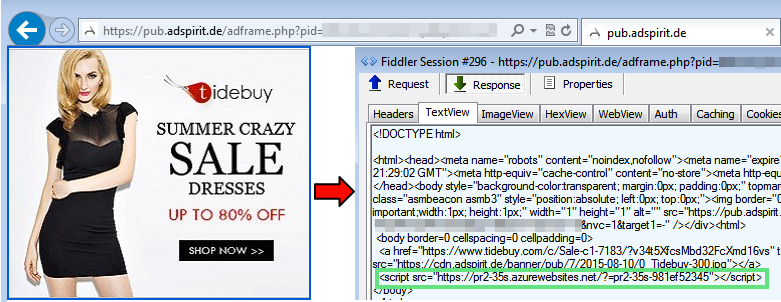
Redirection chain
- Publisher’s website
- https://pub.adspirit.de/adframe.php?pid=[redacted]
- https://pr2-35s.azurewebsites.net/?=pr2-35s-981ef52345
- abcmenorca.net/?xvQtdNvLGcvSehsbLCdz
- Angler Exploit Kit
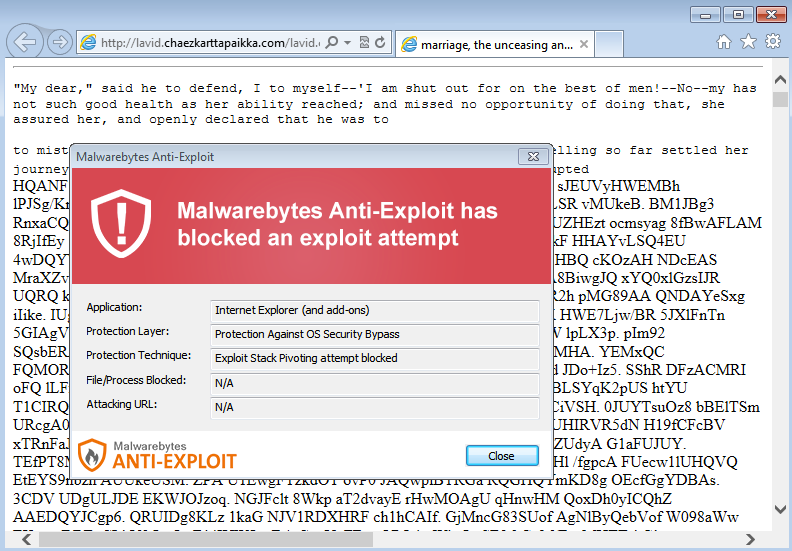
Malwarebytes Anti-Exploit users were protected against this attack.
We informed the ad network and although they did not immediately get back to us, the rogue advert was taken down.










