With the holiday season here, we are seeing a rise in online scams that attempt to trick victims into giving out personal information and extorting money for bogus services.
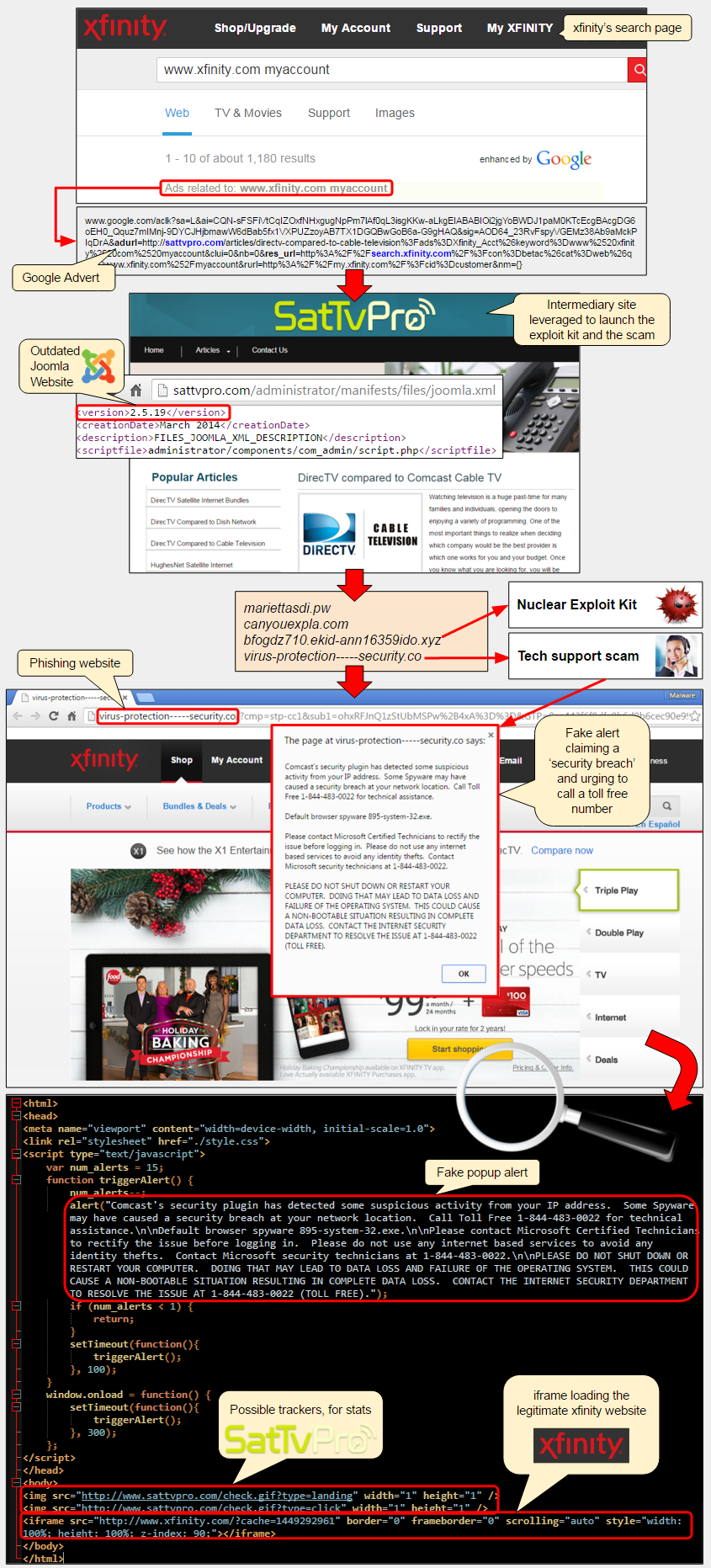
This latest one is particularly sneaky because it starts with an advert on Comcast’s Xfinity search page, the largest provider of cable internet access in the US, which attempts to infect visitors via an exploit kit and finally delivers a tech support scam.
The advert for a review site called SatTvPro.com via Google AdWords appeared on some of Xfinity’s search results page. When people clicked on the ad, it launched the review site (running an outdated version of the Joomla CMS) but also silently loaded a series of redirects leading to the Nuclear exploit kit.
Although we did not collect the malware payload in this particular case, vulnerable machines would likely be infected with the CryptoWall ransomware or another variant.
This was not the end of the ordeal for some Comcast customers. Indeed, an additional phishing website designed to look like the Xfinity portal would immediately display a warning claiming (quite rightly) that their computers may have been breached.
This tech support scam page pretending to be Xfinity was hosted on a completely separate domain from the SatTvPro site but yet contained interesting artifacts linking the two together:
- Web beacons, in the form of 1×1 pixel images typically used for tracking the number of visits to a site, were directly loading from SatTvPro.com, therefore establishing a relationship between the initial advert, the review site and the scam page.
This makes it the first attack we have seen which combines malvertising, exploit kit, phishing-like page and tech support scam.
Step by step review of the con:
- A Comcast customer performs a search on the Xfinity web portal
- The search results powered by Google are displayed as well as ‘relevant ads’ at the top
- The user clicks on the top ad for “DirectTV compared to Comcast TV”
- This opens up a website called “SatTvPro” which silently loads the Nuclear exploit kit
- If the user’s computer is vulnerable, it is immediately infected with malware
- Another website appearing to be the Xfinity portal loads up and displays a critical warning
Comcast’s security plugin has detected some suspicious activity from your IP address. Some Spyware may have caused a security breach at your network location. Call Toll Free 1-866-319-7176 for technical assistance
The whole attack is illustrated in the graphic below:
We immediately notified Google and Comcast about this attack. The SatTvPro website was quickly flagged by Google’s Safebrowsing: “Some pages on this website send visitors to the following dangerous websites: canyouexpla.com.“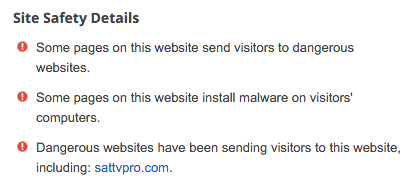
We actually reported on a case similar to Symantec’s story where a scam page contained a link to an exploit kit about a year ago. However, this may have been a poorly secured scam site that simply got hacked, unintentionally leading to the exploit kit.
But we have seen more recent examples that would justify this theory of “double payloads”. Back in July, VirusBulletin blogged about a Compromised site serves Nuclear exploit kit together with fake BSOD.
This latest attack on Comcast customers may very well indicate new realities where exploit kits and scams play well together. From the point of view of a malicious actor redirecting traffic (traffer), it makes a lot of sense to get paid a double commission for referral traffic: one from the exploit kit operator and another from tech support scammers.
Just before publication of this article, we noticed that the SatTvPro review site changed CMS from Joomla to WordPress (its latest version). It is possible that the rightful owner (which we contacted but did not return our message) realized the site was compromised and decided to roll out WordPress, rather than going through the more painful Joomla migration from the 2.x to 3.x branch.
There are still several plausible scenarios for who really was behind this attack. Based on the evidence we collected, the tech support scam page was definitely tailored for Comcast users, and not simply the pop up alert but also the full screen iframe loading the Xfinity portal.
The crooks who designed the phishing/scam page most likely exercised some control over the SatTvPro site since it was vulnerable and got hacked; but they also by chose to include web trackers directly calling back to it. Whether those same criminal actors also bought the ad via Google AdWords by impersonating the review site is not clear, but one thing is for sure: they definitely benefitted from it.
IOCs:
- Google advert:
www.google.com/aclk?sa=L&ai=CQN-sFSFiVtCqIZOxfNHxgugNpPm7lAf0qL3isgKKw-aLkgEIABABIOi2jgYoBWDJ1paM0KTcEcgBAcgDG6oEH0_Qquz7mIMnj-9DYCJHjbmawW6dBab5fx1VXPUZzoyAB7TX1DGQBwGoB6a-G9gHAQ&sig=AOD64_23RvFspyVGEMz38Ab9aMckPIqDrA&adurl=http://sattvpro.com/articles/directv-compared-to-cable-television%3Fads%3DXfinity_Acct%26keyword%3Dwww%2520xfinity%2520com%2520myaccount&clui=0&nb=0&res_url=http%3A%2F%2Fsearch.xfinity.com%2F%3Fcon%3Dbetac%26cat%3Dweb%26q%3Dwww.xfinity.com%252Fmyaccount&rurl=http%3A%2F%2Fmy.xfinity.com%2F%3Fcid%3Dcustomer{redacted} - Review site (intermediary that launches EK and scam):
sattvpro.com/articles/directv-compared-to-cable-television?ads=Xfinity_Acct&keyword=www%20xfinity%20com%20myaccount
- Malicious redirections:
mariettasdi.pw/Ik/QLmnitT--MvXPs-z-SUhYNgry/Ms_ot.js?RHvFSlj=d4cJLf&u61JQ=1553&-LkAYic_=382t0_&k82AY4u=R32bLz2&Hf_NwY=3lM9HSd1K&ytr4-s=8d4d&_8Ra=6L682 canyouexpla.com/HV/mzX_-N-rxqwhVt/HNsYQpWvUK-yTu/_GIVYwiXRnZH_NM.js?fyB=bm08vbmd57dN790v2k1ieeWcR5dP2
- Nuclear Exploit Kit:
bfogdz710.ekid-ann16359ido.xyz/piranha/espying.php?enthusing=2838&totaling=softening&[421792336]=146582075
- Scam page:
virus-protection-----security.co/?cmp=stp-cc1&sub1=ohxRFJnQ1zStUbMSPw%2B4xA%3D%3D>P=0ae443f6f8dfa9b6d0b6cec90e99824b
This domain was registered on November 14 via proxy. Interestingly, another domain almost identical to it (six dashes instead of five):
virus-protection------security.co
was registered on December 11, also via proxy and on the same IP address: 45.55.101.48.










