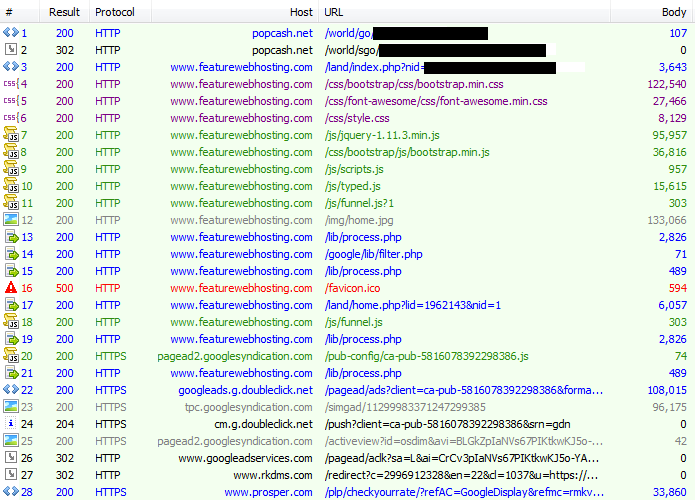
We’ve spotted an advertising campaign that tricks users into clicking on what looks like a notification alert that actually hides a legitimate advert, therefore abusing both the advertiser and the ad network hosting the ad (Google Ads Services).
The rogue actors behind this fraudulent activity are cleverly leveraging a European law on the use of cookies to seemingly prompt visitors to answer a question.
“The Cookie Law is a piece of privacy legislation that requires websites to get consent from visitors to store or retrieve any information on a computer, smartphone or tablet. All websites owned in the EU or targeted towards EU citizens, are now expected to comply with the law.”
Source: https://www.cookielaw.org/the-cookie-law/
We took apart one such page to describe exactly how it works.
A legitimate ad banner is loaded via an iframe and placed right on top of the warning message. However, that ad is invisible to the naked eye because of a parameter within that iframe which sets its opacity to zero.
To that effect, when a user clicks anywhere on the pop up message it acts as though they clicked on the ad banner itself, which loads the advertiser’s website.
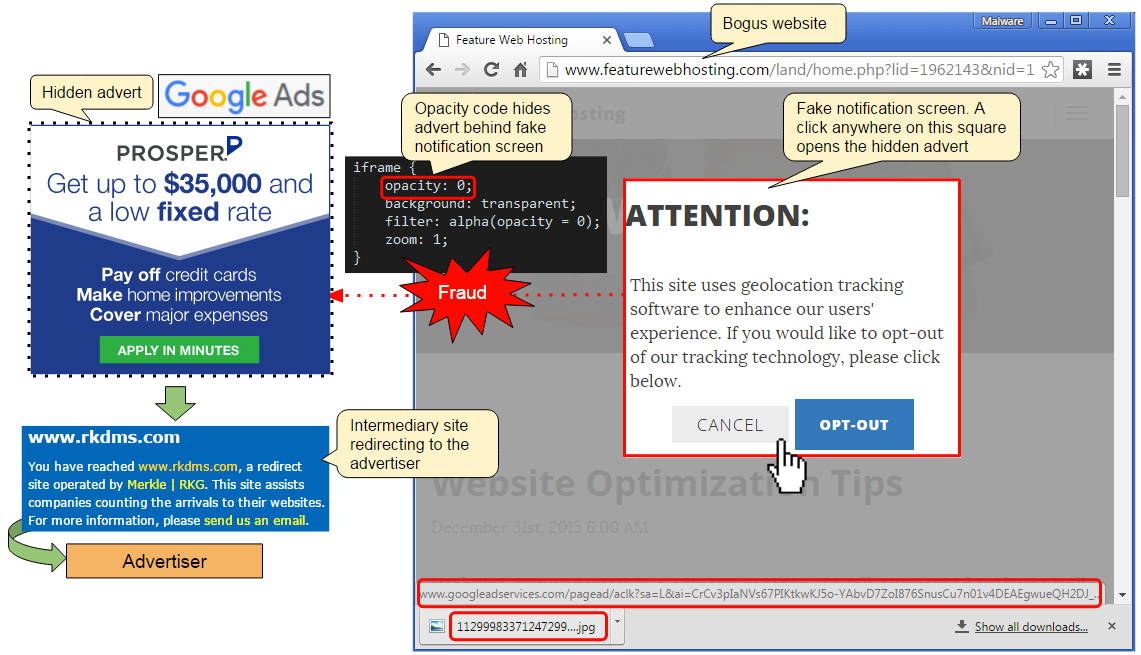
While simple, this technique, also known as clickjacking, is pretty effective at generating clicks that look perfectly legitimate and performed by real human beings as opposed to bots.
This is costing advertisers and ad networks a lot of money while online crooks are profiting from bogus Pay Per Click traffic. We have notified Google about this fraudulent scheme.
IOCs:
Ad network involved:
- popcash.net
:
- featurewebhosting.com
- elitewebhostings.com
- bestcartoday.info
- hotcartop.online
- ivirtualcloudhost.com
: