While looking into an infection associated with a “system optimizer”—Didn’t we say they’re digital snake oil?—we identified a multi-functional installer called FAsetup1.exe (md5 902e30fa3dc4bf543b523b4a41eb8acd) as the source. This file offers a variety of different bundlers and scams that are usually different every time you run the executable and the offers vary with the user’s geolocation and operating system.
This “advertisement downloader” opens various advertisements, scam pages, fake alerts, and install sites for potentially unwanted programs (PUPs). Let us show you some examples.
Fake alerts
These show up quite frequently. What they all have in common is a popup telling you that you need a new version of something. Be it:
- Java
- Flash Video Player
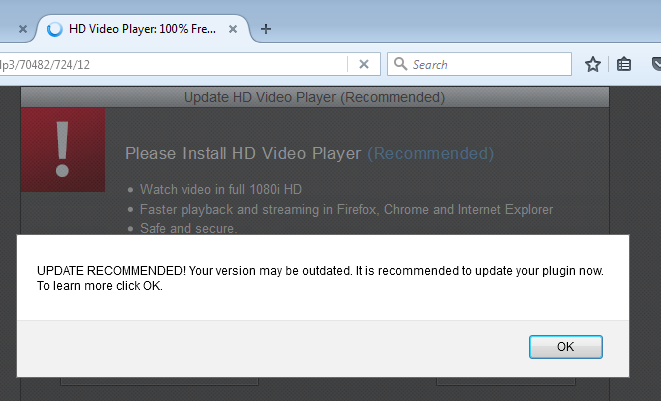
- HD Video Player
- Adobe Flash Player
- or just “Your” Flash Player
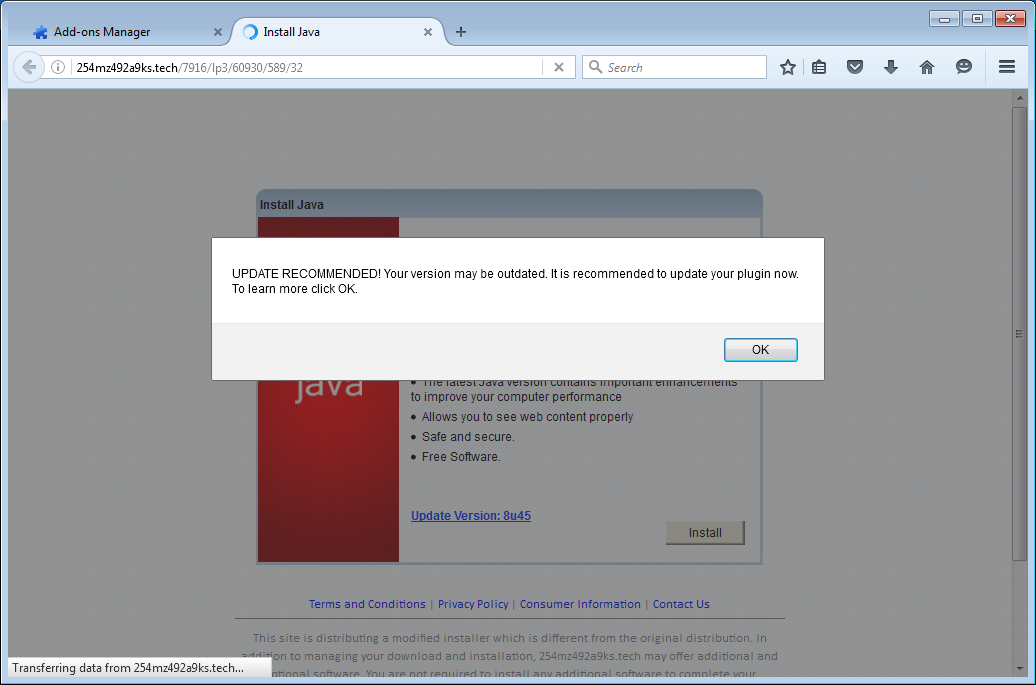
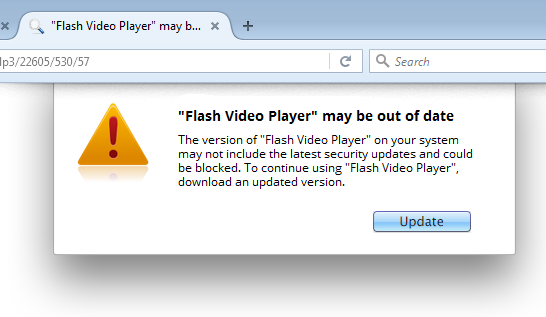
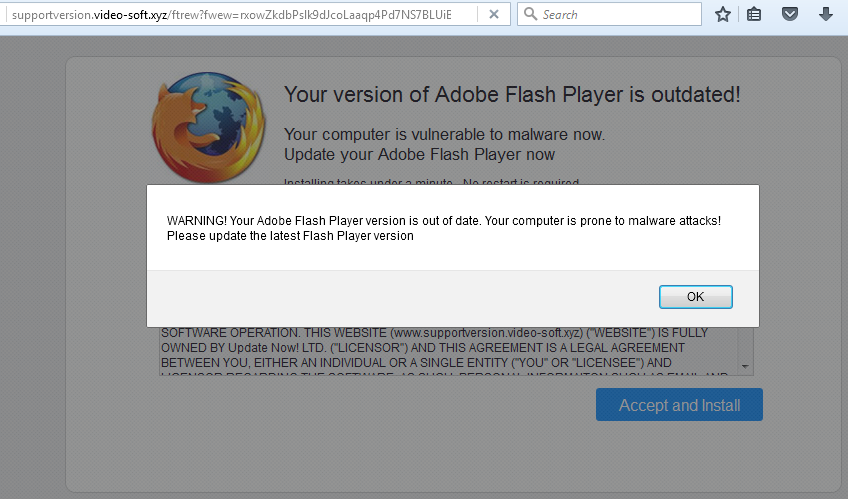
I tried a few of these “updates” and most of them are the same bundle of adware installers wrapped around the core install. The Java “updater,” for example, installed an old version of Java and offered to install Norton360, WeatherBug, Lenovo ReachIT, DriveUpdate, and PCMechanic—a tactic that we have discussed here before. Others include the VLC Player, which is well known for being bundled with adware and other PUPs.
Scams
We also noticed some scam attempts, including the “earn tons of money working from home” scam shown below, but also the type that tries to get your personal information by having you fill out all your personal data at the off chance of winning an iPhone in a survey.
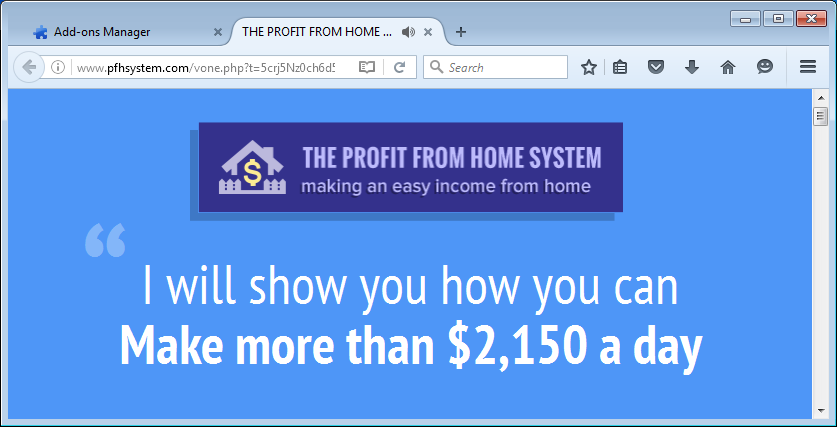
PUP installers
On top of that, we also encountered some sites that offered up installers for PUPs like Mindspark’s SendFilesFree and the search hijacker, SocialMediaNewtab.

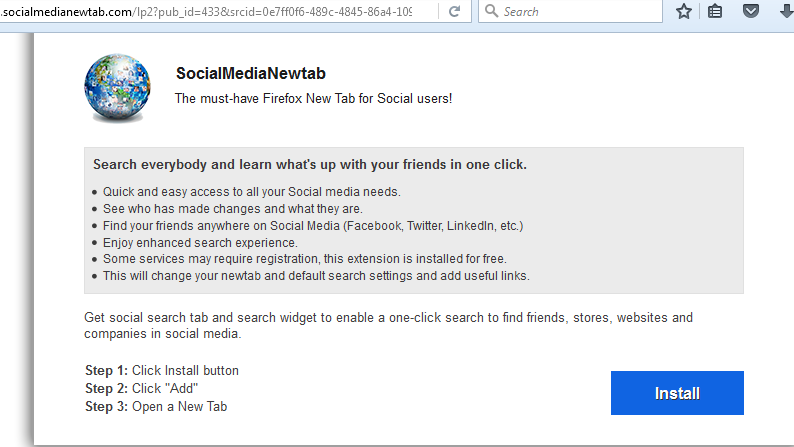
Targets by geolocation and operating system
The “advertisement downloader” targets users by geolocation as well as by Operating System (OS). My Windows 7 Virtual Machine is connected through a proxy and will claim to be in the USA, and that is what got me to the sites we discussed above but depending on your location you may get very different results.
For example, these are the ones I received on my Windows 10 system that is not connected by proxy, so it will show I’m in the Netherlands.
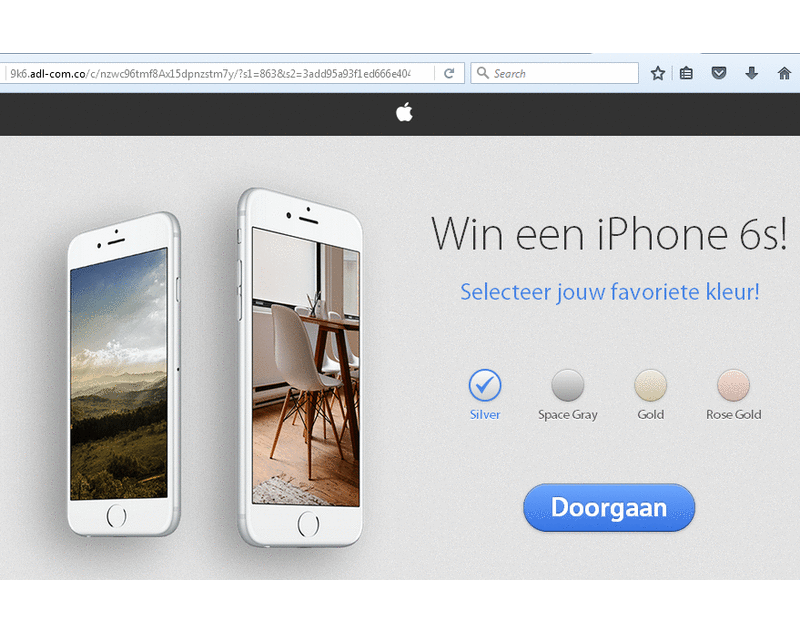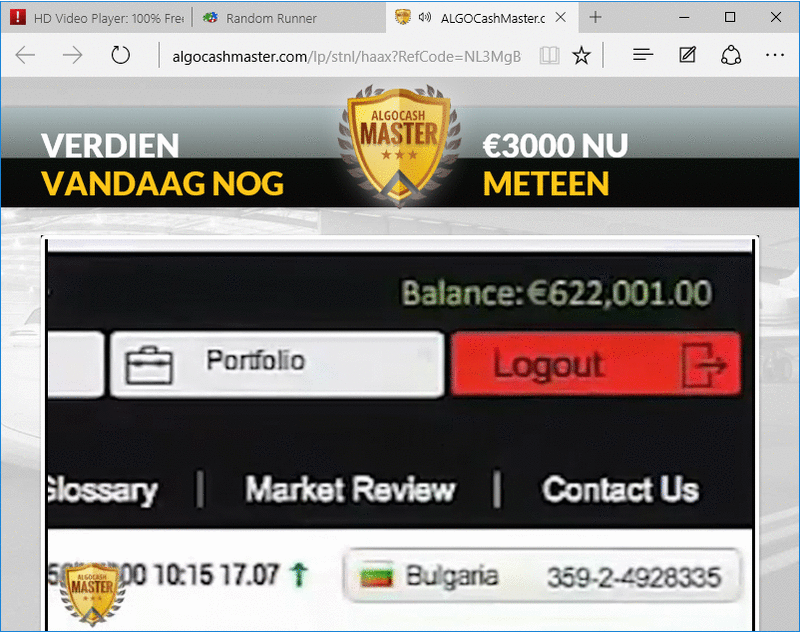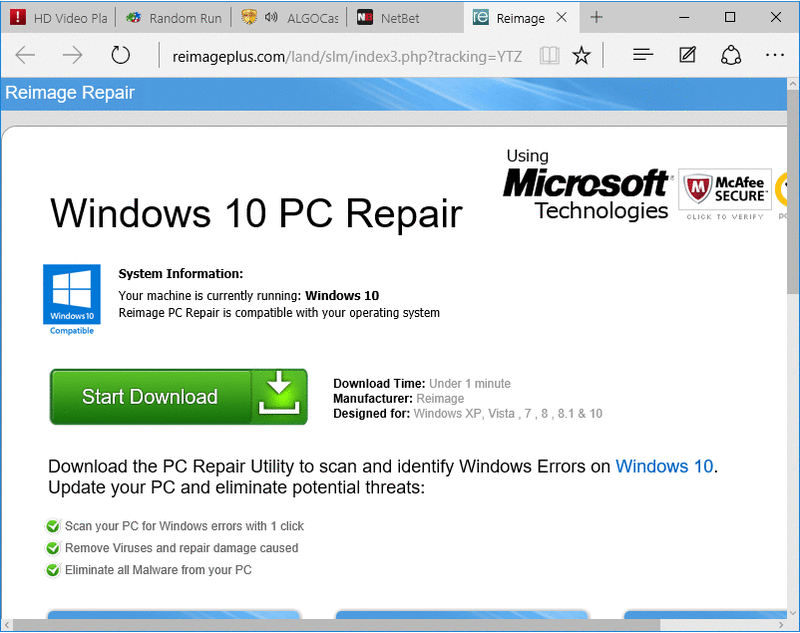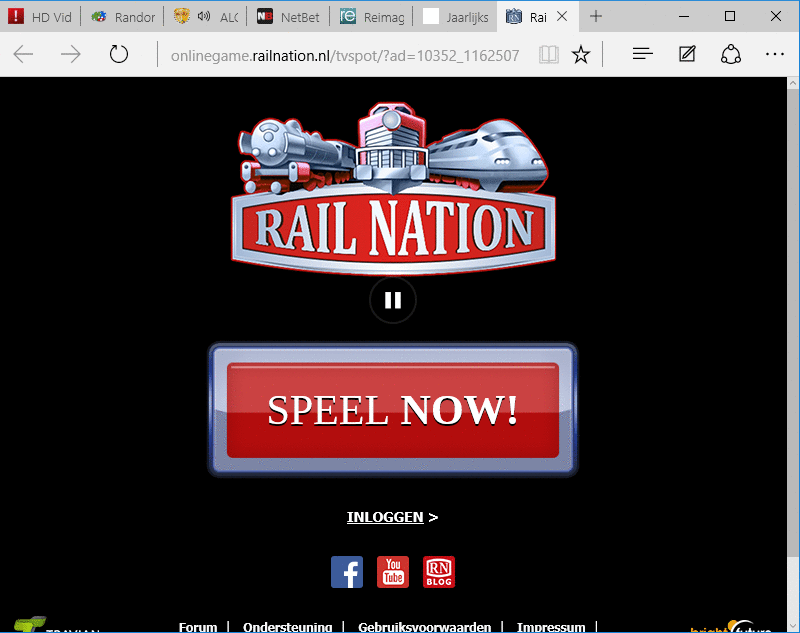
As you may see all the sites are in Dutch and the “Reimage” advertisement is now aimed at Windows 10.
Path to the advertisements
From what I have been able to follow, the path to the advertisements is linked through these sites:
- adswarez(dot)com
- minhaspromocoes(dot)com
- openadserving(dot)com
Which one of these does the initial fingerprinting and who pays who for what are beyond the scope of this post, but all of these sites are blocked for Malwarebytes Anti-Malware Premium users who have “Malicious Website Protection” enabled.
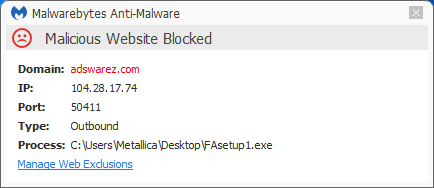
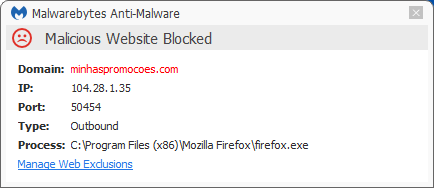
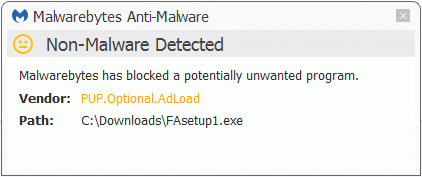
Malwarebytes Anti-Malware detects FAsetup1.exe as PUP.Optional.AdLoad.
Summary
In this post, we have taken a look at the results of being infected with PUP.Optional.AdLoad. Looking at the workings of the file, it is probably intended to run as a service or a Scheduled Task. In these cases, the user is presented with a new advertisement in a browser tab or window every few minutes.
As always:
Save yourself the hassle and get protected.
Pieter Arntz