At Malwarebytes Labs, we’re never short of PUPs to analyse and explore. As per our telemetry to date, SweetIM is one of the top PUPs Malwarebytes Anti-Malware (MBAM) detects and removes from our clients systems. In order to get to know what SweetIM software does on a user’s system, we have selected Bubble Hit by GamePacks (MD5: 0326564318717b9826c4b81eb5d34239).
What is SweetIM?
It is a software product of a company with the same name, SweetIM Technologies LTD, which according to their EULA, is formerly known as the company, Imvent LTD. SweetIM software can be downloaded from its official website, www[DOT]sweetim[DOT]com, but as the brand is associated with third-party affiliates, users can expect to find SweetIM bundled with other free, publicly available software.
SweetIM can be installed on Windows and Mac OS X.
What is Bubble Hit by GamePacks?
Bubble Hit is a bubble shooting game wherein players are asked to clear the colored bubbles from a board by connecting at least three bubbles of the same color. There’s an online version of similar games like this that doesn’t require any installation.
What happens when you install and execute SweetIM?
Bubble Hit by GamePacks, in particular, installs like any other software. Below is a slideshow of the program’s interface shown in succession after double-clicking the installer file:
The below shortcut file is then created on the user’s Desktop:

Here’s how the game would appear on the user’s desktop once the shortcut is double-clicked:
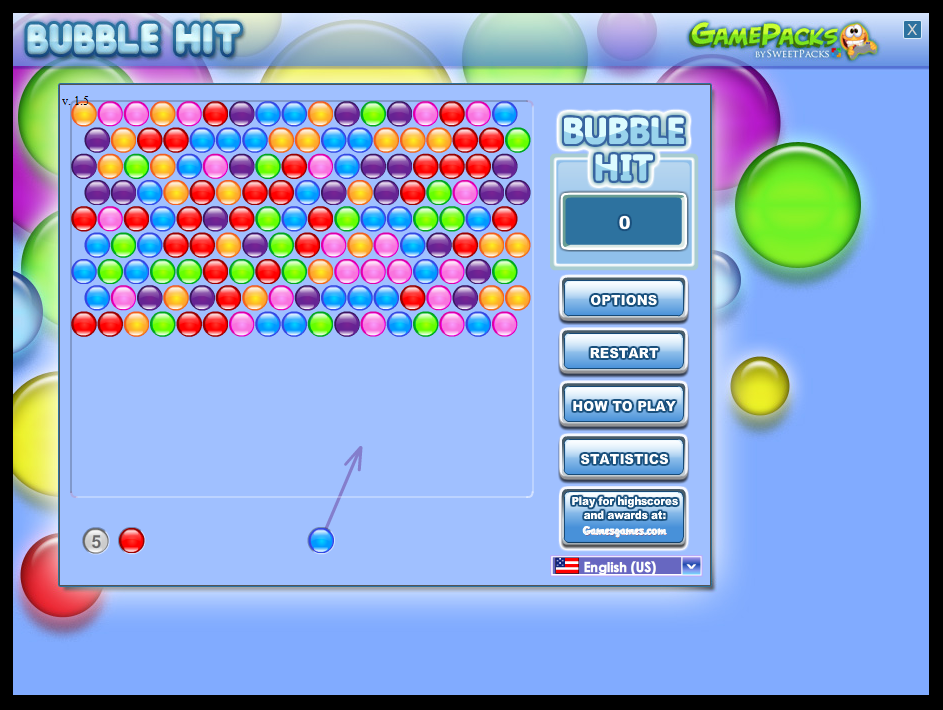
Pop ’em! Pop ’em ALL!
Notable files and/or folders added:
- C:Program Files (x86)Mozilla Firefoxfirefox.cfg
- a Firefox configuration file
- C:WindowsSystem32dmwu.exe
- detected as Adware.InstallBrain
- C:WindowsSysWOW64ARFCwrtc.exe
- detected as PUP.Optional.Perion
- C:WindowsSysWOW64WNLT
- detected as PUP.Optional.Perion
Notable entries in the registry that are added:
- HKLMSYSTEMCURRENTCONTROLSETSERVICESSHAREDACCESSPARAMETERS FIREWALLPOLICYFIREWALLRULES|{C4850434-A1D8-41B2-8280-F7D84D16F659}
- HKLMSYSTEMCURRENTCONTROLSETSERVICESSHAREDACCESSPARAMETERS FIREWALLPOLICYFIREWALLRULES|{E61685E1-22E1-4F63-9554-5A268CEA6E05}
- HKLMSYSTEMCURRENTCONTROLSETSERVICESSHAREDACCESSPARAMETERS FIREWALLPOLICYFIREWALLRULES|{FB21A74D-A36D-403A-B957-A4DE53FE3FC9}
- HKLMSYSTEMCURRENTCONTROLSETSERVICESSHAREDACCESSPARAMETERS FIREWALLPOLICYFIREWALLRULES|{B7E0D1F5-3D00-46F9-B129-B3DC5CEE38E6}
The above keys are “rules” that tells the firewall to allow traffic coming to and from the dropped files, dmwu.exe and wrtc.exe.
Furthermore, based on its registry logs, Bubble Hit by GamePacks’s installer adds emoticons and other elements that “enhances user experience” to the following instant messengers:
- ICQ
- MSN Messenger (currently known as Windows Live Messenger)
- Y! Pager (currently known as Yahoo! Messenger)
Other notable changes:
Users will find that additional changes to their systems will only take place if they allow Bubble Hit to make modifications during its installation phase. Such changes include the search engine being changed to “SweetIM search”, the home page being changed to home[DOT]sweetim[DOT]com, and the browser having an added extension. For example, below is a screenshot of the DealPly add-on prompt for Firefox:
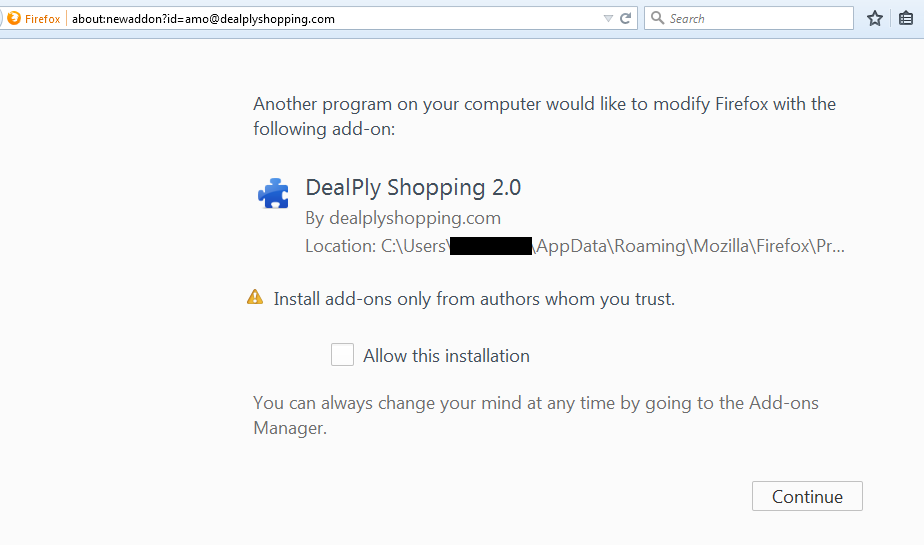
click to enlarge
Malwarebytes categorizes DealPly as a browser hijacker.
For a complete or detailed list of changes Bubble Hit by GamePacks does to user systems, visit our forum page.
Does Malwarebytes Anti-Malware (MBAM) detect Bubble Hit by GamePacks?
We detect this particular program as PUP.Optional.SweetIM. Check out this Malwarebytes forum post for the complete removal instructions for Bubble Hit by GamePacks.
Conclusion
We’re reminding our readers once again to take extra care when downloading freebies like games and software online. While most PUPs still rely on this kind of lure, others have already begun using fake notifications, such as software updates or ads on Web pages, to get users to click, download, and install them without a second thought. However dodgy and/or malicious files arrive on systems, it is always best to keep your AV software updated and set to real-time blocking. Scanning files to make sure they’re safe to execute can also be a good computing practice if you’re unsure of the legitimacy of their legitimacy.
Stay safe, everyone!
More PUP Friday post(s):
- The Next Generation Yontoo Browser Hijackers
- GsearchFinder Hijackers Add Extra Firefox Profile
- SafeSoft Protector Abuses Privoxy
- Adware PUP Dotdo FastInternet Blocks Security Related Domains
- TopFlix: A DNS Unlocker Variant
Jovi Umawing