A colleague referred me to an article on a piece of cross-platform malware, called Adwind RAT (short for “remote access tool”), that was going undetected.
This is often code for “this malware was written in Java,” which doesn’t necessarily mean that it actually drops a Mac payload. So I was a bit skeptical, and said so. But, hey, new malware to play with… how could I resist taking a peek?
The first thing I noticed was – surprise, surprise – the malware was written in Java. Prepared for disappointment, I grabbed a sample of the dropper from VirusTotal.
The dropper was a file named Doc-172394856.jar. It would seem that it’s meant to be a document of some kind, but it’s not very convincing, as it has a .jar extension, not something more expected like .docx or .pdf. Strike one.
It also required me to install Java just to run it. Since Apple quit including Java in the system years ago, that’s something that most people don’t have on their Macs these days. So, to open it, you’d have to download a large file – after figuring out exactly what to download on Oracle’s rather hard-to-navigate website – and install it. Strike two.
Next, of course, the file wasn’t codesigned in any way, so of course Gatekeeper’s default settings prevented it from running. Strike three.
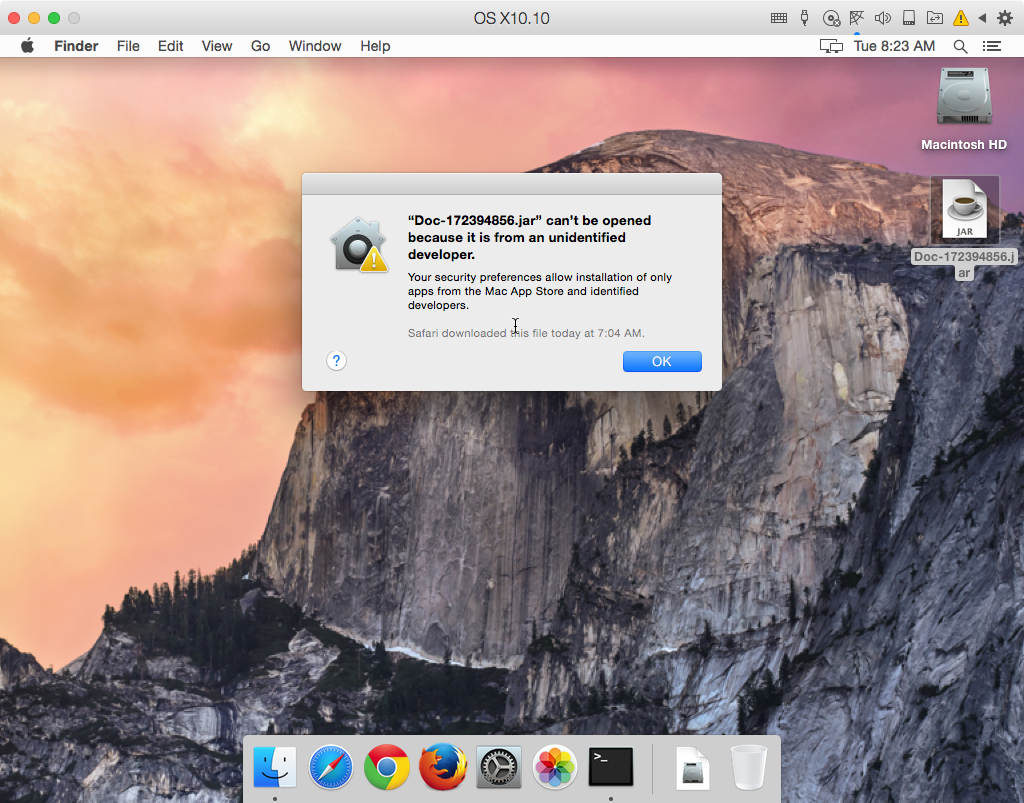
So I bypassed Gatekeeper. The file executed in Java, opening and then closing again in about a second. No decoy document opened, to make it seem as if the user had actually opened a document. No fake app user interface, to make the user think it was legit. Nothing to help the user believe this is legit. Strike… four? (Okay, the sports metaphor is failing at this point.)
I was primed for disappointment, not expecting any meaningful infection. However, when I looked to see what file system changes had been made, lo and behold, there was a brand new launch agent, loading an executable found in a brand new hidden folder!
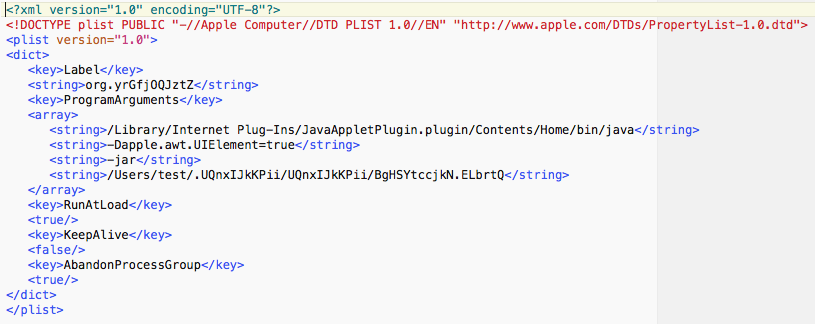
The launch agent file was named org.yrGfjOQJztZ.plist, and was found in the user LaunchAgents folder. It loaded a Java app named BgHSYtccjkN.ELbrtQ, and found in a hidden folder in the user’s home folder.
Even more interesting, as I was looking through the files that had been created, I noticed my webcam light was on. I wasn’t able to find any newly created video files, however, and could not get this behavior to repeat in subsequent tests.
Beyond the obvious use of the webcam, this malware is reported to perform a number of other backdoor activities, such as downloading and executing new malicious files, executing remote commands and sending data from the infected system to a server controlled by the hacker(s).
It communicates with a server at jmcoru(dot)alcatelupd(dot)xyz, and the data is encrypted to prevent snooping by nosy malware researchers.
Interestingly, this malware appears to have a long history, being distributed at least since early 2012 under a number of different names, such as Frutas, Unrecom, jRAT, AlienSpy and JSocket.
It just so happens that jRAT – a tool that could be used to create a custom backdoor server, to be used for infecting machines – is thought to have been used to create the Jacksbot malware, which affected Mac users in late 2012.
At the end of the day, it turned out to be true that this is actually cross-platform malware, with a Mac payload, but that doesn’t mean the hackers behind it really put that much effort into making it work on the Mac.
In all, this malware isn’t particularly worrisome. It would take a bit of effort on the part of a Mac user to infect their computer with Adwind in its current form.
If you downloaded this file, or received it by e-mail, there would be three big potential red flags before you could even infect yourself, and another after the fact that might clue you in to the fact that what you just opened wasn’t really what it seemed to be.
Adwind is, overall, a fairly weak effort on the Mac.










