We here at Malwarebytes Labs have been posting on the ins and outs of tech support scams since 2013. (First post here, if you’re interested). That amounts to at least a decade in computer years.
So with all that time, effort, and analysis, why are these people still in business? They’re generally technically inept, have atrocious OPSEC, don’t vary their operations in the slightest, and have been publicly exposed countless times. And yet. . .
They keep…

…scamming
online…

…users.

So rather than another post where we name and shame these guys, let’s take a step back and look at a few of the structural forces that sometimes prevent us from smiting scammers for great justice.
1. The Search Engines
There’s a saying out there that if you lose $1000, its your problem.
But if you lose $150,000,000, it’s the bank’s problem.
Similarly, once ad revenue climbs to a certain amount, search engines tend to be dis-incentivised to look into where that money is coming from. Almost all tech support scammers will sign up with multiple ad networks as a way of tracking traffic as well as diversifying income streams. Perversely, if the core scam achieves a certain level of success, the income from legitimate traffic clicking on search engine ads can cause the likelihood of an investigation to plummet.
Search engine security algorithms tend to focus on indicators of fraud against the search engine, not against you the user. As such, the probability of a human fraud analyst even seeing the scam sites is low.
But Google and Bing both said that they won’t tolerate these scams anymore! Thats true-ish, but let’s allow the users on noted legitimate business site “Blackhat World” speak for themselves:
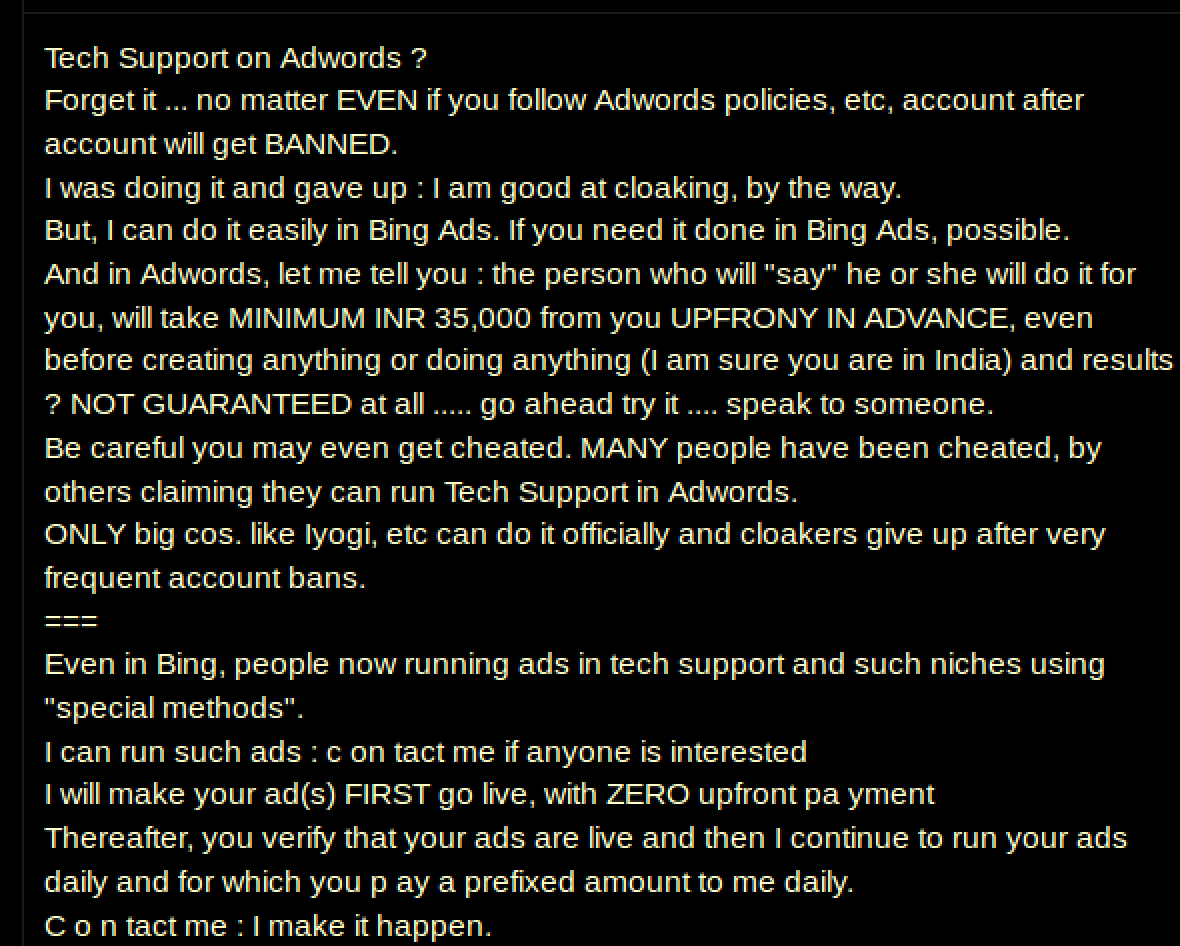
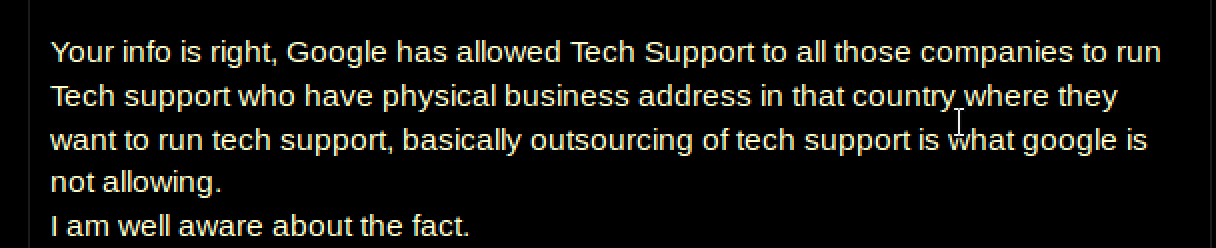
So take a big loophole in the ads approval process, add an algorithmic blind spot in fraud detection, and a well meaning search engine ends up with occasional difficulty in keeping their results clean.
2. The Law
The Digital Millennium Copyright Act (DMCA) is a 1996 US law that establishes a framework dealing with intellectual property infringement, and the responsibilities of third parties that host such content.
The gist of it is that if someone is hosting my content without my permission, and a third party is hosting that content, that third party has to take it down when I ask.
So what’s the problem? In short, a DMCA claim requires you to stipulate that “you are the owner, or authorized to act on behalf of the owner, of the copyright or of an exclusive right under the copyright that has allegedly been infringed.”
Here’s where it gets a little knotty: what constitutes authorization to act on behalf of the owner? Some companies require a signed, hardcopy letter. And given that most tech support scams target as many brands as possible, does it really make a difference if they only take down their fake Malwarebytes page?
Next, the Communications Decency Act (CDA) says that “No provider or user of an interactive computer service shall be treated as the publisher or speaker of any information provided by another information content provider.”
This means that an ISP unwittingly hosting illegal content can’t be held liable for it. The safe harbor provided allows some really great services to operate at a large scale, like Youtube. It also means that very, very large ISPs are not always responsive to takedown requests without bulletproof evidence of wrongdoing.
3. But is it a scam, though?
Ironically, this can be the hardest part of all.
Accusing someone of scamming who in fact isn’t is grossly irresponsible, and could be a crushing setback to a legitimate business. As such, the burden of proof before slinging an accusation is quite high, and time consuming. Our go to method is generally to call them up and see if they attempt a scam or not.
Alternatively, we can correlate reported victim data with previous incidents of proven fraud, infrastructure established by middlemen who advertise its utility for fraud, or identified fraudulent actors – until a preponderance of evidence supports the conclusion that the threat actors are almost certainly scamming end users. Both methods are effective, but both are painstaking, time-consuming, and resource intensive.
And given that the total number of fake tech support sites in hpHosts is currently sitting at 2162, there is an upper limit on how many scams can be effectively analyzed at any given time.
Why We’re Doing Pretty Well, Considering
You. Your reports of scams, fraudulent credit card charges, and scam company names and numbers tip us off to criminals that might otherwise look benign from their public web presence. Your diligence in reporting the evil doers is an early warning system that lets us know “hey maybe we should take a closer look at that.”
Here’s a few things Malwarebytes users have included in reports to us that are enormously helpful in smashing bad guys:
- **The name of the company appearing on credit card/Paypal statements**
- email addresses of the scammer they spoke with
- Company names that the phone reps use
- Callback numbers when the criminals contact you multiple times
- which legitimate company they’re trying to impersonate
- where the scammers say they’re located
- what website led to the scam page
- any software the phone rep tried to install
More data helps to make better judgements, faster. If you’d like a little more info on how to protect yourself from scams in the first place, check out our post here.