Researchers Claudio Guarnieri and Collin Anderson recently discovered new Mac malware, which they have dubbed MacDownloader. They report that this malware appears to be the work of Iranian hackers and is targeting US defense contractors, such as Lockheed Martin, Sierra Nevada Corporation, Raytheon, and Boeing.
The malware was first found on a spearphishing site, claiming to offer “Special Programs and Courses” to interns at these companies. The site showed a “broken video,” using the common trick of claiming that Adobe Flash Player was outdated and offering a link to a “Flash installer.”
That “Flash installer” was the malware dropper – although, as we’ll see, “dropper” may not be a very accurate term. The installer was a simple app, named “addone flashplayer” and has a Flash icon. (SHA256: 52efcfe30f96a85c9c068880c20663db64f0e08346e0f3b59c2e5bbcb41ba73c)
When run, the malware immediately opens a window offering to install the update.
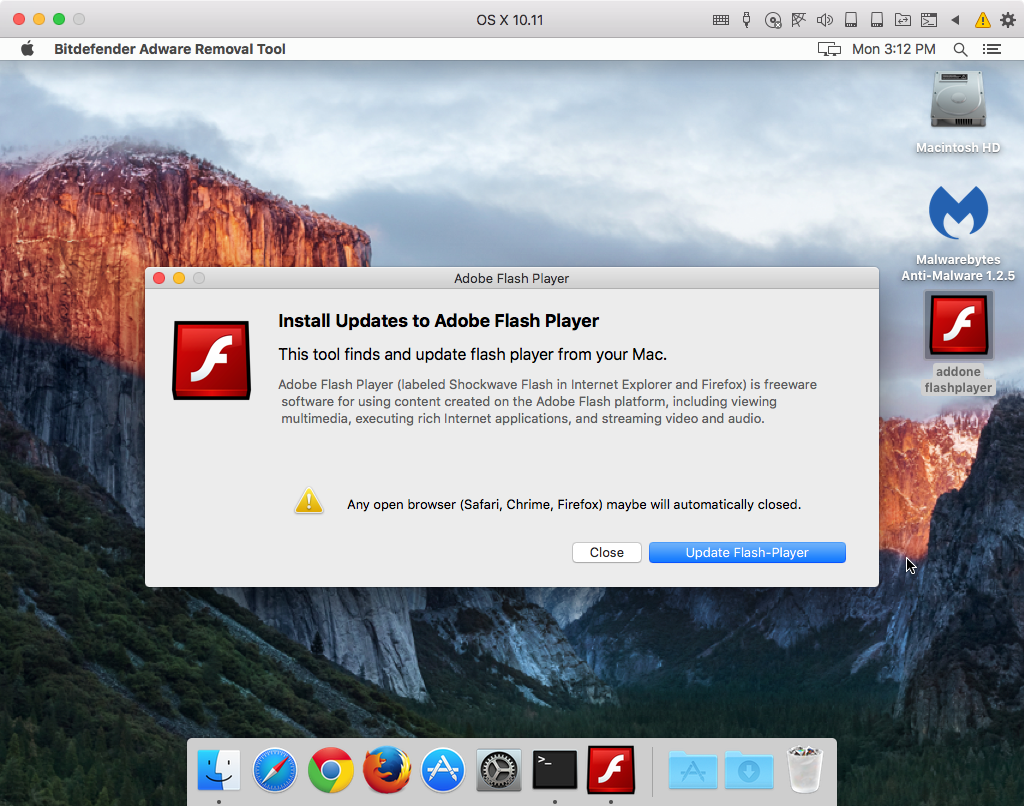
To those who know better, this doesn’t really look much like an actual Adobe Flash Player installer, but many people won’t realize that. There are some other red flags as well, such as some odd phrasing and other errors in the text shown.
The biggest red flag, though, is the name of the application shown in the menu bar next to the Apple menu. As can be seen from the screenshot above, it claims to be Bitdefender Adware Removal Tool. This is the first sign of a serious split personality issue in this malware, which can’t seem to decide whether it’s a Flash installer or an anti-adware program.
Interestingly, if the user clicks the Close button here the malware quits without doing anything else. That’s highly unusual for malware and is likely to be a sign of the poor coding that Guarnieri and Anderson mention in their analysis.
If the user chooses to proceed with the “update,” the malware will then show a rather odd window for what is supposed to be a Flash updater: a claim to have detected malware.
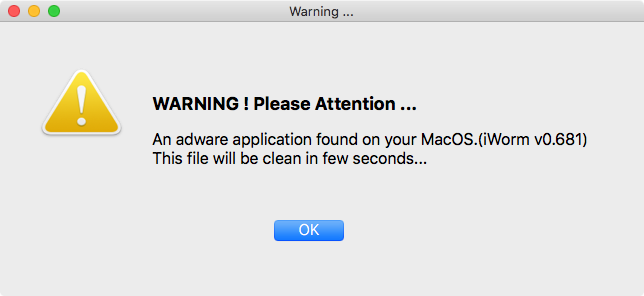
Again, there are some issues with phrasing and spacing in the text of this alert, not to mention the fact that a Flash updater should not be scanning your system like anti-virus software. (There’s also the fact that it calls iWorm “adware,” when it’s actually old malware, but the average user won’t know that there’s anything wrong with that.)
Guarnieri and Anderson believe that this malware was probably originally developed as a fake anti-virus app and hastily or sloppily repurposed into the form of a fake Flash updater, having found other evidence in the app that it was designed to imitate Bitdefender.
After clicking OK here, the user is asked for a password because “System Preferences wants to access from current application.”
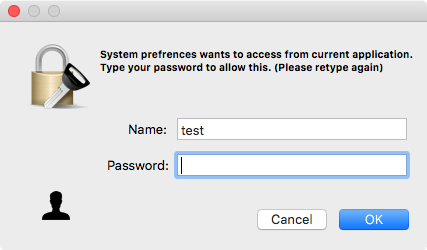
At this point, many people will be extremely suspicious. Fortunately, if the user decides to cancel at this point, the app will again exit without doing anything else.
If a password is entered, the app will then gather some information about the system and write it to /tmp/applist.txt. This file and the user’s keychains are then uploaded to the command and control (C&C) server. Since the applist.txt file contains the user’s username and password, thanks to the password request, this would allow the hackers to unlock the keychain files, accessing all the passwords stored within. (Fortunately, the C&C server is now offline.)
The malware appears to contain some code designed to download a payload from the C&C server and install it persistently in the system, Guarnieri and Anderson found that bugs in the code prevented that code from working properly. Thus, MacDownloader does not install anything persistently. Once it has been run, it’s done.
This malware continues the recent malware trends on macOS. In the past year, nearly all true Mac malware (as opposed to adware) has been 1) lame and 2) targeted.
Mac malware has a historical tendency towards lameness, not necessarily because the code itself is poor (though that’s often the case), but because it always uses the same old boring method of persistence: a launch agent/daemon that loads a hidden process. This makes Mac malware easy to spot and easy to remove.
In the case of MacDownloader, the malware takes “lame” to a new level, with poor code, sloppy UI, and non-functional persistence. (Though perhaps it should be given a little extra credit for trying – albeit unsuccessfully – to use an older persistence technique involving rc.common, which most people would not be looking for.)
Most Mac malware in recent years, with a few exceptions, have been targeted attacks. Such attacks have targeted human rights advocates, government agencies, research institutions, and others. This malware is no different, as it is being used to target US defense contractors via spearphishing, a technique in which links to specially-crafted malicious sites are sent to targeted individuals or groups via e-mail or other messaging services.
The majority of Mac users will never see this malware and one would hope that most of those who do would not be fooled by the clumsy behavior. Still, it doesn’t take many to fall for the tricks employed by this malware to get access to sensitive accounts within an organization, which can be used to pwn the entire company.










