Last year, we reported on a new modular malware called TrickBot that uses a network protocol similar to Dyreza. The malware was not particularly stealthy, and some parts looked to be still under development, but we noticed its potential and capability to be easily extended.
Indeed, the authors of TrickBot are persistent not only in spreading their malware but also in developing new features.
Some of the novel changes applied to TrickBot were noted in Spanish cybersecurity company S2Grupo’s June 2017 report called the Evolution of Trickbot.
In addition, it has been found that developers added to the bot a worm module, probably inspired by the success of other worm-equipped ransomware such as WannaCry and EternalPetya.
But authors of this malware didn’t stop there. Recently, we captured some additions that allow for TrickBot to attack Outlook and capture browsing data. For example, we noticed a new module called Outlook.dll, which was written in Delphi (while most of the other modules are written in C++). This may indicate that the team of TrickBot developers gained some new members that are more comfortable with this particular language.
Analyzed samples
- 9aac1e00d62e0b4049781cc5eff99bc7 – main sample (packed)
- 9b3659936354dceb1063a42f15d0f12a – main sample (unpacked)
- 60bd4480035e82393636b0fb60d351ba – bot 32 bit
- ba36cf1afb6b6eed38b0a8d54152335b – bot 64 bit
- 74933912ad87ec0b3a1b570a0ea0832b – loader for 64 bit
- 9b3659936354dceb1063a42f15d0f12a – main sample (unpacked)
Downloaded modules (32 bit):
- b6f9ba3fd8af478147c59b2f3b3043c7 – OutlookX32.dll
- ac32c723c94e2c311db78fb798f2dd63 – module.dll (importDll32)
- f8e58af3ffefd4037fef246e93a55dc8 – mailsearcher.dll (mailsearcher32)
- 25570c3d943c0d83d69b12bc8df29b9d – SystemInfo.dll (systeminfo32)
- 5ac93850e24e7f0be3831f1a7c463e9c – loader.dll (injectDll32), reflectively loads submodules:
- 69086a1e935446067ecb1d20bfa99266 – core-dll.dll
- b34d36c1c76b08e7b8f28d74fbf808d8 – rtbroker_dll.dll
Behavioral analysis
As before, after being deployed, TrickBot installs itself in a new directory created in %APPDATA%. It runs a new instance from the installation directory.
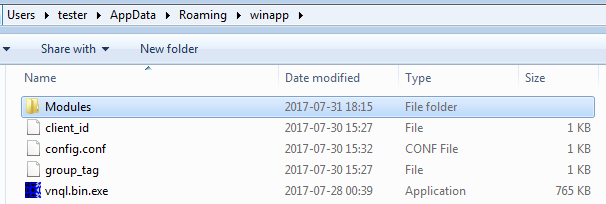
Inside, it creates another directory—Modules—where it drops downloaded modules and their configuration files in encrypted form:
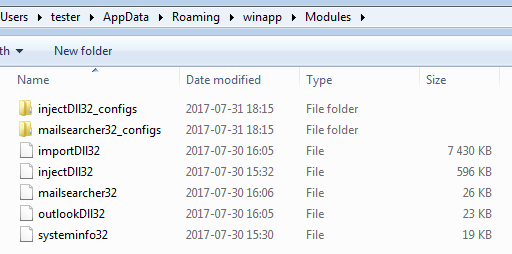
The way in which the modules and configuration files are encrypted didn’t change. We can still use the same scripts to recover them.
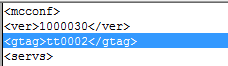
After decrypting config.conf, we got some more details about the current campaign: the version of the analyzed configuration is 1000030 and the given group tag is tt0002. Fragment:
As before, persistence is achieved with the help of a Scheduled Task:
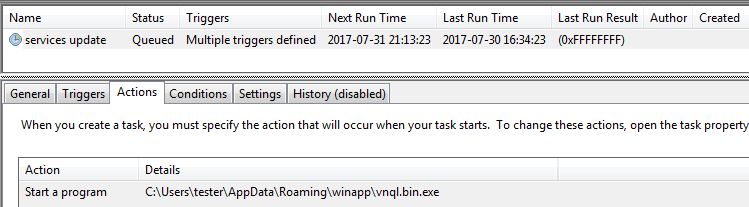
The task deploys the main bot that, after being run, decrypts and loads other modules. Each module is injected into a new instance of svchost:
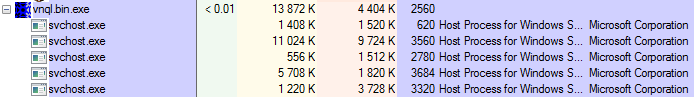
Inside the malware
As before, all the TrickBot modules follow a predefined API. They export four functions:- Control
- FreeBuffer
- Release
- Start
“>
As mentioned in “behavioral analysis,” we observed five modules in the current run. SystemInfo.dll and loader.dll (injectDll32) have been present in TrickBot since the very beginning. The module mailsearcher.dll was introduced in December 2016 (according to the F5 DevCentral’s article). But there are some modules in the set that we haven’t seen described before: module.dll and Outlook.dll.
module.dll/importDll32
This bulky module is written in C++, compiled with Qt5 and OpenSSL, and also incorporates SQLite. Inside the binary, we can find the strings indicating particular versions of the libraries:
- Qt 5.6.2 (i386-little_endian-ilp32 static release build; by GCC 6.2.0)
- OpenSSL 1.0.2k 26 Jan 2017
- 2017-02-13 16:02:40 ada05cfa86ad7f5645450ac7a2a21c9aa6e57d2 (SQLite)
We can also find references in the code. In the given example, QAbstractSocket class from Qt library is used:
DLL’s compilation timestamp indicates that it is pretty fresh, written in May 2017:
2017:05:27 14:27:06+01:00
Functionality-wise, this module is focused on stealing data from the browsers, such as:
- Cookies
- HTML5 local storage
- Browsing history
- Flash LSO (Local Shared Objects)
- URL hits
…and more.
Authors didn’t put any effort into hiding their intentions. Debug strings informing about every action taken are being printed. Examples:
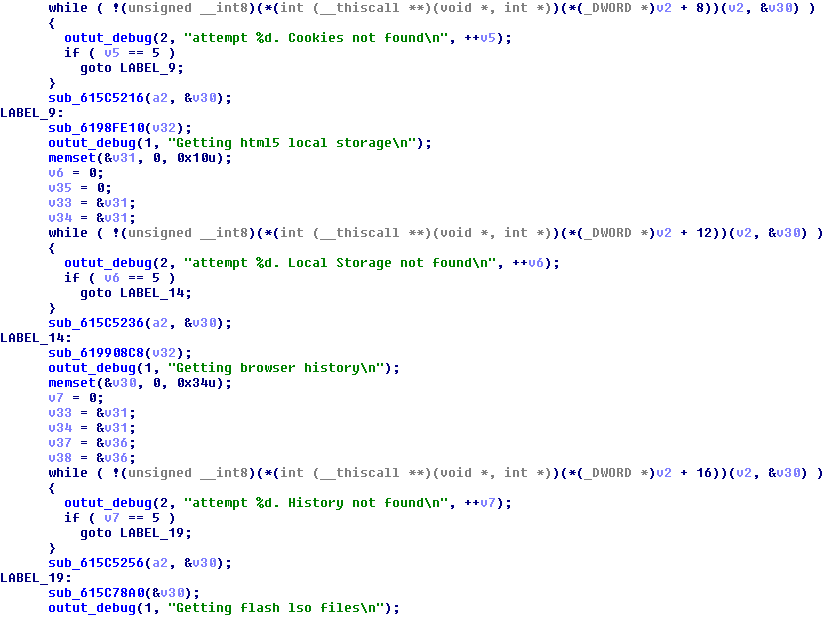
Grabbing URL hits:
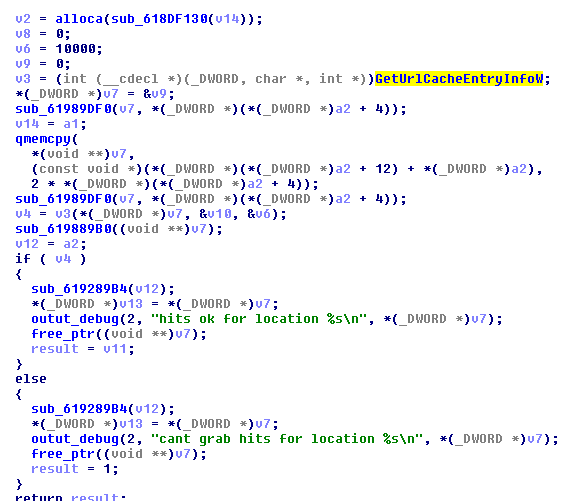
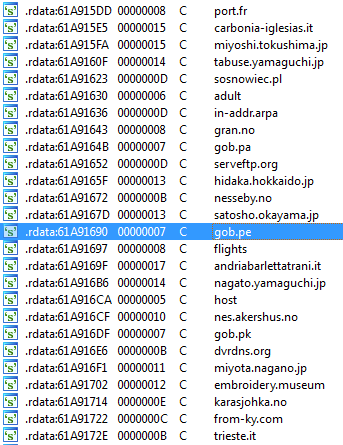
In contrast to loader.dll/injectDll (referenced here), which is modular and stores all the scripts and targets in dedicated configuration files, module.dll/importDll32 comes with all its data hardcoded. For example, inside the binary we found a long list of targets—websites from countries all around the world, including France, Italy, Japan, Poland, Norway, Peru, and more:
Browser fingerprinting
During its run, the module creates a hidden desktop: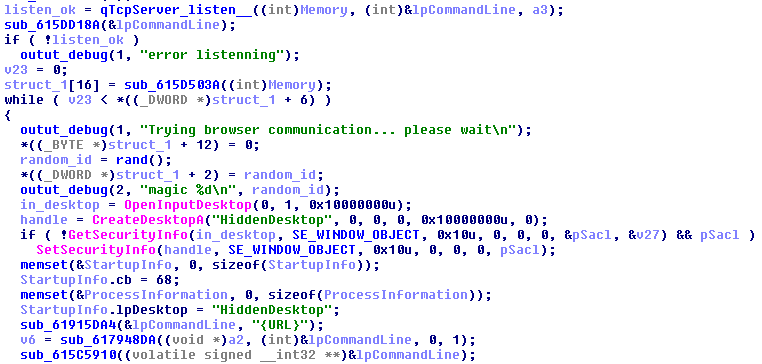
This desktop is used as a workspace where the malicious module can open and fingerprint browsers in a way that is not noticed by the user.
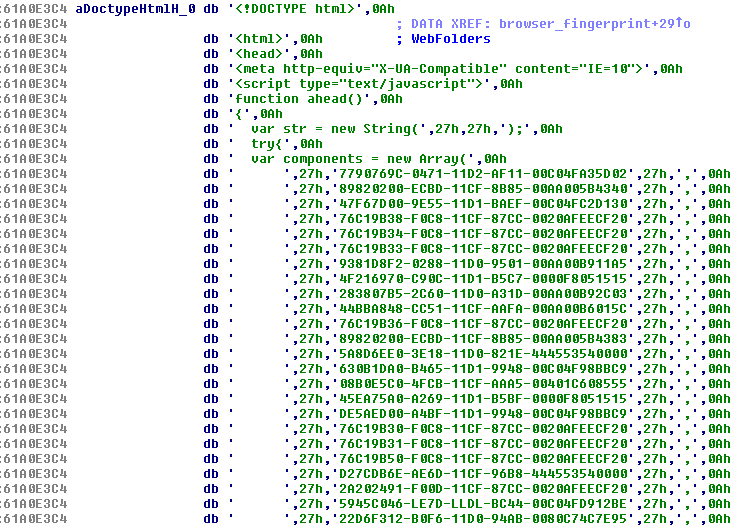
Inside the malware’s code, we found hardcoded HTML files with JavaScripts that are used for gathering information about the browser’s configuration. For example:
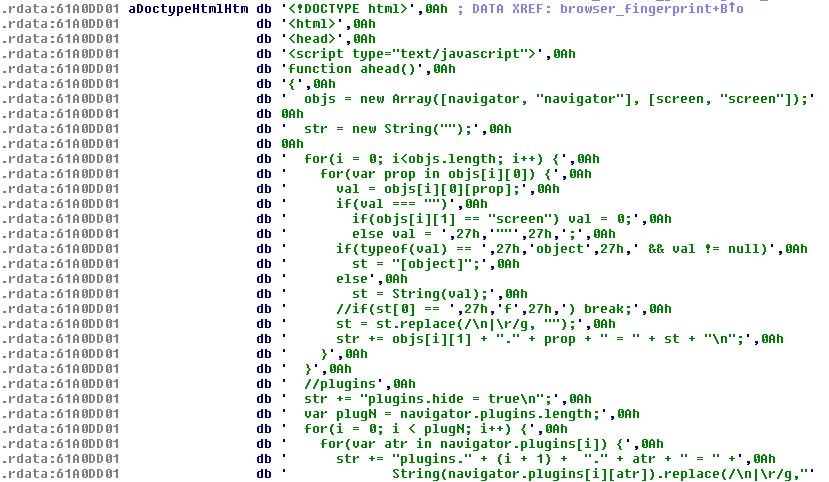
You can see the full content here.
This script, while being executed, fills the text area with the data gathered about the environment and passes this data to the malware:
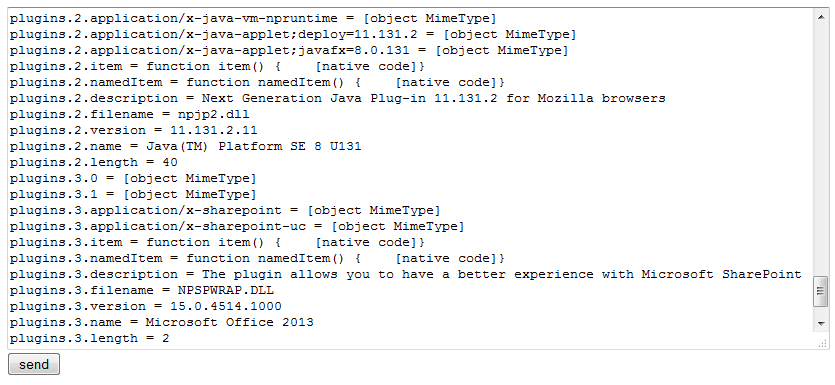
Another script is used for gathering information on the plugins installed in Internet Explorer (compare with this script):
You can see the full content here.
The scripts send the collected data in the POST request in the variable called marker_:
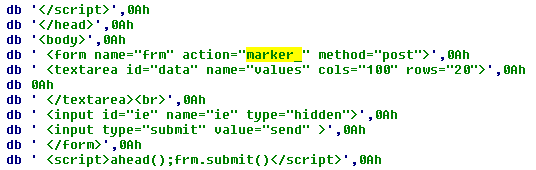
The data is received by the handler inside the TrickBot module:
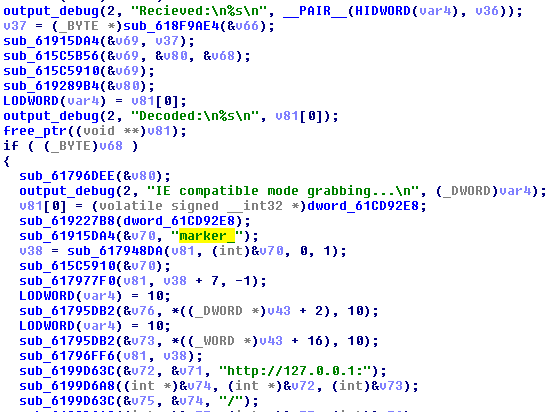
Interestingly, the malicious plugin also contains four base64-encoded pictures in PNG format:
Decoded pictures:

The SQL part
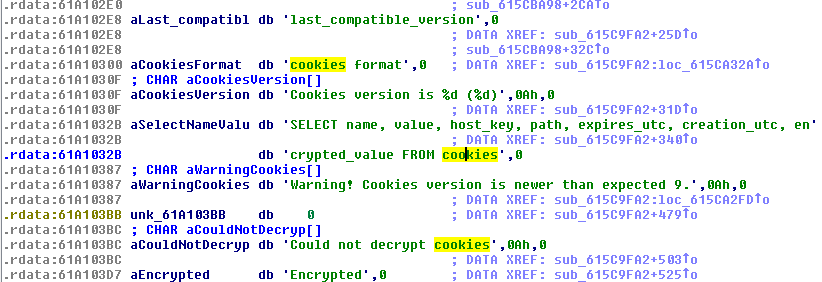
Among the data hardcoded within the module.dll we can find a string referencing an SQLite release:
2017-02-13 16:02:40 ada05cfa86ad7f5645450ac7a2a21c9aa6e57d2
The incorporated SQLite is used to retrieve and steal data such as cookies from locally stored databases (similar to Terdot Zbot, described here, that also incorporated SQLite for this purpose):”>
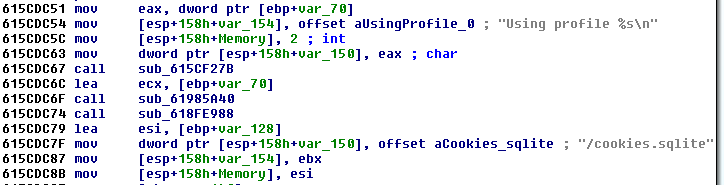
Sample strings and queries to the cookies database:
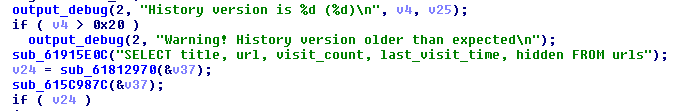
We can see also queries used for stealing the stored browsing history:
Outlook.dll
This is the module written in Delphi. It contains a hardcoded configuration that follows a pattern typical for TrickBot modules:Its purpose is to steal data saved by Microsoft Outlook.no
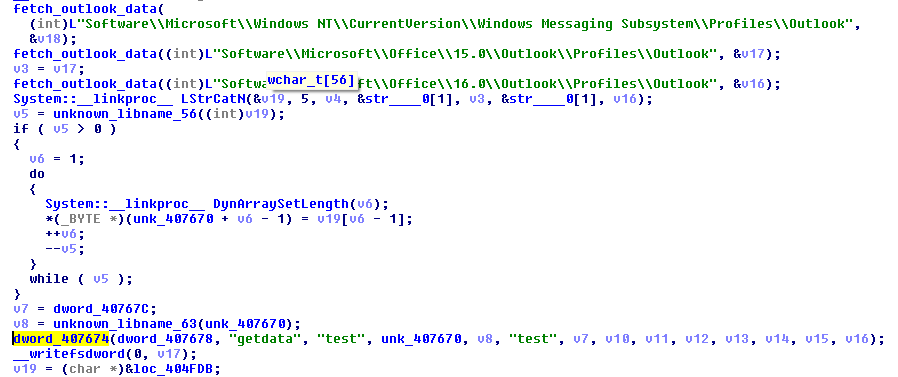
The module opens relevant registry keys and tries to retrieve saved credentials:
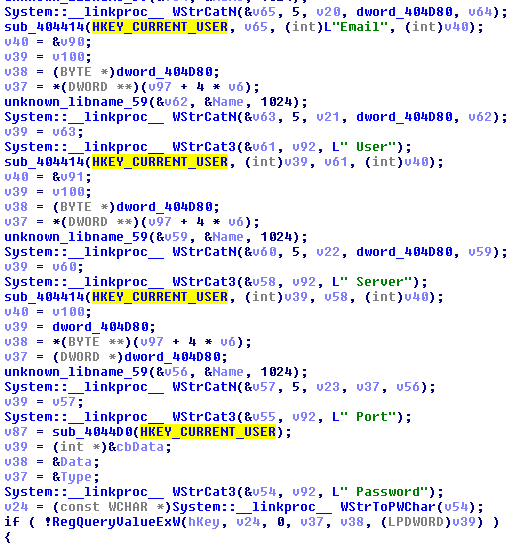
Not going away
TrickBot’s new modules are not written well and are probably still under development. The overall quality of the design is much lower than the quality of the earlier code. For example, module.dll is bulky and does not follow the clean modular structure introduced by TrickBot before. Also, they make use of languages and libraries that are easier, using Qt instead of native sockets for module.dll, and Delphi language for Outlook.dll.The differences in code, languages, and design may indicate that some changes were made to the development team. Either they gained new members who have been delegated to the new tasks, or some of the previous members resigned and have been substituted with lower quality programmers. It may also be possible that the malware authors are doing some prototyping and experimenting for the further development.
Whichever is the case, it’s clear that TrickBot is still actively maintained, and is not going to leave the threat landscape anytime soon.
This was a guest post written by hasherezade, an independent researcher and programmer with a strong interest in InfoSec. She loves describing malware in detail and sharing threat information with the community. Check her out on Twitter as well as on her personal blog, hasherezade’s 1001 nights.










