In Q1 and Q2 of 2017, we noticed a sharp decline in drive-by downloads coming from compromised websites. The campaigns of the past are either gone (Pseudo Darkleech) or have changed focus (EITest using social engineering techniques).
Malvertising – which has remained steady and is currently the main driving force behind some of the most common malware and scam distribution operations- not only stems from various publishers but also from ‘abandoned’ websites. Those related domains once served a legitimate purpose but were never renewed by their owners and fell into the hands of actors looking to make a quick profit using questionable practices.
In this post, we take a look at how malicious redirections from expired domains work and what kind of traffic they lead to.
The life, death, and resurrection of a domain name
Most issues when it comes to web security don’t usually come from the platforms themselves but from the people that run them or from properties that have simply been relinquished. The folks over at Sucuri have written about this extensively and in a recent post, they showed how expired domains and outdated plugins in popular CMS were a deadly mix, resulting in malicious redirects.
Here is an example of a website, oezelotel[.]com first registered to denizduezguen@yahoo.de on 03/10/2014, that once was advertising various hotels, was wiped in 2016, and eventually got parked as its domain name registration was never renewed.
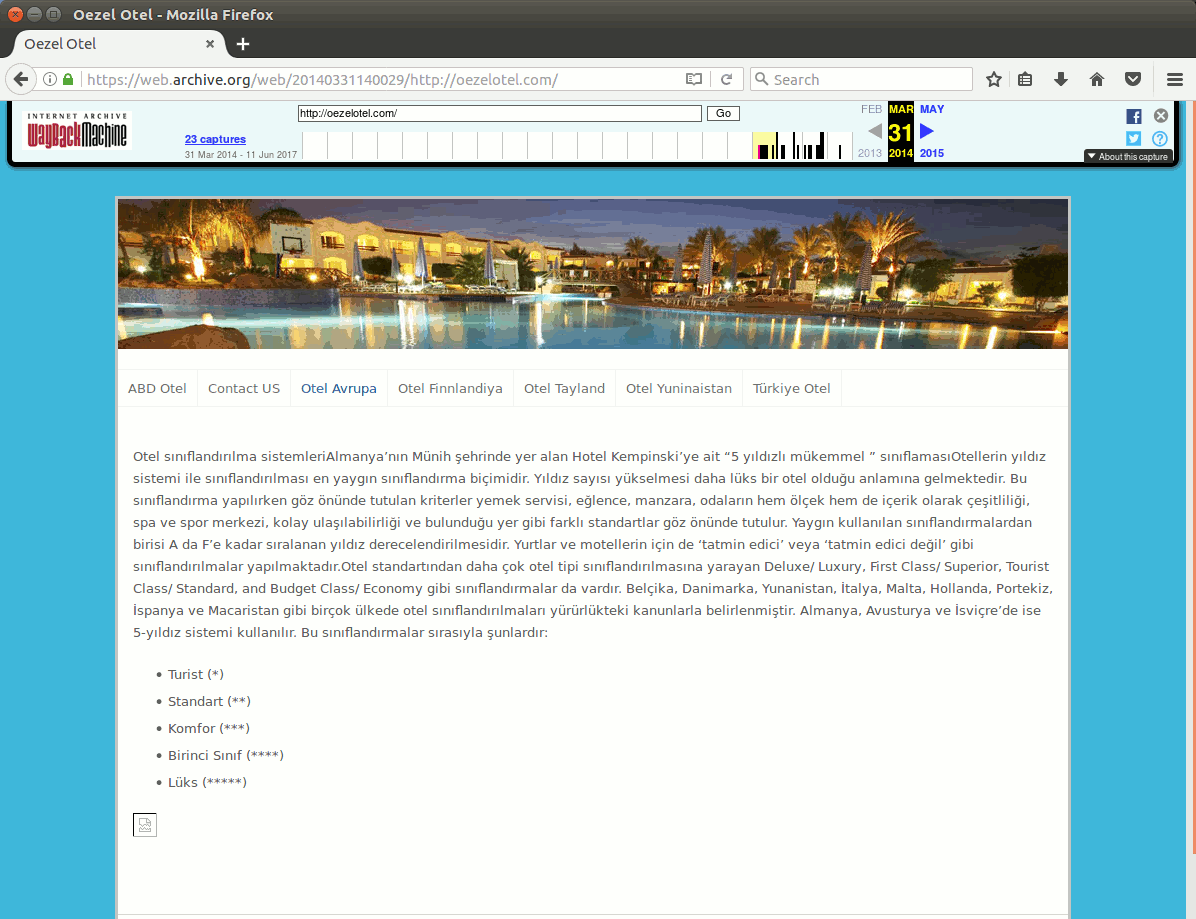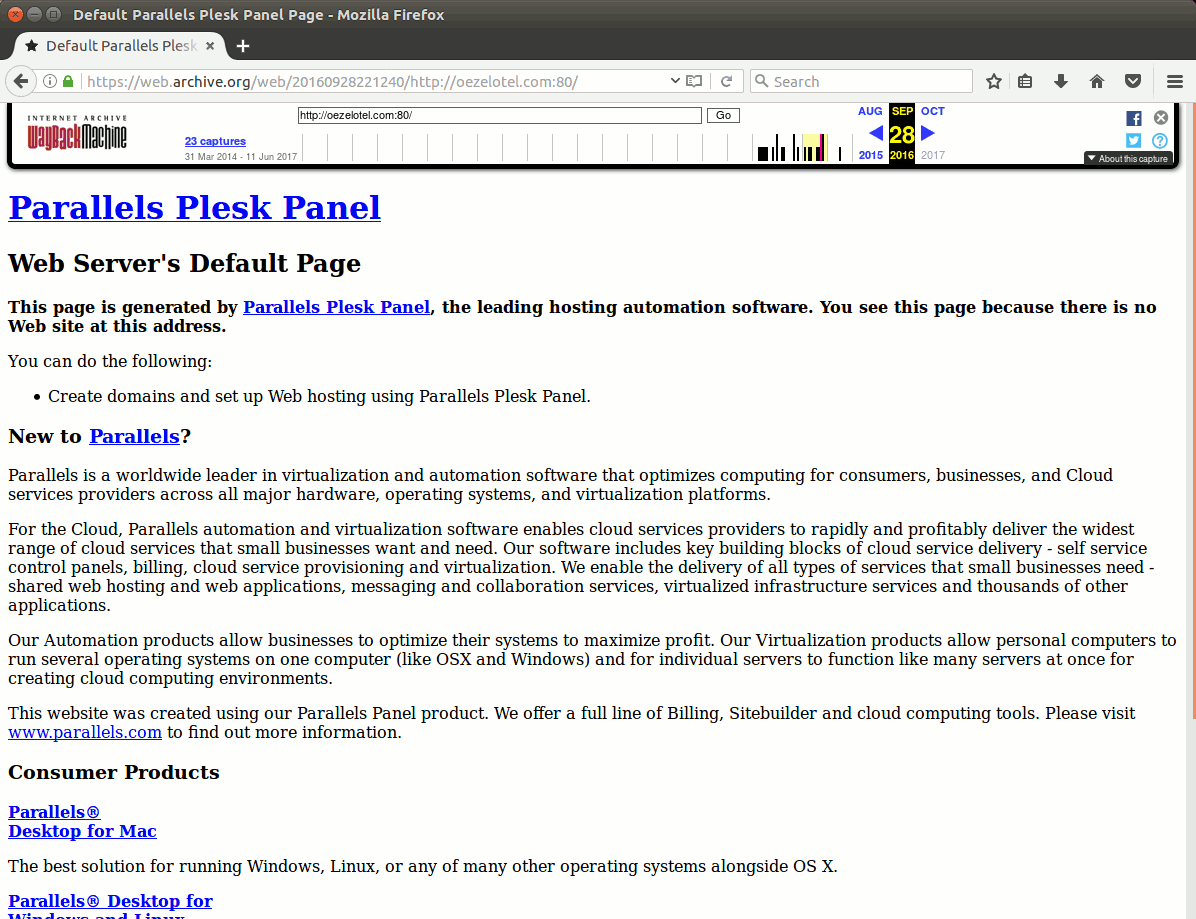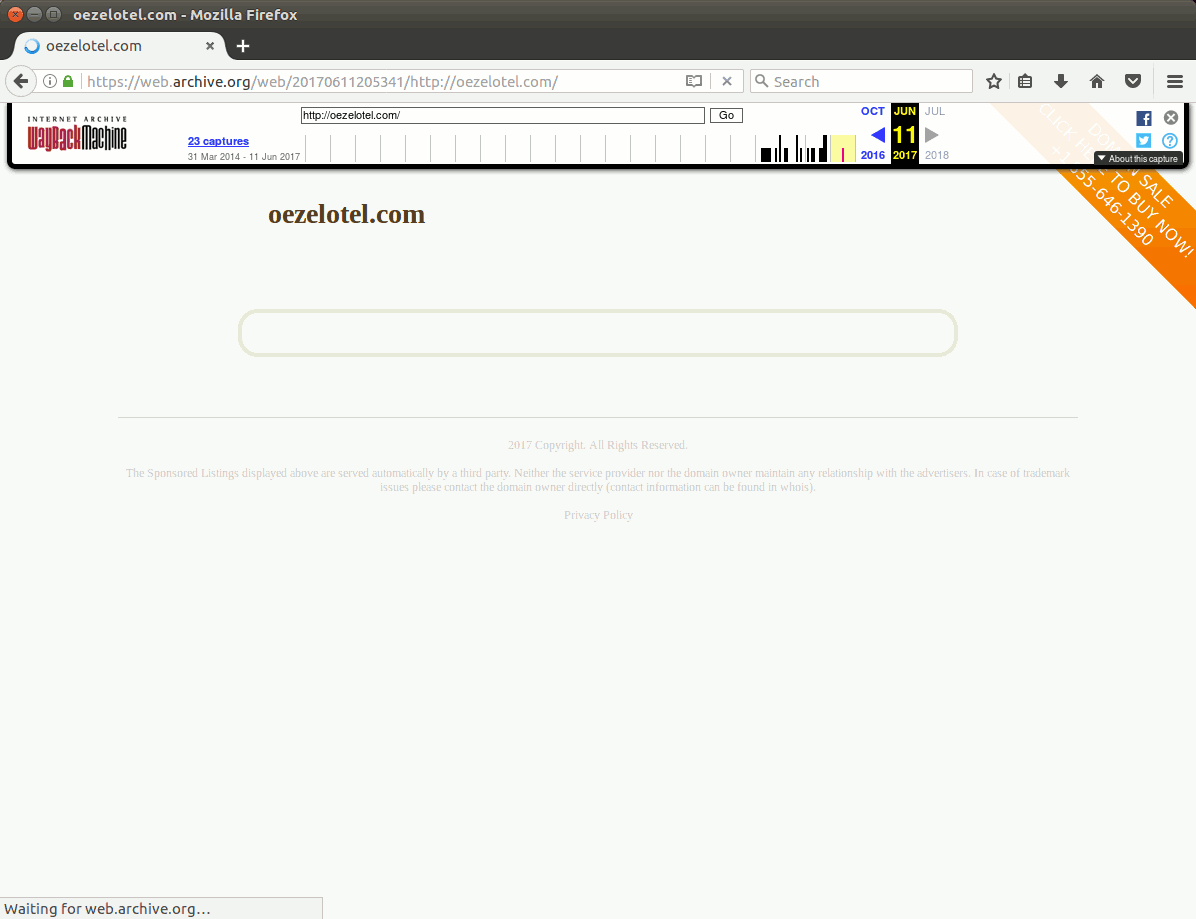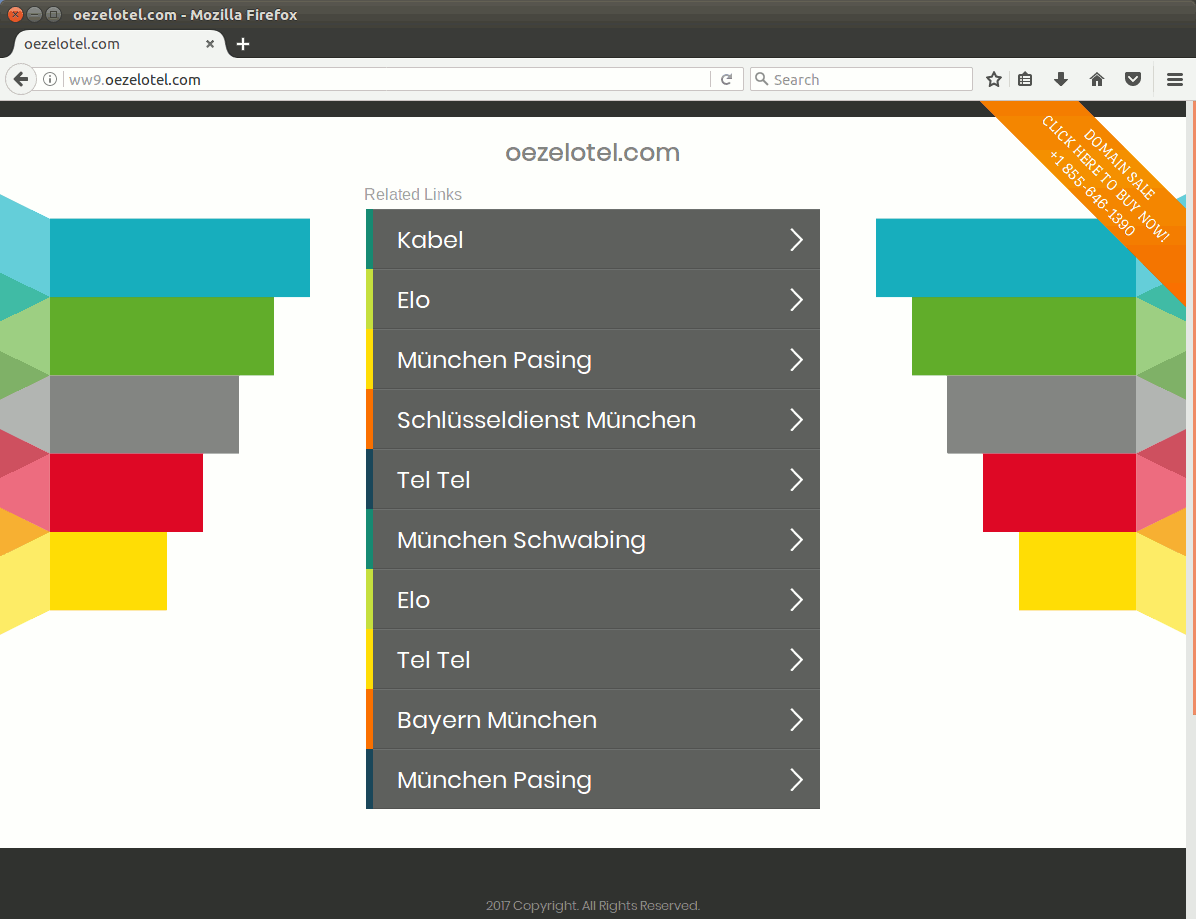
Figure 1: Evolution of a website over time and its eventual expired domain name
New owner, clear motive
A historical whois on the parked domain courtesy of Hyas’ Comox shows that on June 4, 2017, the domain name changed hands from its original owner to domainmanagers@outlook.com. This is also when the site changed hosting (moving from a Germany based server to a US one) and began exhibiting its malicious behavior.
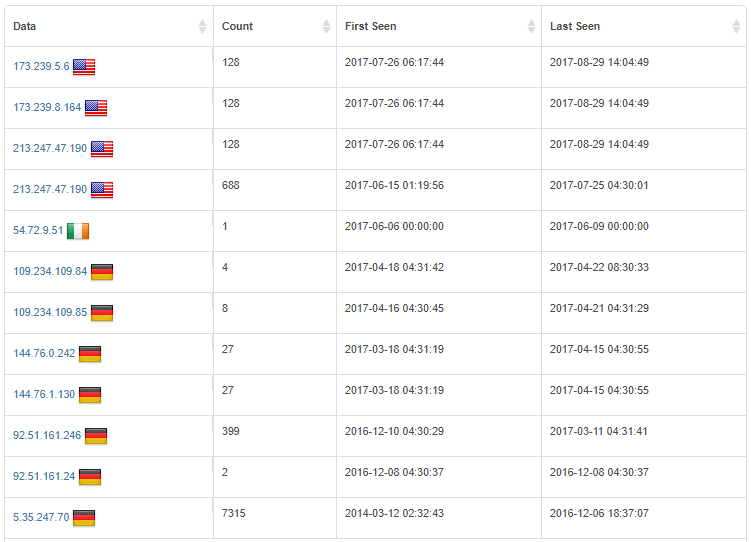
A cursory review of some other properties owned by the same registrant indicates a penchant for going after expired domains and monetizing them via dubious ad networks. DomainTools has over 23 K records belonging to that same email address.
Malvertising roulette
You might think a non-existent site is harmless but this couldn’t be further from the truth. Abandoned or forgotten domains are often registered and ‘parked’ to generate low-quality traffic (i.e. spammy links) as described in yet another blog post from Sucuri, and it is a real – lucrative – business model.
We observed different types of traffic, ranging from bogus surveys to more nefarious activity such as drive-by attacks and tech support scams, based on a visitor’s user agent. Note that the following examples did not require users to click on any link, the simple fact of visiting the site triggered an automatic redirection.
RIG EK Flow:
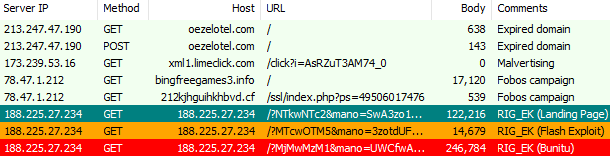
Figure 2: RIG exploit kit infection chain via the Fobos campaign that delivers the Bunitu Trojan.
oezelotel[.]com (parked site) -> xml1.limeclick[.]comLoading location.href='http://xml1.limeclick[.]com /click?i=SXRzS*SmiP4_0'; xml1.limeclick[.]com -> bingfreegames3[.]info212kjhguihkhbvd[.]cf -> 188.225.27.234 (RIG EK landing)
Tech Support Scam (TSS) flow:
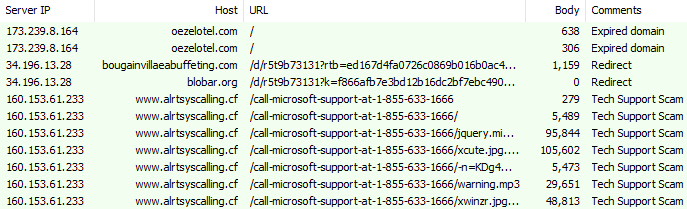
Figure 3: Redirection to tech support scam via blobar[.org]
oezelotel[.]com (parked site) -> bougainvillaeabuffeting[.]comLoading location.href='http://bougainvillaeabuffeting[.]com/d/ r5t9b73131?rtb={redacted}&subid=oezelotel.com';bougainvillaeabuffeting[.]com -> blobar[.]org document.write('');
blobar[.]org -> www.alrtsyscalling[.]cf (TSS landing) Location: https://www.alrtsyscalling[.]cf/call-microsoft-support-at-1-855-633-1666
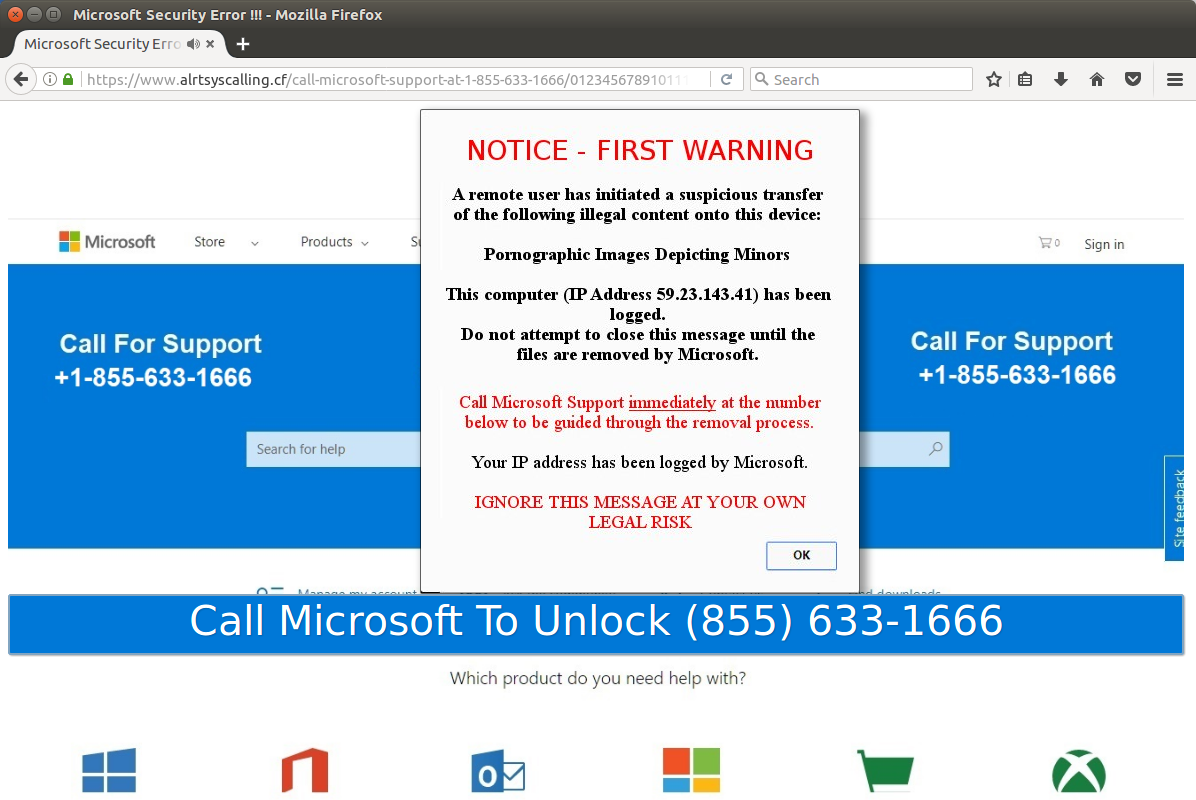
Figure 4: Browser locker serving a tech support scam page (IP address is hard coded in picture)
Traffic and user targeting
These days it seems irrelevant how malicious actors get their leads, so long as they are genuine users they can expose to malware or scams. An advantage of using ad networks and malvertising is that a lot of the filtering can be handled throughout the distribution chain, with remarkable efficiency, compared to server side checks on compromised sites.
Parked domains are one of many scenarios of hijacking traffic and monetizing it. While those practices raise eyebrows, are they actually illegal? Is it something that domain name registrars should enforce or ban? Those are interesting questions worth debating.
Malwarebytes blocks a lot of domains associated with malvertising as well as drive-by download attempts. Because we are witnessing more and more social engineering attacks, we highly recommend you spread the word about one of the most common scams today, the tech support scam.










