My curiosity was triggered when the telemetry of our heuristic scanner started showing a multitude of reports about a small file called grandfather.exe, so I went out to grab a copy and have a look at it.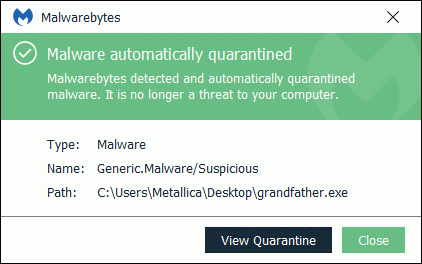
As you can probably tell from some of the detection names at Virustotal, this is a MSIL (Microsoft Intermediate Language) file. There are a lot of tools to decompile MSIL executables, but ILSpy is my personal favorite. To demonstrate why, I will show you how I analyzed this very small executable that is part of the Adware.Dotdo family.
Using ILSpy
Once you have downloaded and unzipped the binaries from their site, you can run ILSpy.exe and click File > Open to navigate to the file that you like to look at.
One advantage of ILSpy is that the code is shown in a very clear format. Even knowing how to read pseudocode and where to find .NET documentation will get you a long way, as I’m about to demonstrate.
The code in the example
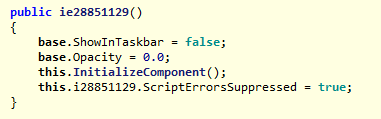
Code is shown in C# format
In this code slice, where the most important part of the program is initialized, we see three methods of hiding the program parts from the user:
- The program will not be shown in the taskbar
- The opacity is set at 0% which means you will see right through it
- And the program will not show any error prompts in case any script errors occur
By the way, if you are more comfortable with coding or reading code in VB.net, you can set ILSpy to show the code in that format.
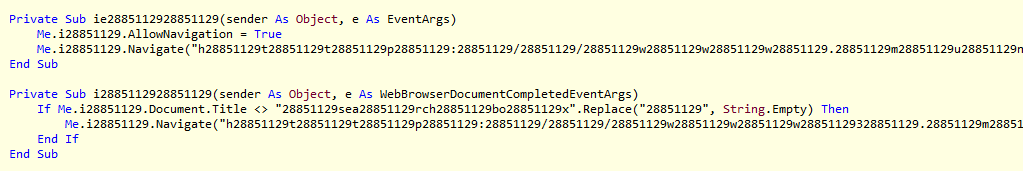
Code is shown in VB format (click to enlarge)
The strings in the code above have been obfuscated in a very simple way. Just enough to throw someone who is merely looking at strings off track.
After applyingReplace("28851129", string.Empty)), which is added to all the strings in that part of the code, this is what’s left of the two functions that will later be used as event handlers:
Private Sub ie(sender As Object, e As EventArgs)
Me.i.AllowNavigation = True
End Sub
The event handler above simply navigates to the obfuscated URL.
Private Sub i(sender As Object, e As WebBrowserDocumentCompletedEventArgs)
If Me.i.Document.Title <> "searchbox" Then
End If
End Sub
This event handler determines where the browser connects to, based on the title of the current document. If the title of the site does not match “searchbox” then it simply redirects the user to the URL that is obfuscated. If the title already is “searchbox” it will do nothing.
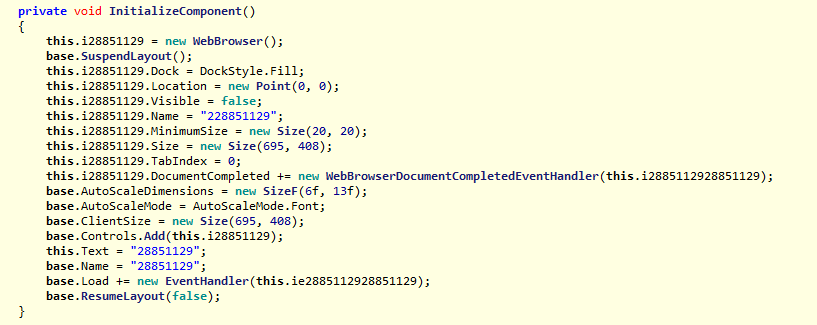
This is where the browser control (‘this’) is initialized while the layout of the main Window (‘base’) is postponed until the browser is ready to go. All the control’s edges are docked to the edges of its containing control and sized appropriately. The browser will resize to fit all of the empty space in its parent container with the DockStyle.Fill property set.
Then the location, size, and name are set, but also the control is hidden by setting the “.visible” property to “false”.
When the new document is fully loaded, the DocumentCompleted event occurs, and the event handler is the (lightly) obfuscated function we discussed earlier, so that will be triggered.
The AutoScaleDimensions property represents the DPI or font setting of the screen that the control was scaled to or designed for. Specifically, at design time this property will be set by the Windows Forms designer to the value your monitor is currently using. The “Font” is auto-scaled as well, relative to the dimensions of the font the classes are using, which is typically the system font.
Then after the browser control has been added to the base application, the first event handler is called which, as mentioned earlier, hides the main window and initializes the browser.
Summary
The “program” stays completely hidden from the user, but tries to contact two different websites on the same domain, probably with the intention to fetch further instructions. At the moment of writing, the site contains two iframes connecting to videojelly[.]com and whos.amung[.]us, a visitors counter.
I tried to show why I like ILSpy as a tool to decompile .NET and browse the assembly.
The file we looked at has:
SHA-256 53ac5aa31468ad9c14b179b8fd9ab2eed19cbbf2f5f4de97c9255be6f2af6240
Grandfather.exe is now detected as Adware.Dotdo.
Pieter Arntz











