Update (2017-12-05): We noted some malvertising chains using a new domain name (newadultthem[.]info) also hosted on the same IP address as the Punycode one.
– –
The Seamless campaign is one of the most prolific malvertising chains pushing the RIG exploit kit and almost exclusively delivering the Ramnit Trojan. Identification of Seamless is typically easy, due to its use of static strings and an IP literal URLs. However, for over a week now we have been seeing another Seamless campaign running in parallel, making use of special characters.
Rather than using an IP address, this Seamless chain uses a Cyrillic-based domain name, which is transcribed into recognizable characters via Punycode, a visual representation of Unicode. In this blog post, we’ll do a quick historical review of the Seamless gate and describe this latest iteration in a new format.
History
We noted redirections via adult sites around March 2017 (as pictured below) that were going through a new gate targeting Canada. Due to the presence of the string of the same name in its code, Cisco named this new campaign “Seamless.” Seamless dropped the Ramnit banking Trojan from the very beginning and still continues to do so.
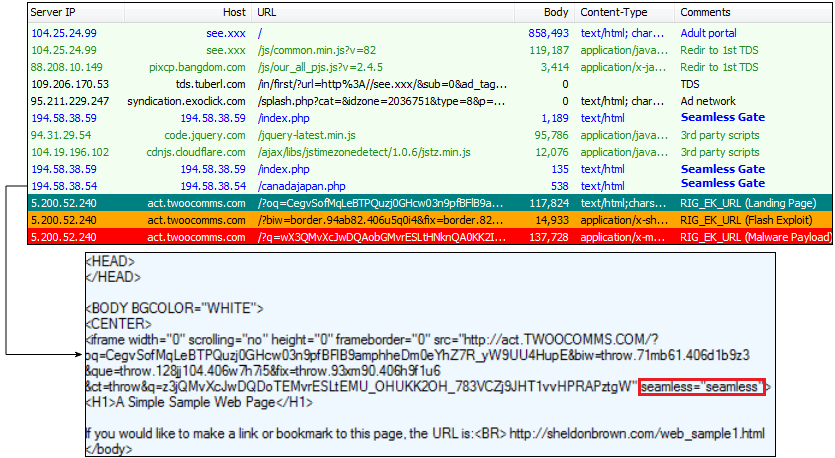
The URL patterns were typically:
194.58.39.195/flow2.php 194.58.42.235/flow335.php 185.31.160.55/flow336.php 193.124.18.78/signup2.php 194.58.38.54/canadajapan.php 194.58.38.31/japan.php 194.58.92.34/usa.php 194.58.47.235/signup1.php 194.58.47.235/signup2.php 194.58.47.235/signup3.php 194.58.47.235/signup4.php 194.58.40.48/signu3.php
These days, web traffic to Seamless still comes from adult portals serving malvertising, eventually redirecting to the same IP literal URLs containing the string test followed by three digits:
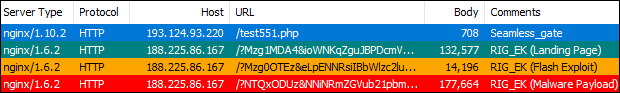
Seamless and Punycode
It wasn’t until recent years that domain registrars began to allow for non-English (ASCII) characters in domain names, defined by the Internationalized Domain Names (IDNs) for Applications framework. This allowed for countries to customize services with their own alphabets, which include what we’d otherwise call “special characters,” but have in fact existed long before the Internet was born.
Punycode is a representation of Unicode characters into ASCII used for hostnames, which allows for IDNs, while DNS lookups can still be performed using ASCII characters. The threat actors behind Seamless have been using a domain name containing Cyrillic characters (mostly found in Eastern European countries), which we noticed in our honeypot captures via its Punycode representation.
The call to the Seamless gate was initiated by a malvertising redirection:
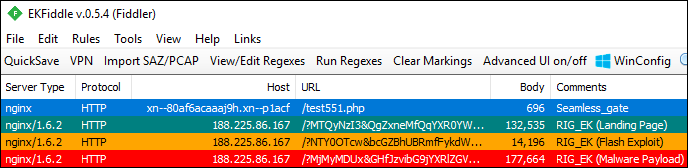
It is worth noting that Punycode has been exploited by scammers crafting phishing domain names resembling official brands, as sometimes certain Unicode characters are hard to distinguish from ASCII ones.
It is unclear whether this was a deliberate attempt to bypass intrusion detection systems or if it is simply an odd case similar to previous ones such as the Decimal IP campaign. Time will tell if the Seamless operators maintain it or abandon it in favor of the long-used IP literal URLs.
Indicators of compromise (IOCs)
Note: These IOCs are specific to the Punycode Seamless campaign.
URLs:
xn--80af6acaaaj9h .xn--p1acf/test441.php xn--80af6acaaaj9h .xn--p1acf/test551.php
IP address:
31.31.196.171
Payloads:
1609ab905f2ebbfe23b1111789cf8cade8b303642ecc5002ea63a3be24d2a07e 1a82f19a88827586a4dd959c3ed10c2c23f62a1bb3980157d9ba4cd3c0f85821 555f2d1665910e5d47ba45b0c8ec9eafaeb7c12868c5b76d52fcd0e17da248ec 58fb6436df51c59f8efe67b82e2a8a3af10faf798e9f4f047bac2fab1c1b0541 5943564ab3d38d4a9a0df32352dd5d2b04ccb76294e68a5efcbad5745d397de3 6fc5375161decbb23391e8302693437740765cf3e5e6f17afee9d720c22a1fac 79754c3bf6d5e40d89d2d81ba5a124b9ee13d924994fddeb170a50abd7f2be62 85c3822ab9254c8b52515869ca7430165142b37d05d4a41fe0293177098d44f2 888c88d190776cbf6bb010c2613c31428fb0779ed90f4f2bb8611a754a6bd44a a5d557f02bbf6454e912f7295f641985ec5535443a58bb163d7beadade854783 afe98c589e78abf76080ecdd1640f8e6e64f1f0244cfd4a1c216a4c0f8a9df24 b6c18ec6499e9671e0d80107e27485dee0ece626220a701570037407423f25c1 bba607dcf8d747daa2cb8d60986240caa932300dcf12da7073238822b3a1f42f bbea73e7b0d57969e45ef34667a016992f9295932e5b901858e3417593e080a2 d7b0ea1593eee67d43f5cd0a4472ac2cd12920a9ae2e87f29b02fafc98b00321 ec82f488d2c0c5f69f01c7d051081e8404f883cd4b63e57506d461c3e3926b0e f71411642bb2cdc1bb3da39d44d8f157bda0bdb853632174ec3796b9d3b500f5 f766d034b8579922fceb9a0c50b7ea7799ed6d9ed79acc8fcc08abea129b6f4a










