Browlocks are the main driving force behind tech support scams, using a combination of malvertising and clever browser locker tricks to fool users. In fact, the effects can be so convincing that people call the rogue Microsoft support number for help because they believe their computer has been hijacked.
Crooks are constantly trying out new tricks to defeat modern browsers and evade detection. Recently we’ve seen the “evil cursor” that prevents you from closing the fake alert, and the fake virus download that insinuates your computer is already infected. This time, we look at how browser locker pages use encoding to bypass signature-based detection.
Encoding and other obfuscation types
The use of Base64 or hex encoding to hide malicious scripts is as old as the moon. Malware authors have been relying on those to make identification of malicious code much more difficult for both human eyes and scanners.
Tech support scammers have been no stranger to leveraging obfuscation within their browser locker templates. For instance, by using this hexadecimal encoding below, the crooks can mask the fake warning message from prying eyes:
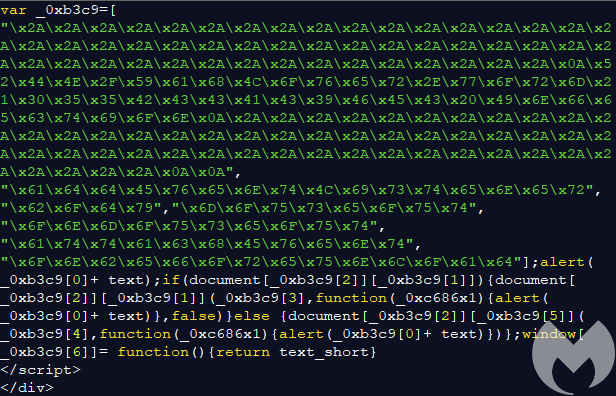
However, browsers can read and decode the hex encoded content and display it to the user as the following (fake) alert:
************************************************* RDN/YahLover.worm!055BCCAC9FEC Infection *************************************************
Not all tech support scam browlocks use obfuscation, but over the years it has become more common to see parts of the code being hidden. What we haven’t really seen is complete encoding of the browlock page such that almost no artifacts are present.
Soup to nuts encoding
We recently came upon a browlock template reported on Reddit that has taken encoding to a whole new level, on top of using the aforementioned unpatched, existing techniques. Its source code page is beautifully simple and yet effective:
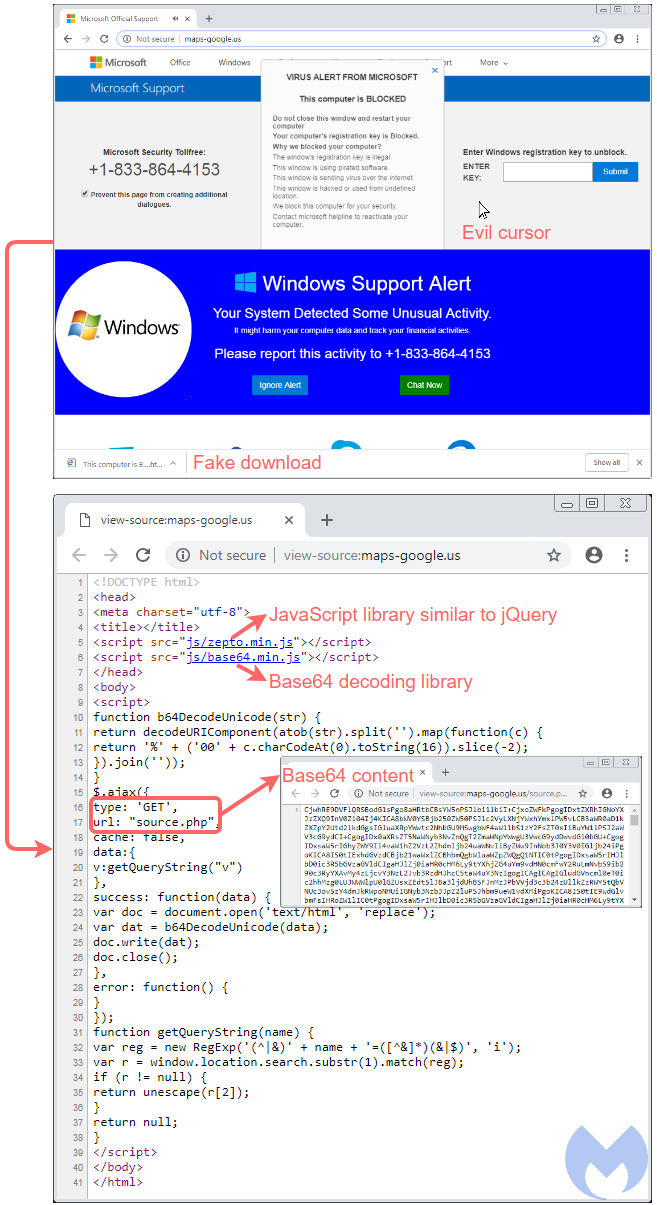
We can see two JavaScript libraries that are being retrieved. One is called Zepto.js, which according to its author is “a minimalist JavaScript library for modern browsers with a largely jQuery-compatible API.” The more interesting library is this base64.min.js file, which gets Base64 encoded content and decodes it on the fly. Note how this data is not loaded from the main page but rather from a following GET request:
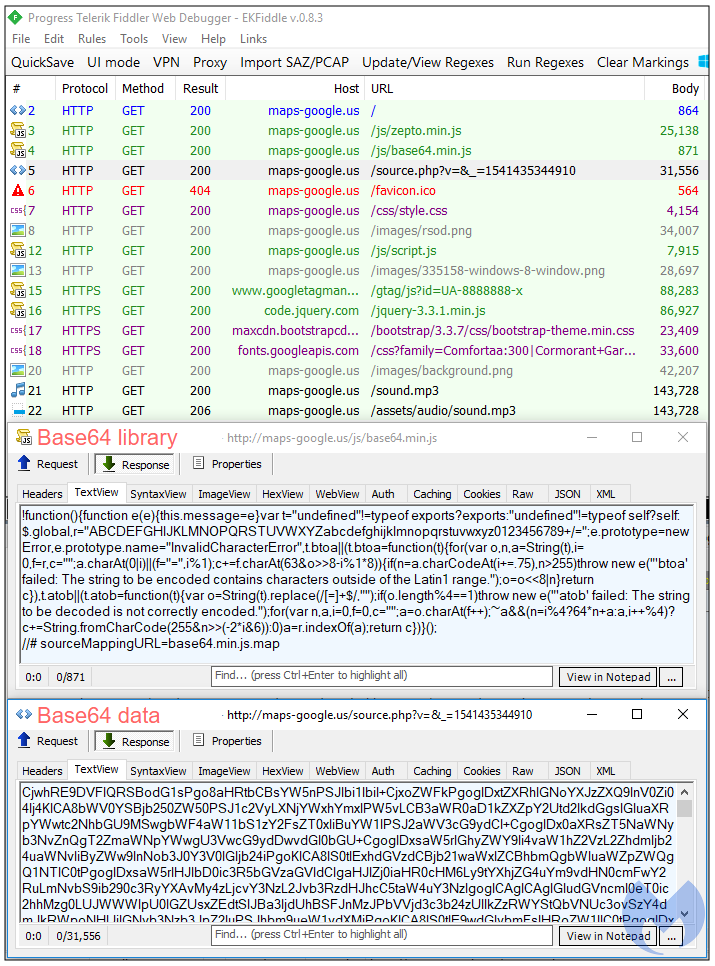
There is no denying that crooks are once again trying to play cat and mouse with defenders. Perhaps as a tongue-in-cheek gesture, they even created a bogus Google Analytics tracker ID: gtag(‘config’, ‘UA-8888888-x’), in addition to using the maps-google[.]us Google look-alike domain.
For end users, it is important to remember that no matter how scary a warning looks or even sounds, the best course of action is to remain calm and take the time to check on it before overreacting and dialing a scammer’s hot line. These browlocks are not causing any damage to the computer and can be closed one way or another. The more annoying ones still require using the Task Manager to kill the offending process, which is why we hope browser vendors take these issues seriously to restore power to the user. But otherwise, taking time to investigate does no harm, no foul.
Malwarebytes Browser Extension is not fooled by this obfuscation trick and already protects users from this browlock.










