In the months since our last spring review, there has been some interesting activity from several exploit kits. While the playing field remains essentially the same with Internet Explorer and Flash Player as the most-commonly-exploited pieces of software, it is undeniable that there has been a marked effort from exploit kit authors to add some rather cool tricks to their arsenal.
For example, several exploit kits are using session-based keys to prevent “offline” replays. This mostly affects security researchers who might want to test the exploit kit in the lab under different scenarios. In other words, a saved network capture won’t be worth much when it comes to attempting to reenact the drive-by in a controlled environment.
The same is true for better detection of virtual machines and network tools (something known as fingerprinting). Combining these evasion techniques with geofencing and VPN detection makes exploit kit hunting more challenging than in previous quarters.
Threat actors continue to buy traffic from ad networks and use malvertising as their primary delivery method. Leveraging user profiling (their browser type and version, country of origin, etc.) from ad platforms, criminals are able to maintain decent load rates (successful infection per drive-by attempts).
Summer 2019 overview
- Spelevo EK
- Fallout EK
- Magnitude EK
- RIG EK
- GrandSoft EK
- Underminer EK
- GreenFlash EK
Vulnerabilties
Internet Explorer’s CVE-2018-8174 and Flash Player’s CVE-2018-15982 are the most common vulnerabilities, while the older CVE-2018-4878 (Flash) is still used by some EKs.
Spelevo EK
Spelevo EK is the youngest exploit kit, originally discovered in March 2019, but by no means is it behind any of its competitors.
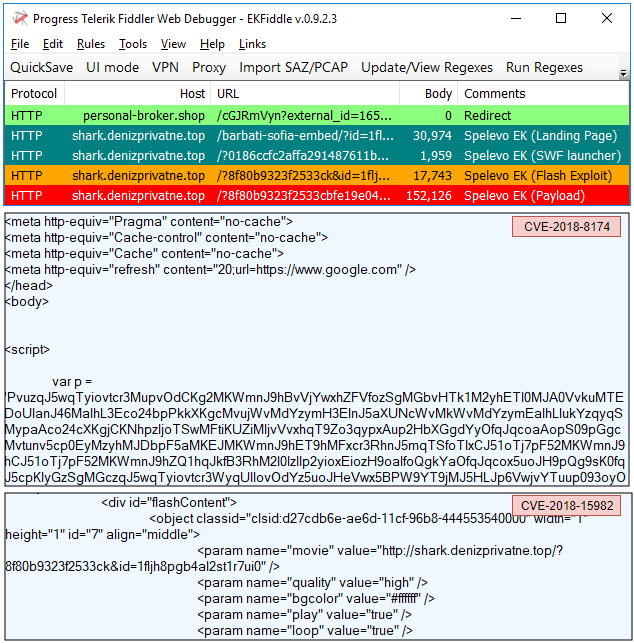
Payloads seen: PsiXBot, IcedID
Fallout EK
Fallout EK is perhaps one of the more interesting exploit kits. Nao_Sec did a thorough writeup on it recently, showing a number of new features in its version 4 iteration.
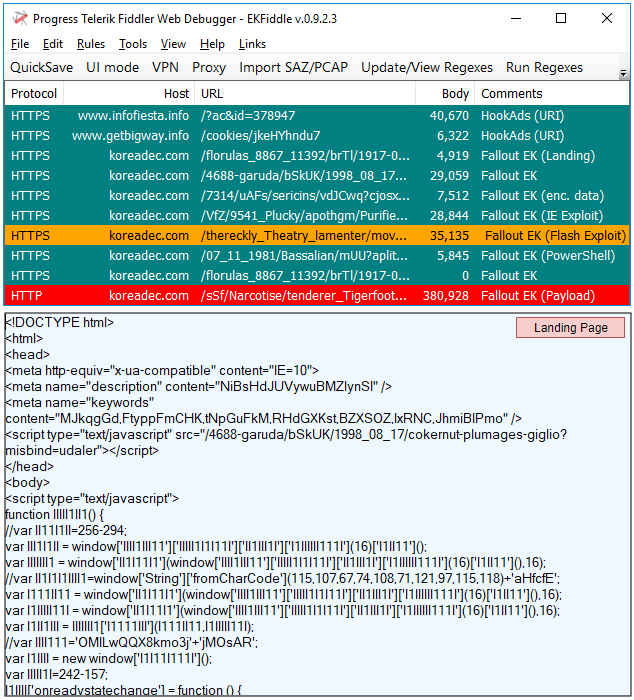
Payloads seen: AZORult, Osiris, Maze ransomware
Magnitude EK
Magnitude EK continues to target South Korea with its own Magniber ransomware in steady malvertising campaigns.
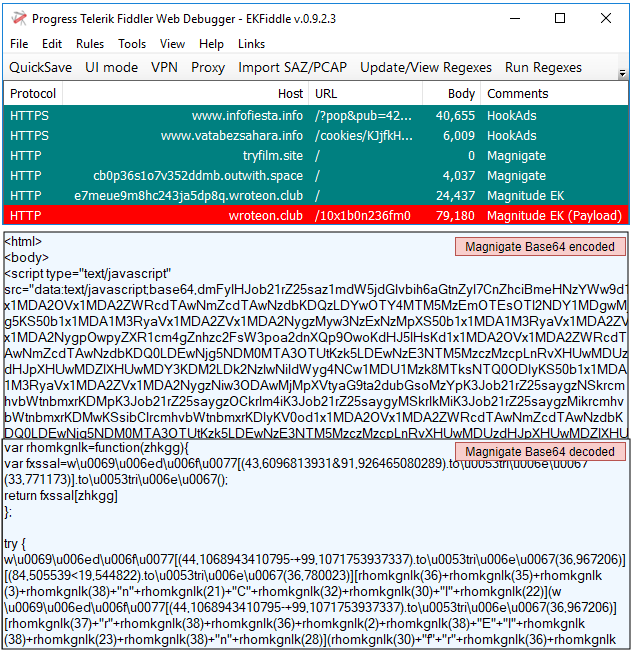
Payload seen: Magniber ransomware
RIG EK
RIG EK is still kicking around via various malvertising chains and perhaps offers the most diversity in terms of the malware payloads it serves.
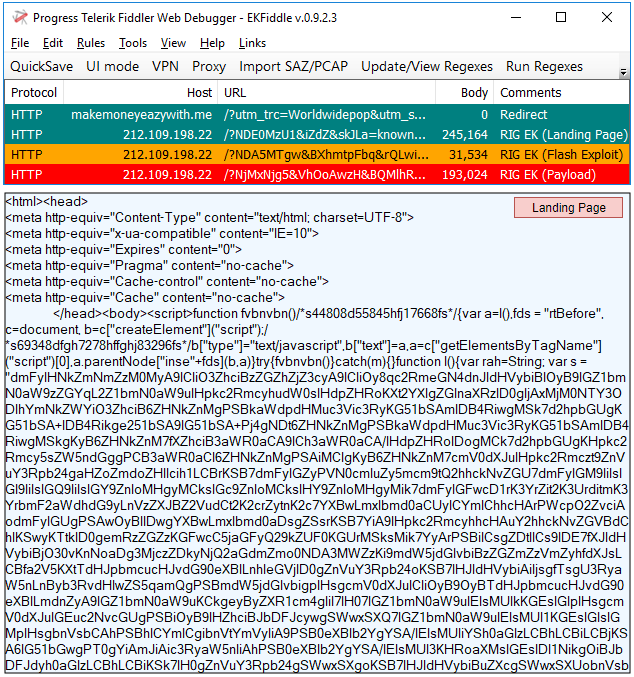
Payloads seen: ERIS, AZORult, Phorpiex, Predator, Amadey, Pitou
GrandSoft EK
GrandSoft EK remains the weakest exploit kit of the bunch and continues to drop Ramnit in Japan.
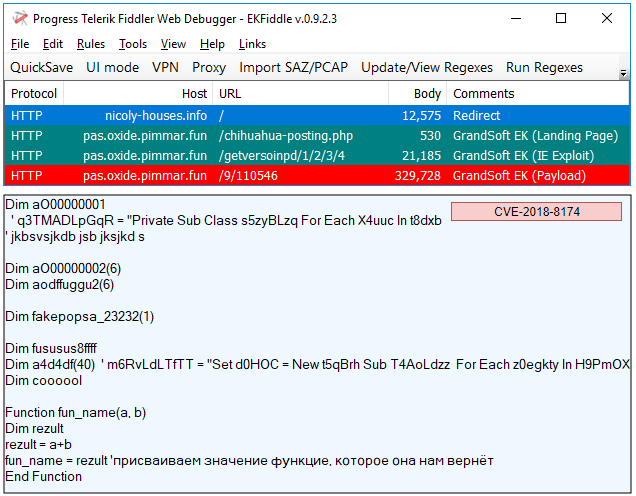
Payload seen: Ramnit
Underminer EK
Underminer EK is a rather complex exploit kit with a complex payload which we continue to observe via the same delivery chain.
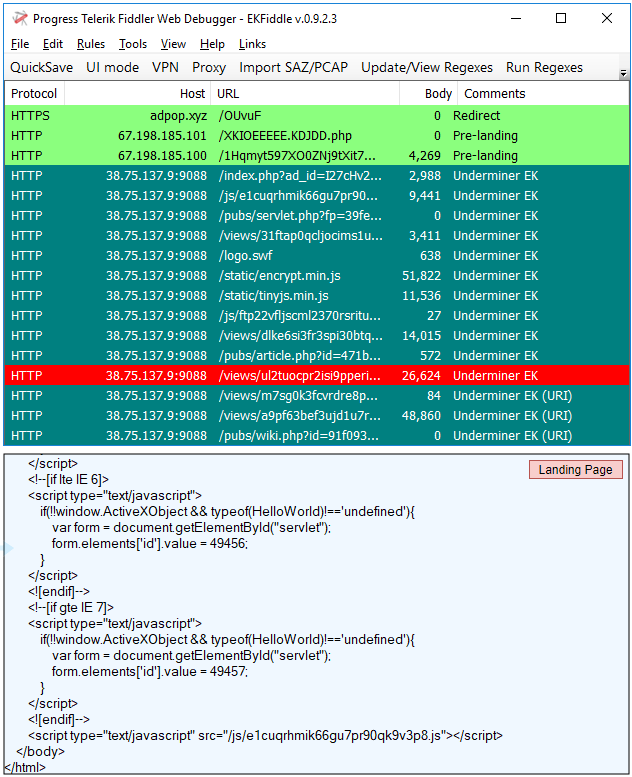
Payload seen: Hidden Bee
GreenFlash Sundown EK
The elusive GreenFlash Sundown EK marked a surprise return via its ShadowGate in a large malvertising campaign in late June.
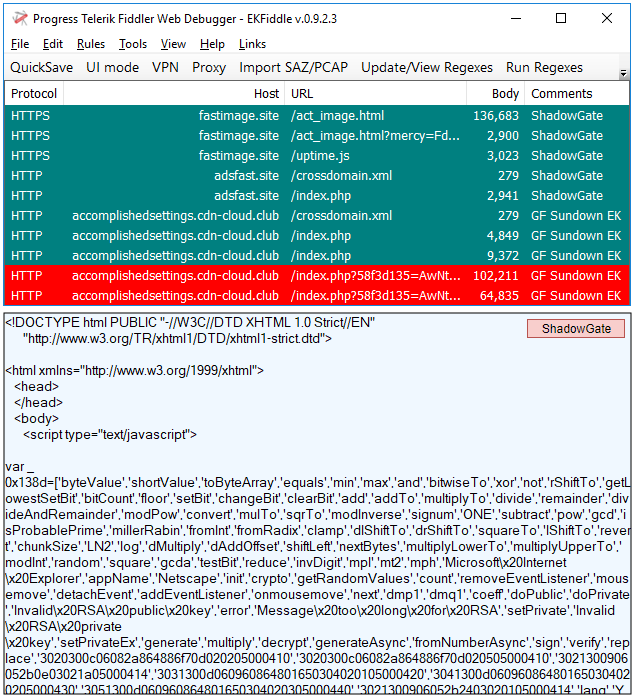
Payloads seen: Seon ransomware, Pony, coin miner
Pseudo-EKs
A few other drive-bys were caught during the past few months, although it might be a stretch to call them exploit kits.
- azera drive-by used the PoC for CVE-2018-15982 (Flash) to drop the ERIS ransomware
- Radio EK leveraged CVE-2016-0189 (Internet Explorer) to drop AZORult
Three years since Angler EK left
June 2016 is an important date for the web threat landscape, as it marks the fall of Angler EK, perhaps one of the most successful and sophisticated exploit kits. Since then, exploit kits have never regained their place as the top malware delivery vector.
However, since our spring review, we can say there have been some notable events and interesting campaigns. While it’s hard to believe that users are still running machines with outdated Internet Explorer and Flash Player versions, this renewed activity proves us wrong.
Although we have not mentioned router-based exploit kits in this edition, they are still a valid threat that we expect to grow in the coming months. Also, if exploit kit developers start branching out of Internet Explorer more, we could see far more serious attacks.
Malwarebytes users are protected against the aforementioned drive-by download attacks thanks to our products’ anti-exploit layer of technology.
Indicators of Compromise (URI patterns)
Spelevo EK
hxxp[://]shark[.]denizprivatne[.]top/barbati-sofia-embed/?id=1fljh8pgb4al2st1r7ui0
hxxp[://]shark[.]denizprivatne[.]top/?0186ccfc2affa291487611b&id=1fljh8pgb4al2st1r7ui0
hxxp[://]shark[.]denizprivatne[.]top/?8f80b9323f2533ck&id=1fljh8pgb4al2st1r7ui0
hxxp[://]shark[.]denizprivatne[.]top/?8f80b9323f2533cbfe19e0483c81dc8b72294a&id=1fljh8pgb4al2st1r7ui0
Fallout EK
hxxps[://]koreadec[.]com/florulas_8867_11392/brTl/1917-08-03[.]phtml?Patining=eEo
hxxps[://]koreadec[.]com/4688-garuda/bSkUK/1998_08_17/cokernut-plumages-giglio?misbind=udaler
hxxps[://]koreadec[.]com/7314/uAFs/sericins/vdJCwq?cjosx=Sturnine-amadous-6883
hxxps[://]koreadec[.]com/VfZ/9541_Plucky/apothgm/Purified-Beatifies[.]xhtml?carafe=9109&TIo=nepotious-5579-10022&STlvZ=6372
hxxps[://]koreadec[.]com/thereckly_Theatry_lamenter/movant-13555-Procotton/11235/6428-14646-9953?XG53=ethanes-ekename-aldeament&Betwixt=untoggler-6715-anoles&aHvBI=2guk
hxxps[://]koreadec[.]com/07_11_1981/Bassalian/mUU?aplites=zH1Koq&fBRR=7541_9162_witterly
hxxps[://]koreadec[.]com/florulas_8867_11392/brTl/1917-08-03[.]phtml?Patining=eEo
hxxp[://]koreadec[.]com/sSf/Narcotise/tenderer_Tigerfoot_Spackle
Magnitude EK
hxxp[://]tryfilm[.]site/
hxxp[://]cb0p36s1o7v352ddmb[.]outwith[.]space/
hxxp[://]e7meue9m8hc243ja5dp8q[.]wroteon[.]club/
hxxp[://]wroteon[.]club/10x1b0n236fm0
RIG EK
hxxp[://]212[.]109[.]198[.]22/?NDE0MzU1&iZdZ&skJLa=known&ljQicPIO=criticized&PbvRlP=detonator&t4gfhtgf4=xfQlKrcFPArhjUODfwIwyIZaUVwb96n8ikbXwRPJgJ_UrxSLNwJEqaKlJLd_mhj2&bmSJmU=vest&IabEYxV=strategy&ffffghds=w3nQMvXcJxfQFYbGMvPDSKNbNknWHViPxomG9MildZeqZGX_k7XDfF-qoVrcCgWR&qRrScLDp=difference&tNEKEWCG=known&qAVUDc=criticized&RWWa=already&NAaUs=difference&tqHbh=referred&XSZz=professional&QqbDBluKn=referred&riObvJqGb=heartfelt&RTXBW=difference&QEcvAFNjYzNTc=
hxxp[://]212[.]109[.]198[.]22/?NDA5MTgw&BXhmtpFbq&rQLwisIbKvO=constitution&yMpSuTkuRhu=known&EPxLjfEgMobx=perpetual&nxAaNt=strategy&VKoMoenBvZEBoJ=already&t4gfhtgf4=8vUoeLNQPQXihEHRLw1mn4ZUUlpB86umi0aAyUDOgZHU-xTbUQ5G_5qcFoF4nwvF&ffffghds=wXbQMvXcJwDQA4bGMvrESLtMNknQA0KK2Ij2_dqyEoH9fGnihNzUSkr76B2aCm3Z&EuhiAT=strategy&IIwiBsrVTzN=community<SPgukgZMu=golfer&WHJVKfgHYyhBKA=already&ruFaROBjfxdFlTw=referred&erHmTrM=community&rZYXaPLBZQZ=constitution&alUaYovES=referred&PAmrMcgpepI=golfer&kWSrADlsss=professional&xftTftqdNDIyNjk0
hxxp[://]212[.]109[.]198[.]22/?NjMxNjg5&VhOoAwzH&BQMlhROymiqqMuw=blackmail&GhAssHkhgxqw=community&DegGfd=perpetual&gquWWCtuJtSPU=known&rAGXUesC=perpetual&zLRRtbwijFH=heartfelt&CIklccbXNmonSm=detonator&gaxgBSvwPv=heartfelt&sHkEPhjzv=constitution&EKoVAfMMJrfDqut=community&YDYZAvpVWZjDdO=blackmail&QRRmDFtTZ=blackmail&ffffghds=w3bQMvXcJxfQFYbGMv3DSKNbNkfWHViPxoeG9MildZmqZGX_k7rDfF-qoVvcCgWRxfUlKr&yuImXnAAw=professional&CFnDimnJDGPFi=wrapped&t4gfhtgf4=cFPArhjUODfwIwyIZaUV0b96n8ikbXwRPJgJ_UrxSLNwJEqaKcHbYy0VT8xrkdQJZnxBCy&NrzaCYKBrsfbC=golfer&WYYKaQVuhFBMjM2MDg4
GrandSoft EK
hxxp[://]pas[.]oxide[.]pimmar[.]fun/chihuahua-posting[.]php
hxxp[://]pas[.]oxide[.]pimmar[.]fun/getversoinpd/1/2/3/4
hxxp[://]pas[.]oxide[.]pimmar[.]fun/9/110546
Underminer EK
hxxp[://]67[.]198[.]185[.]101/XKIOEEEEE[.]KDJDD[.]php
hxxp[://]67[.]198[.]185[.]100/1Hqmyt597XO0ZNj9tXit7HZOMroEJu8c[.]php
hxxp[://]38[.]75[.]137[.]9:9088/index[.]php?ad_id=I27cHv2i8QxDkXOJWhnMGw&re=I27cHv2i8QxDkXOJWhnMGw&rt=I27cHv2i8QxDkXOJWhnMGw&id=9088&zone=I27cHv2i8QxDkXOJWhnMGw&prod=I27cHv2i8QxDkXOJWhnMGw&lp=Type&st=I27cHv2i8QxDkXOJWhnMGw&e=1563981076&y=203384173015
hxxp[://]38[.]75[.]137[.]9:9088/js/e1cuqrhmik66gu7pr90qk9v3p8[.]js
hxxp[://]38[.]75[.]137[.]9:9088/pubs/servlet[.]php?fp=39fe6ccb473b08362ae067b8c0ee865d&lang=en-US&token=&id=49457&sign=5eed006ae06584a03f969b9cd3558c28&validate=13b96b0bb8ac2a105d07f7c8b701f240
hxxp[://]38[.]75[.]137[.]9:9088/views/31ftap0qcljocims1ubickgps8[.]html
hxxp[://]38[.]75[.]137[.]9:9088/logo[.]swf
hxxp[://]38[.]75[.]137[.]9:9088/static/encrypt[.]min[.]js
hxxp[://]38[.]75[.]137[.]9:9088/static/tinyjs[.]min[.]js
hxxp[://]38[.]75[.]137[.]9:9088/js/ftp22vfljscml2370rsritui9g[.]js
hxxp[://]38[.]75[.]137[.]9:9088/views/dlke6si3fr3spi30btq624ghlg[.]html
hxxp[://]38[.]75[.]137[.]9:9088/pubs/article[.]php?id=471b68c405614637d03b31b4d3155244
hxxp[://]38[.]75[.]137[.]9:9088/views/ul2tuocpr2isi9pperindatp3c[.]ocx[.]gz
hxxp[://]38[.]75[.]137[.]9:9088/views/m7sg0k3fcvrdre8psojjlu8r2c[.]txt
hxxp[://]38[.]75[.]137[.]9:9088/views/a9pf63bef3ujd1u7r6v9dda0mk[.]wav
hxxp[://]38[.]75[.]137[.]9:9088/pubs/wiki[.]php?id=91f093921cbb802ee2d2a22d8a4a1135
GreenFlash Sundown EK
hxxps[://]fastimage[.]site/act_image[.]html
hxxps[://]fastimage[.]site/act_image[.]html?mercy=FdMzpfikLihAnNPppGIucrCHLfiIPE0UYY9ocxDP7RzUlUu6%2BcEavY5yGiQn8ogYce3E0sgs06B1y9%2BnxZhQCg%3D%3D&liberty=djji1ghk3gtx&bubble=RUDOpbnkAS1xQHVxflacRzfZxQ%3D%3D
hxxps[://]fastimage[.]site/uptime[.]js
hxxp[://]adsfast[.]site/crossdomain[.]xml
hxxp[://]adsfast[.]site/index[.]php
hxxp[://]accomplishedsettings[.]cdn-cloud[.]club/crossdomain[.]xml
hxxp[://]accomplishedsettings[.]cdn-cloud[.]club/index[.]php
hxxp[://]accomplishedsettings[.]cdn-cloud[.]club/index[.]php
hxxp[://]accomplishedsettings[.]cdn-cloud[.]club/index[.]php?58f3d135=AwNt6IfxFIvMI5IVpwl86cW8Vw67HxZLI%2BxIxOVtVcp5LRaaMtmhuElGqOGKWUki92GcJmgL0gwOElyFUkW%2FzdQ1y8Ov8MxNATzL7HlkXp5%2FtFmbrh3TWgiJ1QvTmcEwbx66CaLWd2ekFpng2ky4fKUtGRibaY8Eyjcio3ZyibnhUVlW5CpiWNiz02jHD41t%2F9NDPteWGIO1ysm2%2B4%2Bu9osgKIW1%2BmGxVxMGaRby3g%2FBaqw%3D
hxxp[://]accomplishedsettings[.]cdn-cloud[.]club/index[.]php?58f3d135=AwNt6IfxFIvMI5IVpwl86cW8Vw67HxZLI%2BxIxOVtVcp5LRaaMtmhuElGqOGKWUki92GcJmgL0gwOElyFUkW%2FzdQ1y8Ov8MxNATzL7HlkXp5%2FtFmbrh3TWgiJ1QvTmcEwbx66CaLWd2ekFpng2ky4fKUtGRibaY8Eyjcio3ZyibnhUVlW5CpiWNiz02jHD41t%2F9NDPteWGIO1ysu3%2Fo%2Bt9IsgKIW1%2BmGxVxMGaRby3g%2FBaqw%3D










