Sodinokibi ransomware, also known as Sodin and REvil, is hardly three months old, yet it has quickly become a topic of discussion among cybersecurity professionals because of its apparent connection with the infamous-but-now-defunct GandCrab ransomware.
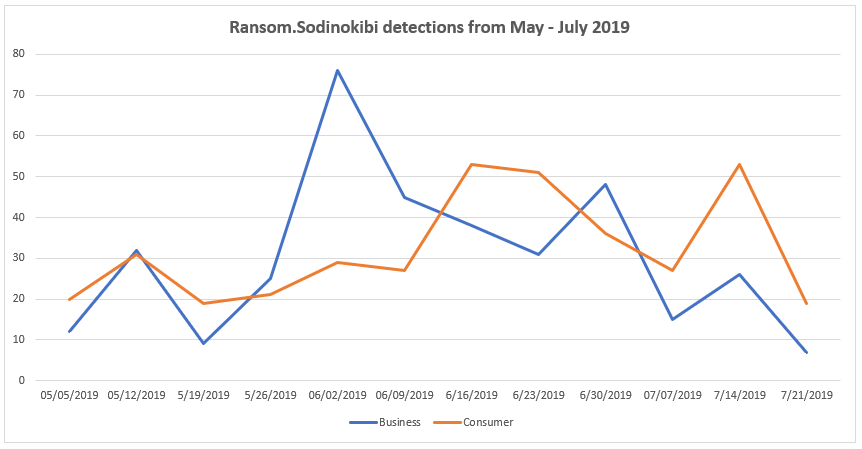
Detected by Malwarebytes as Ransom.Sodinokibi, Sodinokibi is a ransomware-as-a-service (RaaS), just as GandCrab was, though researchers believe it to be more advanced than its predecessor. We’ve watched this threat target businesses and consumers equally since the beginning of May, with a spike for businesses at the start of June and elevations in consumer detections in both mid June and mid July. Based on our telemetry, Sodinokibi has been on rise since GandCrab’s exit at the end of May.
On May 31, the threat actors behind GandCrab formally announced their retirement, detailing their plan to cease selling and advertising GandCrab in a dark web forum post.
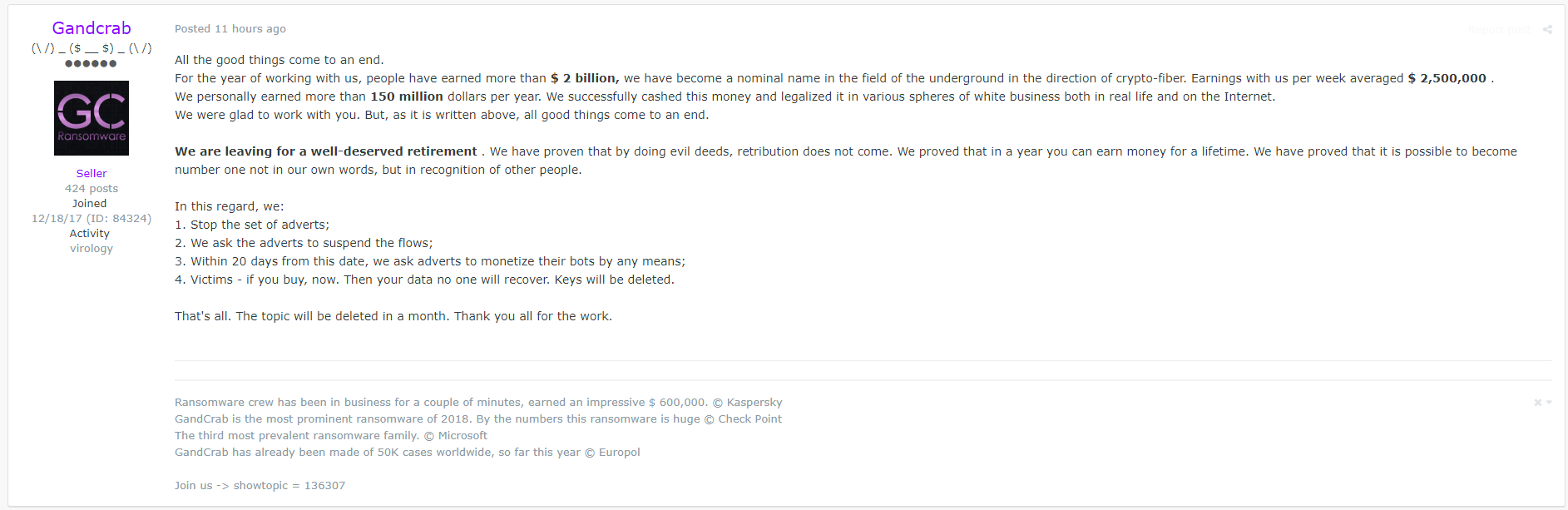
While many may have heaved sighs of relief at GandCrab’s “passing,” some expressed skepticism over whether the team would truly put behind their successful money-making scheme. What followed was bleak anticipation of another ransomware operation—or a re-emergence of the group peddling new wares—taking over to fill the hole GandCrab left behind.
Enter Sodinokibi
Putting a spin on an old product is a concept not unheard of in legitimate business circles. Often, spinning involves creating a new name for the product, some tweaking of its existing features, and finding new influencers—”affiliates” in the case of RaaS operations—to use (and market) the product. In addition, threat actors would initially limit the new product’s availability and follow with a brand-new marketing campaign—all without touching the product standard. In hindsight, it seems the GandCrab team has taken this route.
A month before the GandCrab retirement announcement, Cisco Talos researchers released information about their discovery of Sodinokibi. Attackers manually infected the target server after exploiting a zero-day vulnerability in its Oracle WebLogic application.
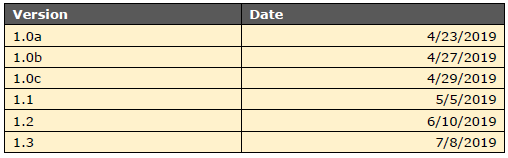
To date, six versions of Sodinokibi has been seen in the wild.
Sodinokibi infection vectors
Like GandCrab, the Sodinokibi ransomware follows an affiliate revenue system, which allows other cybercriminals to spread it through several vectors. Their attack methods include:
- Active exploitation of a vulnerability in Oracle WebLogic, officially named CVE-2019-2725
- Malicious spam or phishing campaigns with links or attachments
- Malvertising campaigns that lead to the RIG exploit kit, an avenue that GandCrab used before
- Compromised or infiltrated managed service providers (MSPs), which are third-party companies that remotely manage the IT infrastructure and/or end-user systems of other companies, to push the ransomware en-masse. This is done by accessing networks via a remote desktop protocol (RDP) and then using the MSP console to deploy the ransomware.
Although affiliates used these tactics to push GandCrab, too, many cybercriminals—nation-state actors included—have done the same to push their own malware campaigns.
Symptoms of Sodinokibi infection
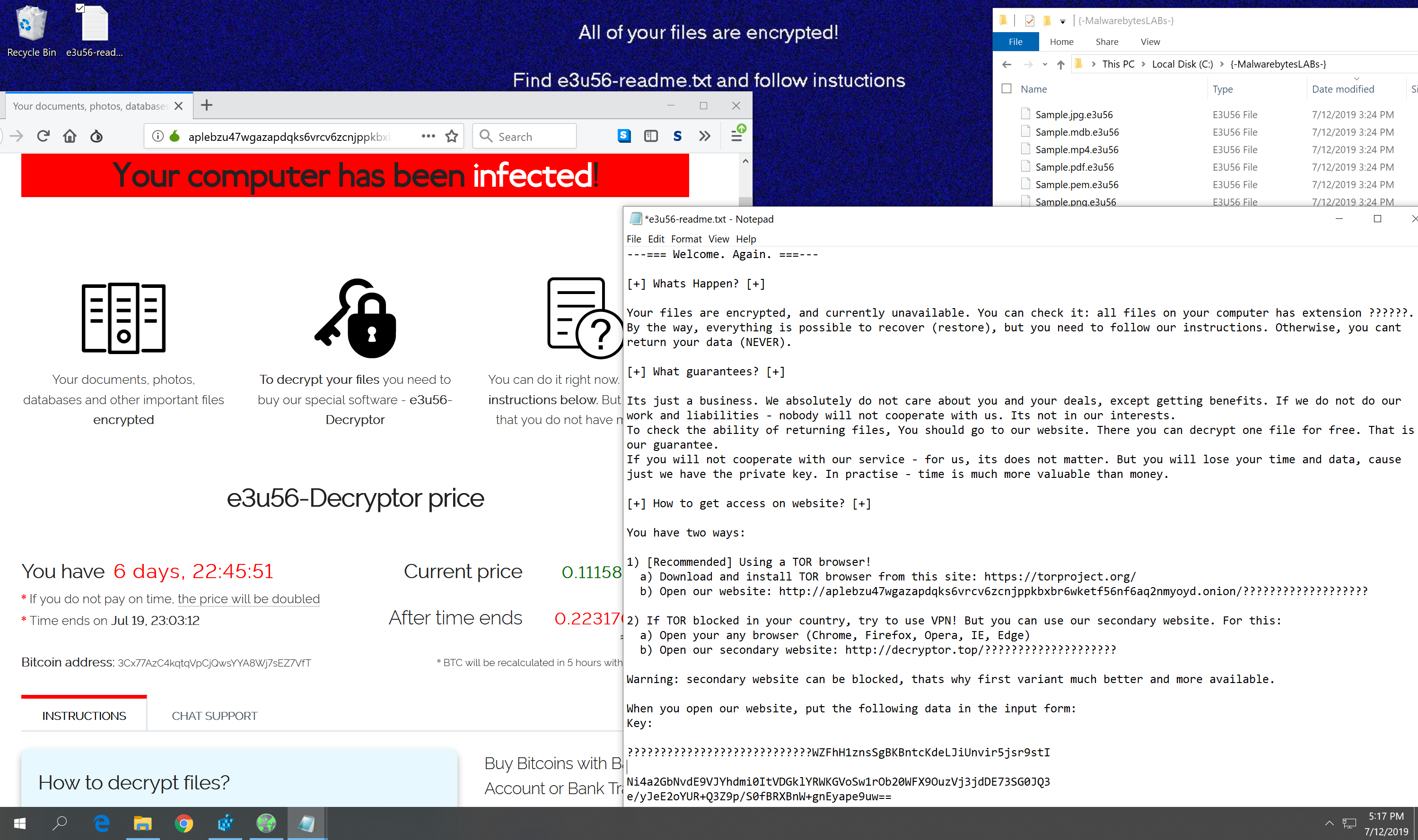
Systems infected with Sodinokibi ransomware show the following symptoms:
Changed desktop wallpaper. Like any other ransomware, Sodinokibi changes the desktop wallpaper of affected systems into a notice, informing users that their files have been encrypted. The wallpaper has a blue background, as you can partially see from the screenshot above, with the text:
All of your files are encrypted!
Find {5-8 alpha-numeric characters}-readme.txt and follow instructions
Presence of ransomware note. The {5-8 alpha-numeric characters}-readme.txt file it’s referring to is the ransom note that comes with every ransomware attack. In Sodinokibi’s case, it looks like this:
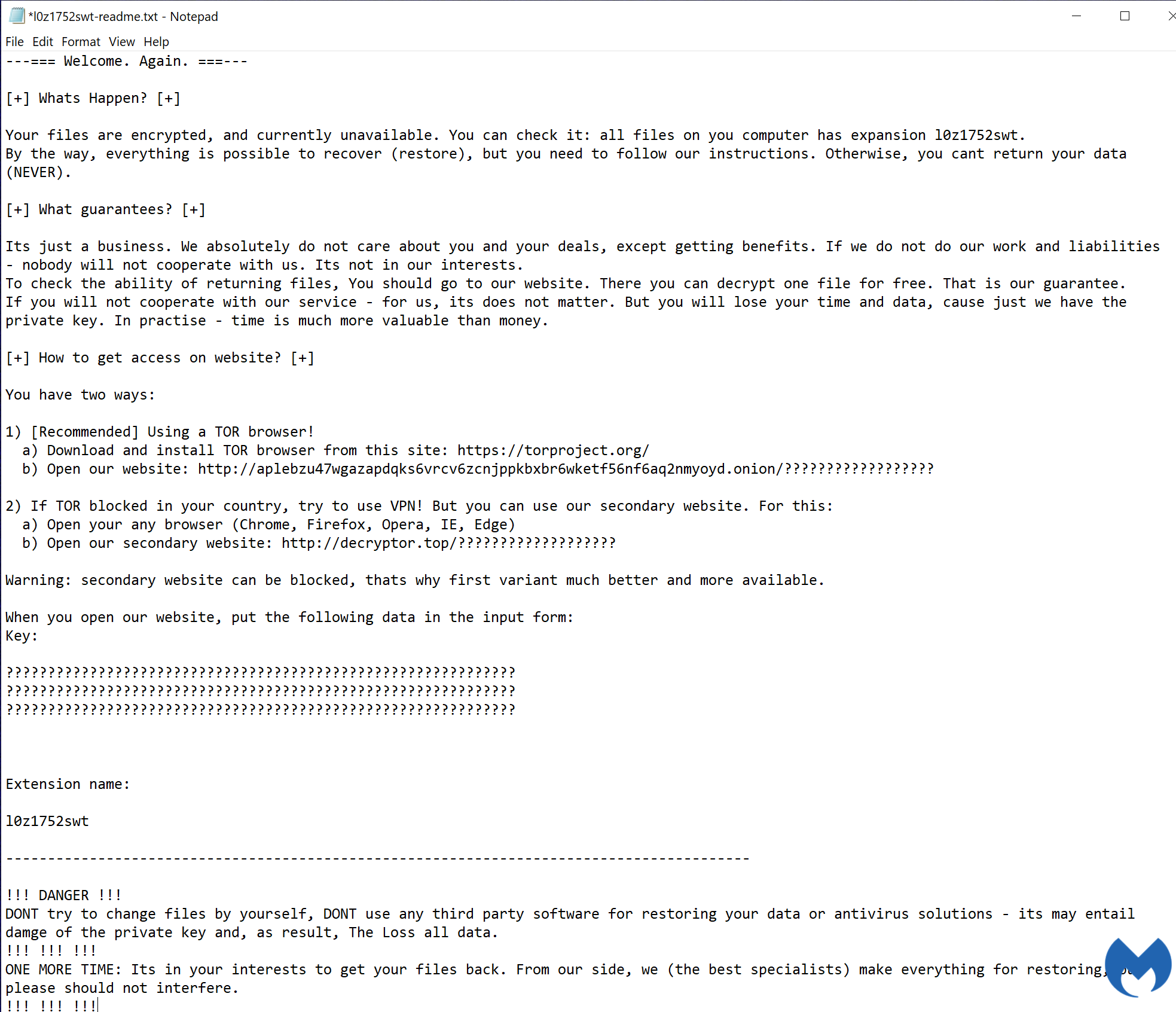
The note contains instructions on how affected users can go about paying the ransom and how the decryption process works.
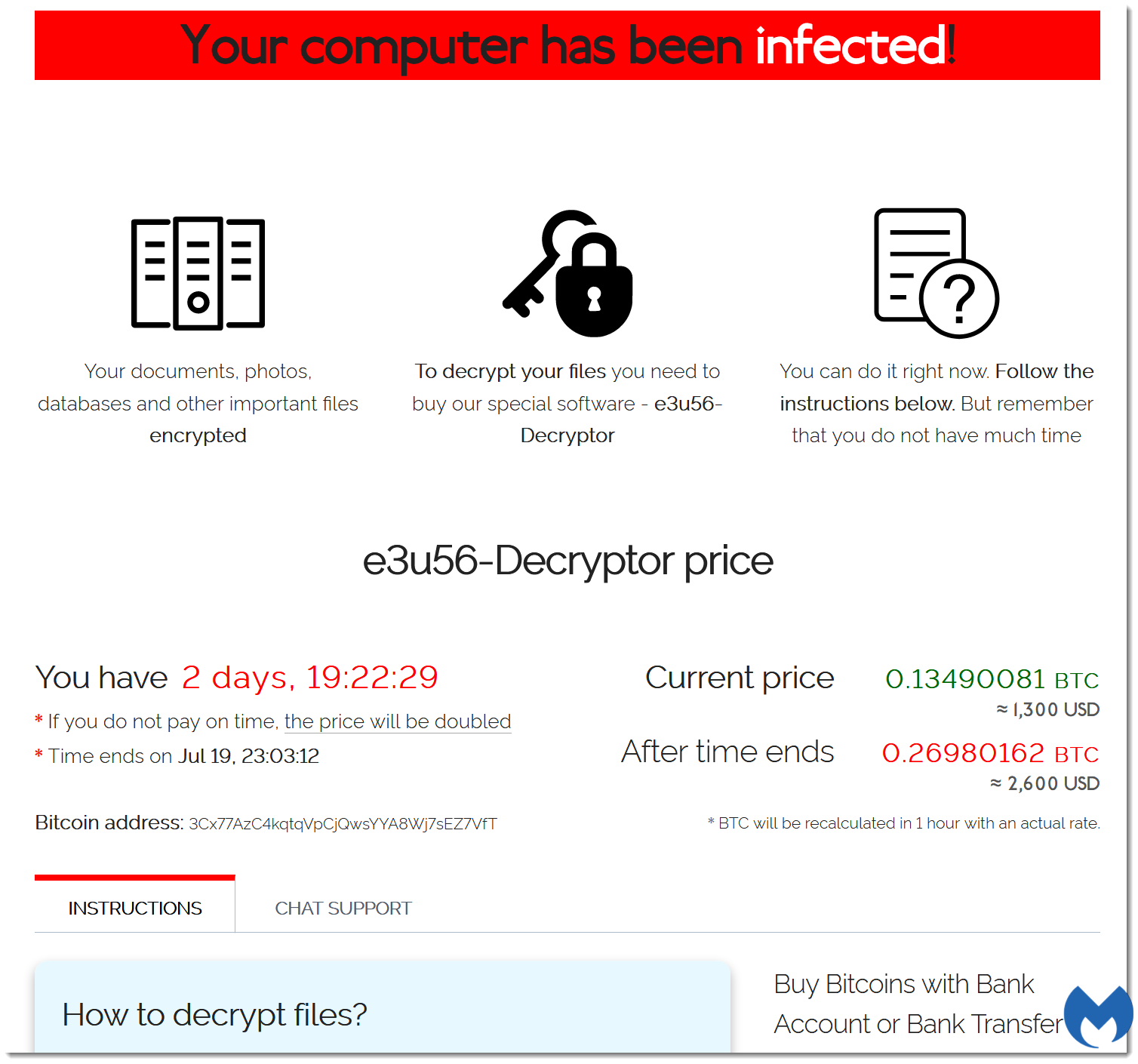
Encrypted files with a 5–8 character extension name. Sodinokibi encrypts certain files on local drives with the Salsa20 encryption algorithm, with each file renamed to include a pre-generated, pseudo-random alpha-numeric extension that’s five to eight characters long.
The extension name and character string included in the ransom note file name are the same. For example, if Sodinokibi has encrypted an image file and renamed it to paris2017.r4nd01, its corresponding ransom note will have the file name r4nd01-readme.txt.
Sodinokibi looks for files that are mostly media- and programming-related, with the following extensions to encrypt:
- .jpg
- .jpeg
- .raw
- .tif
- .png
- .bmp
- .3dm
- .max
- .accdb
- .db
- .mdb
- .dwg
- .dxf
- .cpp
- .cs
- .h
- .php
- .asp
- .rb
- .java
- .aaf
- .aep
- .aepx
- .plb
- .prel
- .aet
- .ppj
- .gif
- .psd
Deleted shadow copy backups and disabled Windows Startup Repair tool. Shadow copy (also known as Volume Snapshot Service, Volume Shadow Copy Service, or VSS) and Startup Repair are technologies inherent in the Windows OS. The former is “a snapshot of a volume that duplicates all of the data that is held on that volume at one well-defined instant in time,” according to the Windows Dev Center. The latter is a recovery tool used to troubleshoot certain Windows problems.
Deleting shadow copies prevents users from restoring from backup when they find their files are encrypted by ransomware. Disabling the Startup Repair tool prevents users from attempting to fix system errors that may have been caused by a ransomware infection.
Other tricks up Sodinokibi’s sleeve
Ransomware doesn’t normally take advantage of zero-day vulnerabilities in their attacks—but Sodinokibi is not your average ransomware. It takes advantage of an elevated privilege zero-day vulnerability in the Win32k component file in Windows.
Designated as CVE-2018-8453, this flaw can grant Sodinokibi administrator access to the endpoints it infects. This means that it can conduct the same tasks as administrators on systems, such as disabling security software and other features that were meant to protect the system from malware.
CVE-2018-8453 was the same vulnerability that the FruitArmor APT exploited in its malware campaign last year.
New variants of Sodinokibi have also been found to use “Heaven’s Gate,” an old evasion technique used to execute 64-bit code on a 32-bit process, which allows malware to run without getting detected. We touched on this technique in early 2018 when we dissected an interesting cryptominer we captured in the wild.
Protect your system from Sodinokibi
Malwarebytes tracks Sodinokibi campaigns and protects premium consumer users and business users with signature-less detection, nipping the attack in the bud before the infection chain even begins. Users of our free version are not protected from this threat without real-time protection.
We recommend consumers take the following actions if they are not premium Malwarebytes customers:
- Create secure backups of your data, either on an external drive or on the cloud. Be sure to detach your external drive from your computer once you’ve saved all your information, as it, too, could be infected if still connected.
- Run updates on all your systems and software, patching for any vulnerabilities.
- Be aware of suspicious emails, especially those that contain links or attachments. Read up on how to detect phishing attempts both on your computer and your mobile devices.
To mitigate on the business side, we also recommend IT administrators to do the following:
- Deny public IPs access to RDP port 3389.
- Replace your company’s ConnectWise ManagedITSync integration plug-in with the latest version before reconnecting your VSA server to the Internet.
- Block SMB port 445. In fact, it’s sound security practice to block all unused ports.
- Apply the latest Microsoft update packages.
- In this vein, make sure all software on endpoints is up-to-date.
- Limit the use of system administration tools to IT personnel or employees who need access only.
- Disable macro on Microsoft Office products.
- Regularly inform employees about threats that might be geared toward the organization’s industry or the company itself with reminders on how to handle suspicious emails, such as avoiding clicking on links or opening attachments if they’re not sure of the source.
- Apply attachment filtering to email messages.
- Regularly create multiple backups of data, preferably to devices that aren’t connected to the Internet.
Indicators of compromise (IOCs)
File hashes:
- e713658b666ff04c9863ebecb458f174
- bf9359046c4f5c24de0a9de28bbabd14
- 177a571d7c6a6e4592c60a78b574fe0e
Stay safe, everyone!










