Short bio
Browser Helper Objects (BHOs) are add-ons or plugins designed for Microsoft’s Internet Explorer (IE). Designed to enable COM objects to be written that will load with the browser (both IE and Windows Explorer), BHOs were a means to enhance the functionality of the browser. Their first use was to add toolbars to the browser windows.
Although these objects are usually dll files, we have also seen dat and exe files. The unrestricted access that BHOs have by design in IEs Document Object Model make them a powerful tool in the hands of attackers. In the Windows registry, the BHOs are registered by globally unique identifiers called CLSIDs under the key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects. There the CLSIDs are sub-keys that enumerate the BHOs in use on that system.
History
BHOs were first introduced with the release of IE4 near the end of 1997. Although there were and are many legitimate applications using BHOs, soon a host of Potentially Unwanted Programs (PUPs) followed in their wake. Adware distributors soon found ways to sell the public toolbars that gave the user some extra functionality for the price of looking at some advertisements. As with other adware applications, the rewards for the user have diminished and the amount of advertisements has grown since then. Knowing that BHOs can also monitor the traffic in the browser, you may not be surprised to learn that there have also been key-loggers and other spyware applications in the form of BHOs.
The add-on manager in IE that allows users to easily review and disable/enable extensions was introduced with IE 6 Service Pack 2. Before that introduction, BHOs that did not make any visible changes to the browser window often went unnoticed for a long time.
With the rise in popularity of other browsers and the introduction of Edge, which does not support BHOs, we may be at a point in history where the number of BHOs will start to fall.
Common infection method
Most BHOs get installed by the user, although the distributor may not always have been completely honest about what they do. As for the potentially unwanted BHOs, these are often offered as “specialized” toolbars that contain links to different sites offering competing services. For example, the toolbars might point to six or seven places where you can compress and decompress files, or offer to save you money by comparing prices at different sites or by finding you coupons. Others offer search engines, promise to show videos in HD quality or to give you free access to game portals.
Bundled installers are another common way to get infected with unsolicited BHOs. These bundles are designed to install more than the user bargained for and usually include one or more BHOs that function as adware and/or hijackers.
Associated families
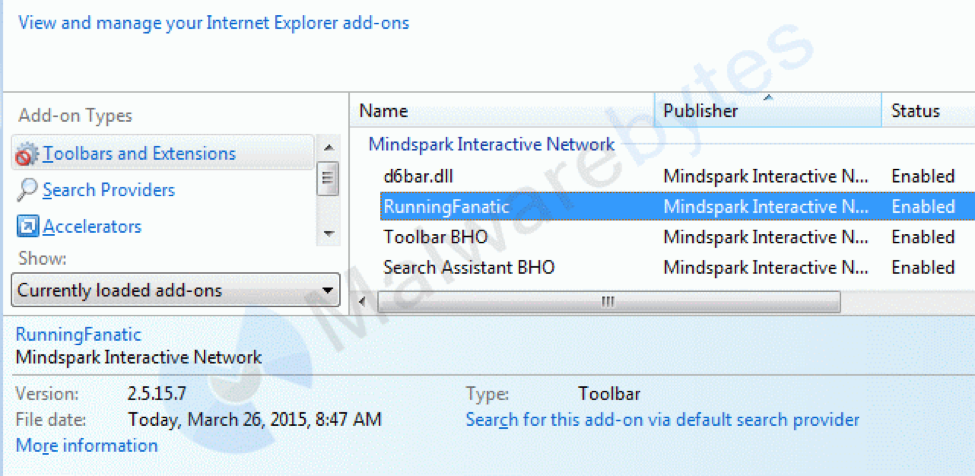
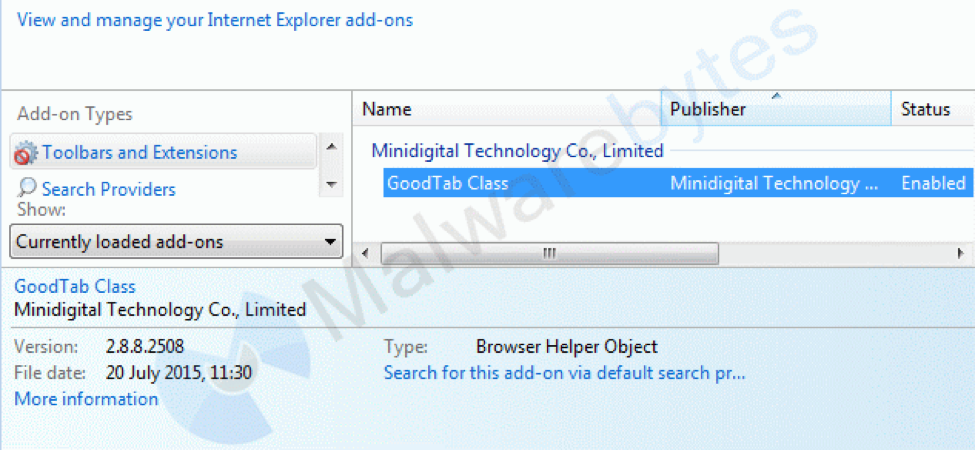
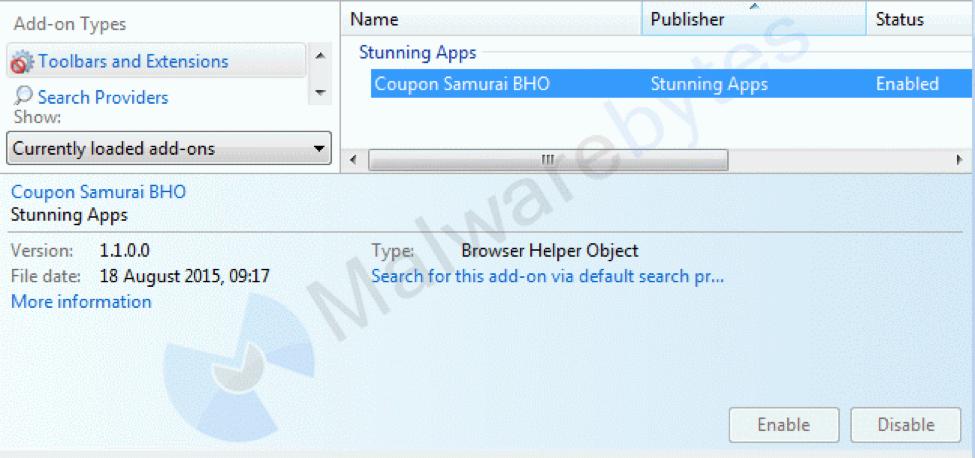
Very common BHOs of the potentially unwanted kind are from the families Mindspark/Ask (toolbars), Browsefox aka Sanbreel (bundled adware), Crossrider (bundled adware), and Conduit/SearchProtect (hijackers).
Remediation
PUPs can usually be removed with the built-in uninstaller, but sometimes this fails or the BHO is left behind. With the introduction of the Add-on Manager in IE, it has become easy to disable BHOs. To avoid getting disabled, they are sometimes given names that put you on the wrong foot. To counter this, there are many online resources where BHOs can be researched by name, filename, or CLSID if you are in doubt.
Aftermath
In cases of spyware and key-loggers, it may be necessary to change the passwords that you have used, since they may have been compromised. This is not limited to the ones you use online, since BHOs also hook into Windows Explorer.
Incomplete removal of a BHO can lead to browser instability, conflicts, and crashes, not only in IE but in Windows Explorer as well (which can be very annoying as you are left without your taskbar).
Avoidance
Be picky about what you install and where to get your installers. Whenever possible download the installers directly from the publisher’s site. Read the EULA and be extra careful when none is offered. Understanding how the software makes money for the publisher can be a good deciding factor for installing it.