Short bio
DDOS, or Distributed Denial of Service tools, are malicious applications designed to mount an attack against a service or website with the intention overwhelming it with false traffic and/or fake requests. This has the desired effect of tying up all available resources dealing with these requests, effectively denying access to legitimate users.
History
These tools were created originally for online extortion, but have also been used in online hooliganism and politically motivated hacking (hacktivism).
Common infection methods
Infection methods vary. Some DDOS tools rely on infected hosts who are centrally controlled and participate in the distributed denial of service without their knowledge, such as drones in a botnet. Others willingly install the DDOS application and rely on amplification mechanisms or other like-minded individuals to mount attacks to cripple their intended victims.
Removal
Stand-alone DDOS programs can be removed by uninstalling the application from the add/remove or programs and features, or deleting them if they do not use a standard installer. Drones in a botnet require disinfection from the original infection with an anti-malware solution.
Aftermath
Voluntary participation in a DDOS attack can lead to criminal charges. Involuntary participation could lead to Internet provider sanctions.
Avoidance
Good computer hygiene, prompt patching and update regimen, and using a defense-in-depth philosophy, including an antivirus and an anti-malware product with regular complete scans should keep most threats at bay that would enroll your PC in a botnet that has DDOS capabilities. Explore alternative ways of expressing political dissent other than through the use of DDOS applications.
Example
Low Orbit Ion Cannon (LOIC)
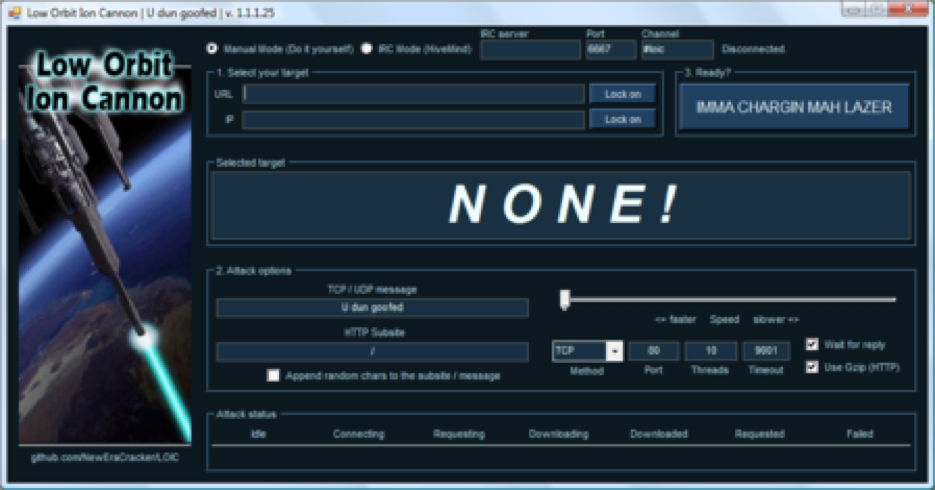
Low Orbit Ion Cannon (LOIC) is an open source network stress testing and denial-of-service attack application written in C#. LOIC was initially developed by Praetox Technologies, but was later released into the public domain, and now is hosted on several open source platforms.

Trojanbotnet.com control panel where drones can be instructed to perform DDOS attacks.
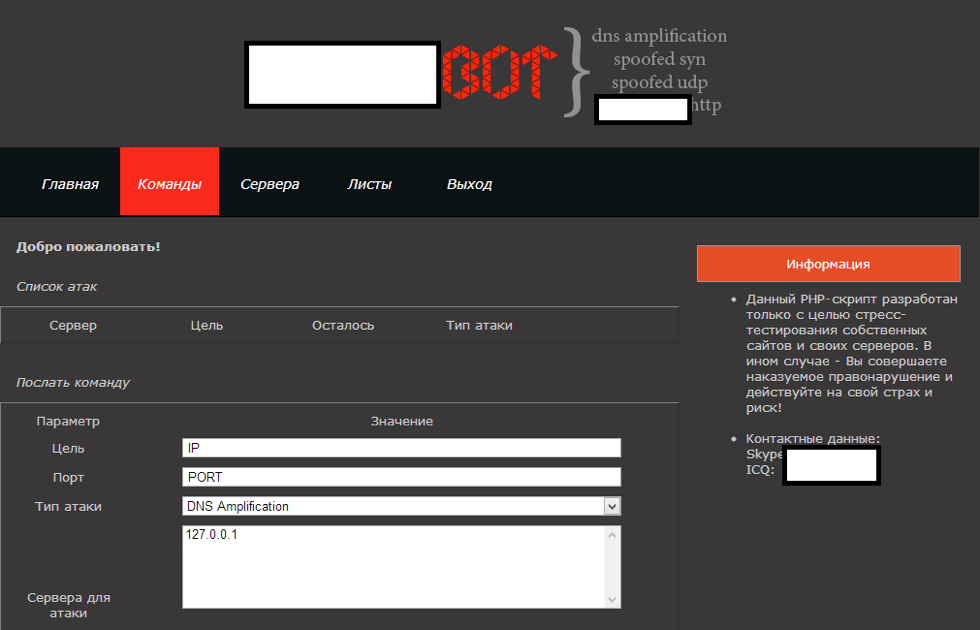
Example of a DNS amplification control panel used to perform DDOS attacks.




