Short bio
These Trojans use the SMS (text) messaging services of a mobile device to send and intercept messages. The user is usually unaware of the behavior.
History
SMS Trojans have been around since mobile devices have become mainstream. With mobile devices being small and users not being able to see activity, these behaviors can run behind the scenes.
Common infection method
Infection occurs when an app with malicious code is installed. These apps vary from legitimate apps recompiled with malcode, straight up malicious apps with a fake name, and apps with fake download links.
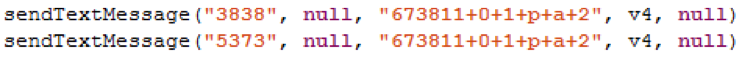
The SMS messages are typically sent without the user’s knowledge and have a fee associated with them. The fee comes in the form of shortcode messages tied to services the malware author has signed up for, like “56789.” The victim is usually unaware the message has been sent.
Android example:
Associated families
- Trojan.SMS.FakeInst
- Trojan.SMS.Agent
- Trojan.SMS.Rufraud
- Trojan.SMS.Opfake
- Trojan.SMS.Boxer
Remediation
These apps can be uninstalled using the mobile device’s uninstall functionality, the tricky part is identifying the offending behavior and app. That is where anti-malware software can help by identifying and removing these apps.
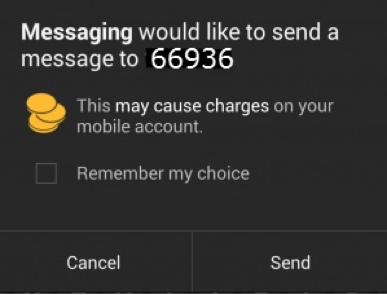
Google added warning functionality for these shortcode messages in later versions of KitKat on Android. This added protection will help warn a user before the message is sent.
Aftermath
Users can expect to see unexpected charges on their phone bill or be signed up for premium services they did not expect.
Avoidance
Stick to trusted sources for mobile apps and pay attention to those that request SMS permissions.




