Recently, we uncovered a new DNS-changer called Extenbro that comes with an adware bundler. These DNS-changers block access to security-related sites, so the adware victims can’t download and install security software to get rid of the pests.
From our viewpoint, this might be like sending in an elephant to save the mosquito, but the threat actors behind this attack have been known to use aggressive tactics in the past. What do they care if they open up your machine to all kinds of threats by disallowing you access to security sites and blocking any existing security software from getting updates? They just want to serve you adware.
Unfortunately, we have seen this kind of behavior before. But since this one uses a few fancy tricks, we’ll give you a quick overview of what it does and how you can get rid of it. For those just looking for a quick fix, there is a removal guide on our forums.
Infection vector
We have noticed the Extenbro Trojan is delivered on systems by a bundler that is detected by Malwarebytes as Trojan.IStartSurf.
DNS-changer
First and foremost, the Trojan changes the DNS settings of the infected system so it won’t be able to reach any security vendors’ sites.
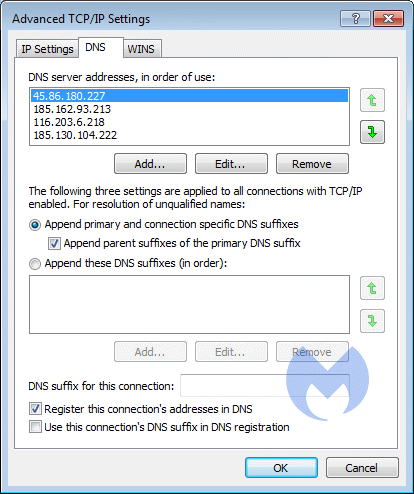
New for this one is that you have to access the Advanced DNS tab to find out that it has added four DNS servers rather than the usual two. Where people might be inclined to change the two that are visible, use the Advanced button and look at the DNS tab: It would cause them to leave the additional two behind.
Task Scheduler
Should you manage to correct the offending DNS servers and reboot the system before taking further measures, you will find that the DNS settings re-appear after a reboot. This is because of a randomly-named Scheduled Task that looks similar to this:
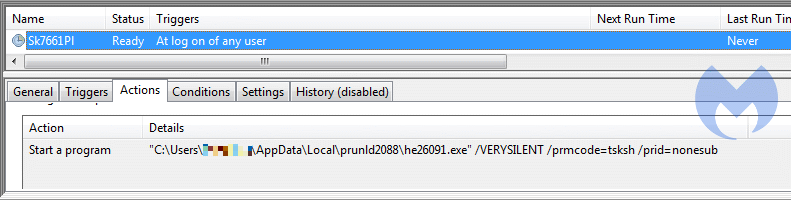
The location of the folder and the switches for the command seem to be fixed, but the folder name and file name are random.
Root certificate
The Trojan also adds a certificate to the set of Windows Root certificates.
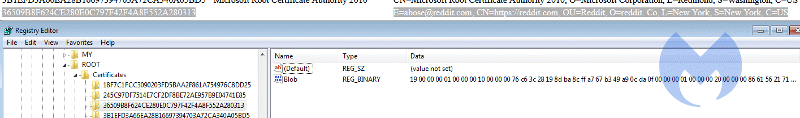
Using the method outlined in the blog post Learning PowerShell: some basic commands, I established that the certificate has no “Friendly Name” and is supposedly registered to abose[at]reddit[dot]com.
Disables IPV6
By changing the registry value DisabledComponents under the key HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservicesTCPIP6Parameters and setting the value to “FF”, the Trojan disables IPV6 to force the system to use the new DNS servers.
User.js
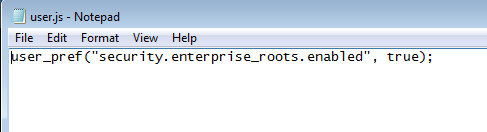
The malware also makes a change in the Firefox user.js file and sets the security.enterprise_roots.enabled setting to true, which Configures Firefox to use the Windows Certificate Store where the newly-added root certificate was added.
Removal instructions
Some of the changes that this malware makes could already be in place, if they are the user’s preferred settings. So feel free to skip the steps that you are not comfortable with.
What really needs to be done so you can download a removal tool or update you existing security software is to restore the DNS servers to what they were—or, if you don’t know the previous settings, to something safe. Most ISPs have the preferred DNS servers listed in their installation instructions or on their website. That is the first place to look. If you can’t find them there, you can use the DNS servers provided by OpenDNS. You can find instructions for many Operating Systems on their site.
An extra step needs to be taken when you are in this screen:
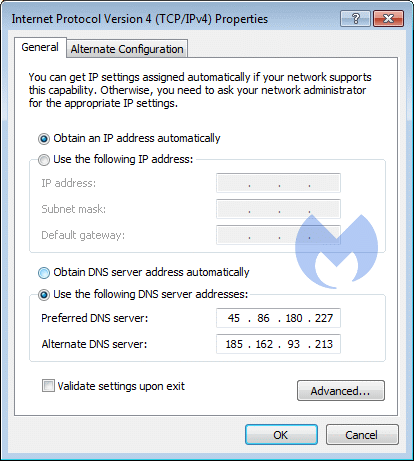
Make sure to click on Advanced…and select the DNS tab to find the extra two DNS servers that we mentioned earlier. Remove those before you change the two shown on the screen to your preferred ones.
Now, you should be able to visit security sites again. Follow the remaining instructions below:
- To get to your security sites, you may need a restart of the browser. Do NOT reboot your system or the DNS servers might be changed for the worse again by the Scheduled Task that belongs to the Trojan. If your existing solution does not pick up on the malware, download Malwarebytes to your desktop.
- Double-click mb3-setup-consumer-{version}.exe and follow the prompts to install the program.
- Then click Finish.
- Once the program has fully updated, select Scan Now on the Dashboard. Or select the Threat Scan from the Scan menu.
- If another update of the definitions is available, it will be implemented before the rest of the scanning procedure.
- When the scan is complete, make sure that All Threats are selected, and click Remove Selected.
- Restart your computer when prompted to do so.
- This procedure should take care of the Scheduled Task and the Root certificate.
- If you want to undo the change that makes FireFox adhere to the Windows certificates, you can open Firefox and type about:config in the address bar. Then read and accept the “risk” and search for security.enterprise_roots.enabled. The default settings is false. You can change the setting by selecting the line and right clicking it to get a menu. Clicking Toggle changes the value back and forth between True and False. Close the about:config tab when you are done.
Should you need further help, feel free to reach out to us on the forums or by contacting our support department.
IOCs
DNS servers:
45.86.180.227
185.162.93.213
116.203.6.218
185.130.104.222
Installer:
SHA256 b2a28e9abb04a5926d53850623b1f3c6738169b27847e90c55119f2836c17006
Root certificate:
36509B8F624CE280E0C797F42F4A8F552A280313
Stay safe, everyone!











